
prowler
Prowler is an Open Source Security tool for AWS, Azure, GCP and Kubernetes to do security assessments, audits, incident response, compliance, continuous monitoring, hardening and forensics readiness. Includes CIS, NIST 800, NIST CSF, CISA, FedRAMP, PCI-DSS, GDPR, HIPAA, FFIEC, SOC2, GXP, Well-Architected Security, ENS and more
APACHE-2.0 License
Bot releases are visible (Hide)
Published by toniblyx over 1 year ago
Drawn by quest for fire
They searched all through the land
Drawn by quest for fire
Discovery of man.
Quest for Fire is a song part of Piece of Mind album of Iron Maiden. This new version is the result of our quest for your security issues and our quest to help you to improve your cloud security posture. See below the amazing new features we have added to Prowler 3.2.0 🔥Quest for Fire🔥
New features to highlight in this version:
🏷️ Tag-based scan: now you can scan only resources with specific tags across your entire account with the following command:
prowler aws --resource-tags Environment=dev Project=prowler- You can use as many tags as you need. More information here: https://docs.prowler.cloud/en/latest/tutorials/aws/tag-based-scan/
🎯 Resource-based scan: now you can scan only a specific resources by the ARN
prowler aws --resource-arn arn:aws:iam::012345678910:user/test arn:aws:ec2:us-east-1:123456789012:vpc/vpc-12345678- That command will run all IAM user related checks to
testand all VPC related checks to VPCvpc-12345678 - This is very helpful for new found resources or even pipelines! More information here: https://docs.prowler.cloud/en/latest/tutorials/aws/resource-arn-based-scan/
⚖️ 17 New Security Compliance Frameworks: we added 17 new security frameworks for AWS.
- In addition to CIS 1.4, CIS 1.5 and Spanish ENS (that comes with more enhancements) we have added the following security frameworks for the AWS provider.
- CISA Cyber Essentials
- FedRAMP Low Revision 4
- FedRAMP Moderate Revision 4
- Federal Financial Institutions Examination Council (FFIEC)
- AWS Foundational Security Best Practices
- General Data Protection Regulation (GDPR)
- GxP 21 CFR Part 11
- GxP EU Annex 11
- HIPAA
- NIST 800-171 Revision 2
- NIST 800-53 Revision 4
- NIST 800-53 Revision 5
- NIST Cybersecurity Framework (CSF) v1.1
- PCI v3.2.1
- RBI Cyber Security Framework
- SOC 2
- These can be considered test mode at this point, we are open for feedback and updates.
- More information about how to use them with Prowler and compliance here: https://docs.prowler.cloud/en/latest/tutorials/compliance/.
- We want to thank @pedromarting3 for his contribution, AWS and their public documentation and also steampipe.io mod page https://hub.steampipe.io/mods/turbot/aws_compliance because they were pretty helpful for us. 🙏🏼 🤜🏼🤛🏼
✅New check:
- Check if IAM Access Analyzer is enabled (in addition of the existing one that looks for issues as well)
📺Handler for output code:
- Like in v2, now you can handle what output code to get when Prowler gets failed findings. (-z)
📄Allow list feature now supports Lambda to manage it:
- More information https://github.com/prowler-cloud/prowler/pull/1793
What's Changed:
- feat(compliance): Add 17 new security compliance frameworks for AWS by @pedromarting3 in https://github.com/prowler-cloud/prowler/pull/1824
- feat(new check): add accessanalyzer_enabled check by @sergargar in https://github.com/prowler-cloud/prowler/pull/1864
- feat(boto3-config): Use standard retrier by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1868
- feat(allowlist): AWS Lambda function support by @pplu in https://github.com/prowler-cloud/prowler/pull/1793
- feat(scan-type): AWS Resource ARNs based scan by @sergargar in https://github.com/prowler-cloud/prowler/pull/1807
- feat(exit_code 3): add -z option by @sergargar in https://github.com/prowler-cloud/prowler/pull/1848
- feat(scanner): Tag-based scan by @sergargar in https://github.com/prowler-cloud/prowler/pull/1751
Fixes:
- fix(elbv2): handle service for GWLB resources by @daftkid in https://github.com/prowler-cloud/prowler/pull/1860
- fix(checks): added validation for non-existing VPC endpoint policy by @daftkid in https://github.com/prowler-cloud/prowler/pull/1859
- fix(action): do not trigger action when editing release by @sergargar in https://github.com/prowler-cloud/prowler/pull/1865
- fix(key_errors): handle Key Errors in Lambda and EMR by @sergargar in https://github.com/prowler-cloud/prowler/pull/1871
- fix(permissive role assumption): actions list handling by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1869
- fix(key_errors): handle Key Errors in Lambda and EMR by @sergargar in https://github.com/prowler-cloud/prowler/pull/1871
- fix(hardware mfa): changed hardware mfa description by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1873
- fix(metadata): typo in appstream_fleet_session_disconnect_timeout.metadata.json by @sergargar in https://github.com/prowler-cloud/prowler/pull/1875
- fix(compliance): ENS RD2022 Spanish security framework updates by @alexr3y in https://github.com/prowler-cloud/prowler/pull/1809
- fix(errors): solve several services errors (AccessAnalyzer, AppStream, KMS, S3, SQS, R53, IAM, CodeArtifact and EC2) by @sergargar in https://github.com/prowler-cloud/prowler/pull/1879
- fix(cloudtrail_multi_region_enabled): reformat check by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1880
- chore(compliance): add manual checks to compliance CSV by @sergargar in https://github.com/prowler-cloud/prowler/pull/1872
- fix(service errors): solve errors in IAM, S3, Lambda, DS, Cloudfront services by @sergargar in https://github.com/prowler-cloud/prowler/pull/1882
- chore(Dockerfile): Remove build files by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1886
- fix(list_checks): filter checks after audit_info set by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1887
- fix(Azure_Audit_Info): Added audited_resources field by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1891
Documentation
- docs: Boto3 Standard Retrier by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1885
- docs: Update AWS Role Assumption by @Fennerr in https://github.com/prowler-cloud/prowler/pull/1890
- docs: Minor changes to the intro paragraph by @Fennerr in https://github.com/prowler-cloud/prowler/pull/1892
- docs: Minor changes to logging by @Fennerr in https://github.com/prowler-cloud/prowler/pull/1893
New Contributors
- @pedromarting3 made their first contribution in https://github.com/prowler-cloud/prowler/pull/1824
- @pplu made their first contribution in https://github.com/prowler-cloud/prowler/pull/1792
Full Changelog: https://github.com/prowler-cloud/prowler/compare/3.1.4...3.2.0
Published by jfagoagas over 1 year ago
Chores
- chore(regions_update): Changes in regions for AWS services. by @github-actions in https://github.com/prowler-cloud/prowler/pull/1812
- chore(issues): update bug_report.md by @toniblyx in https://github.com/prowler-cloud/prowler/pull/1844
- chore(security hub): improve securityhub_enabled check logic by @sergargar in https://github.com/prowler-cloud/prowler/pull/1851
- build(deps-dev): bump moto from 4.1.1 to 4.1.2 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1845
- build(deps-dev): bump sure from 2.0.0 to 2.0.1 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1847
- build(deps-dev): bump openapi-spec-validator from 0.5.4 to 0.5.5 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1846
- build(deps-dev): bump pylint from 2.16.0 to 2.16.1 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1823
Fixes
- fix(readme): correct PyPi download link by @sergargar in https://github.com/prowler-cloud/prowler/pull/1836
- fix(lambda-runtime): Init value must be empty string by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1837
- fix(errors): solve CloudWatch, KMS, EMR and OpenSearch service errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1843
- fix(kms): call GetKeyRotationStatus only for Customer Keys by @sergargar in https://github.com/prowler-cloud/prowler/pull/1842
- fix(checks): solve different errors in EFS, S3 and VPC by @sergargar in https://github.com/prowler-cloud/prowler/pull/1841
- fix(exit_code): change sys exit code to 1 in Critical Errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1853
- fix(iam): change prowler additional policy json due errors in creation by @theist in https://github.com/prowler-cloud/prowler/pull/1852
New Contributors
- @theist made their first contribution in https://github.com/prowler-cloud/prowler/pull/1852
Full Changelog: https://github.com/prowler-cloud/prowler/compare/3.1.3...3.1.4
Published by sergargar over 1 year ago
Chores
- chore(readme): add prowler PyPi stats by @sergargar in https://github.com/prowler-cloud/prowler/pull/1798
- chore(regions): Change feat to chore by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1805
- chore(regions_update): Changes in regions for AWS services. by @github-actions in https://github.com/prowler-cloud/prowler/pull/1812
- chore(logs): improve check error logs by @sergargar in https://github.com/prowler-cloud/prowler/pull/1818
- chore(audit metadata): retrieve audit metadata from execution by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1803
- build(deps-dev): bump pylint from 2.15.10 to 2.16.0 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1815
- build(deps-dev): bump openapi-spec-validator from 0.5.2 to 0.5.4 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1821
Fixes
- fix(kms): add symmetric condition to kms_cmk_rotation_enabled check by @sergargar in https://github.com/prowler-cloud/prowler/pull/1788
- fix(partition): add dynamic partition in CloudTrail S3 DataEvents checks by @sergargar in https://github.com/prowler-cloud/prowler/pull/1787
- fix(metadata): use docs.aws.amazon.com like other aws checks, not docs.amazonaws.cn by @ifduyue in https://github.com/prowler-cloud/prowler/pull/1790
- fix(allowlist): validate allowlist for any database format (file, dynamo, s3, etc) by @pplu in https://github.com/prowler-cloud/prowler/pull/1792
- fix(accessanalyzer_enabled_without_findings): fixed status findings by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1799
- fix(iam_policy_no_administrative_privileges): check only : permissions by @sergargar in https://github.com/prowler-cloud/prowler/pull/1802
- fix(iam_avoid_root_usage): correct date logic by @sergargar in https://github.com/prowler-cloud/prowler/pull/1801
- fix(ec2_securitygroup_not_used): ignore default security groups by @sergargar in https://github.com/prowler-cloud/prowler/pull/1800
- fix(accessanalyzer): no analyzers using pydantic by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1806
- fix(cloudtrail): improve cloudtrail_cloudwatch_logging_enabled status extended by @sergargar in https://github.com/prowler-cloud/prowler/pull/1813
- fix(KeyError): handle service key errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1819
- fix(metadata) fixed typo in title for awslambda_function_not_publicly… by @daftkid in https://github.com/prowler-cloud/prowler/pull/1826
- fix(KeyError): handle service key errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1831
- fix(cloudtrail): included advanced data events selectors by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1814
- fix(shub): update link to Security Hub documentation by @sergargar in https://github.com/prowler-cloud/prowler/pull/1830
- fix(awslambda_function_no_secrets_in_code): Retrieve Code if set by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1833
- fix(action): Build from release branch by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1834
- fix(errors): solve different errors in KMS, EFS and Lambda by @sergargar in https://github.com/prowler-cloud/prowler/pull/1835
New Contributors
- @ifduyue made their first contribution in https://github.com/prowler-cloud/prowler/pull/1790
- @pplu made their first contribution in https://github.com/prowler-cloud/prowler/pull/1792
- @daftkid made their first contribution in https://github.com/prowler-cloud/prowler/pull/1826
Full Changelog: https://github.com/prowler-cloud/prowler/compare/3.1.2...3.1.3
Published by sergargar over 1 year ago
Chores
- chore(contrib): Enables a new CloudFormation of CodeBuild for v3 by @sergargar in https://github.com/prowler-cloud/prowler/pull/1764
- chore(readme): Update pip package name, now
prowlerorprowler-cloudcan be used to install Prowler by @sergargar in https://github.com/prowler-cloud/prowler/pull/1768
Fixes
- fix(docs): Changed the azure subscription file text #HSFDPMUW by @Leon114m in https://github.com/prowler-cloud/prowler/pull/1749
- fix(inventory): update resource type for SQS and SNS by @vabagaria in https://github.com/prowler-cloud/prowler/pull/1747
- fix(metadata): solve metadata replace by @sergargar in https://github.com/prowler-cloud/prowler/pull/1755
- fix(iam): IAM status messages switched fail and pass text and some grammar by @acknosyn in https://github.com/prowler-cloud/prowler/pull/1756
- fix(iam): handle credential report errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1765
- fix(json): close Json correctly when no findings by @sergargar in https://github.com/prowler-cloud/prowler/pull/1773
- fix(apigatewayv2): correct apigatewayv2_access_logging_enabled check title by @sergargar in https://github.com/prowler-cloud/prowler/pull/1769
- fix(IAM): remove duplicate list_policies function by @sergargar in https://github.com/prowler-cloud/prowler/pull/1763
- fix(cloudtrail_multi_region_enabled): fixed region when no trails by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1774
- fix(severity): update severities for Security Hub, GuardDuty and NACL related checks by @sergargar in https://github.com/prowler-cloud/prowler/pull/1775
Docs
- docs(grammar): Improved grammar in the Documentation paragraph by @Ozan-Ekinci in https://github.com/prowler-cloud/prowler/pull/1776
- docs(grammar): Improved grammar in the AZ CLI / Browser / Managed Identity authentication paragraph by @Ozan-Ekinci in https://github.com/prowler-cloud/prowler/pull/1745
New Contributors
- @vabagaria made their first contribution in https://github.com/prowler-cloud/prowler/pull/1747
Full Changelog: https://github.com/prowler-cloud/prowler/compare/3.1.1...3.1.2
Published by sergargar over 1 year ago
Chores
- chore(release): add PyPi GitHub Action by @sergargar in https://github.com/prowler-cloud/prowler/pull/1724
- chore(regions_update): Changes in regions for AWS services. by @github-actions in https://github.com/prowler-cloud/prowler/pull/1730
- chore(dispatch): dispatch triggered actions by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1739
- chore(code-ql): Include security linter by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1703
Fixes
- fix(arguments): improve quiet option by @sergargar in https://github.com/prowler-cloud/prowler/pull/1723
- fix(allowlist): add yaml structure validator by @sergargar in https://github.com/prowler-cloud/prowler/pull/1735
- fix(pipeline): fixed typo in main pipeline by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1740
- fix(rds): remove DocumentDB from RDS by @sergargar in https://github.com/prowler-cloud/prowler/pull/1737
- fix(actions): Exclude docs folder in action by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1743
- fix(IAM): add missing permissions for Prowler by @sergargar in https://github.com/prowler-cloud/prowler/pull/1731
- fix(allowlist): remove re.escape by @sergargar in https://github.com/prowler-cloud/prowler/pull/1734
- fix(lambda): solve lambda errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1732
- fix(pypi): replicate package to have Prowler in PyPi by @sergargar in https://github.com/prowler-cloud/prowler/pull/1727
Docs
- docs(mapping): add mapping of v2 to v3 checks and update pip package name by @toniblyx in https://github.com/prowler-cloud/prowler/pull/1742
Full Changelog: https://github.com/prowler-cloud/prowler/compare/3.1.0...3.1.1
Published by toniblyx almost 2 years ago
"The swords of scorn divide,
Take not thy thunder from us,
But take away our pride."
Revelations is the second song of the Peace of Mind album of Iron Maiden that was written by Bruce Dickinson.
This last month has been a real revelation for us and we realize how big is our community and how well accepted has been version 3. We have passed the number of 2 Million of downloads 🚀 since the project started (not counting forks). As a reference see OSS Insight stats in the last month https://ossinsight.io/collections/security-tool, we became the Top 1 tool thanks to all of you!
What's Changed:
New AWS check iam_role_cross_service_confused_deputy_prevention:
Ensure IAM Service Roles prevents against a cross-service confused deputy attack. Use the aws:SourceArn and aws:SourceAccount global condition context keys in trust relationship policies to limit the permissions that a service has to a specific resource. More information at https://docs.aws.amazon.com/IAM/latest/UserGuide/confused-deputy.html#cross-service-confused-deputy-prevention.
- feat(check): add iam_role_cross_service_confused_deputy_prevention check by @Fennerr and @sergargar in https://github.com/prowler-cloud/prowler/pull/1710
- feat(report): Support to custom report interface by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1702
- feat(ecs_task_definitions_no_environment_secrets): Update resource_id by @Fennerr in https://github.com/prowler-cloud/prowler/pull/1665
- feat(iam): Add IAM Role Class by @sergargar in https://github.com/prowler-cloud/prowler/pull/1709
- feat(only_logs): New logging flag to only show execution logs by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1708
- feat(regions_update): Changes in regions for AWS services by @github-actions
Fixes:
- fix(trustedadvisor_errors_and_warnings): add region by @sergargar in https://github.com/prowler-cloud/prowler/pull/1662
- fix(docs): Include a comma in the permissions paragraph #HSFDPMUW by @Leon114m in https://github.com/prowler-cloud/prowler/pull/1668
- fix(s3): Add S3 ResourceArn by @gabrielsoltz in https://github.com/prowler-cloud/prowler/pull/1666
- fix(shub): associate resource_arn as resourceId in Security Hub by @sergargar in https://github.com/prowler-cloud/prowler/pull/1672
- fix(compliance): Security Hub working with compliance by @sergargar in https://github.com/prowler-cloud/prowler/pull/1673
- fix(config): path error in Windows environment by @sergargar in https://github.com/prowler-cloud/prowler/pull/1684
- docs: Edit troubleshooting page by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1685
- fix: remove unnecessary print by @sergargar in https://github.com/prowler-cloud/prowler/pull/1686
- fix(services): Handle KeyErrors from AWS by @sergargar in https://github.com/prowler-cloud/prowler/pull/1690
- fix(path): aws_regions_by_service.json: FileNotFoundError[13] by @sergargar in https://github.com/prowler-cloud/prowler/pull/1689
- fix: deleted test exclusion in name loading checks by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1694
- fix(docs): Add security section and solve images location by @sergargar in https://github.com/prowler-cloud/prowler/pull/1696
- fix(cloudwatch_service): set default region in CloudWatch by @sergargar in https://github.com/prowler-cloud/prowler/pull/1693
- fix: VPC Key Error by @sergargar in https://github.com/prowler-cloud/prowler/pull/1695
- fix: Solve IAM policy Errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1692
- fix(quick_inventory): Prowler quick inventory for US GovCloud and China by @toniblyx in https://github.com/prowler-cloud/prowler/pull/1698
- fix(docs): correct permissions links by @sergargar in https://github.com/prowler-cloud/prowler/pull/1701
- fix(docs): Include a new comma in the Basic Usage paragraph #HSFDPMUW by @Leon114m in https://github.com/prowler-cloud/prowler/pull/1705
- fix(docs): Include multiple commas in the troubleshooting file #HSFDPMUW by @Leon114m in https://github.com/prowler-cloud/prowler/pull/1706
- fix(apigateway): Add ApiGateway ResourceArn and check fixes by @gabrielsoltz in https://github.com/prowler-cloud/prowler/pull/1707
- fix(ec2_elastic_ip_unassgined): Incorrect ResourceType for check ec2_elastic_ip_unassgined by @gabrielsoltz in https://github.com/prowler-cloud/prowler/pull/1711
- fix(action): add permissions to Github action by @sergargar in https://github.com/prowler-cloud/prowler/pull/1712
- fix(fill_html_overview_statistics): Handle if file exists by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1718
- fix(error): ecr_repositories_scan_vulnerabilities_in_latest_image report not found by @sergargar in https://github.com/prowler-cloud/prowler/pull/1719
- build(deps-dev): bump pytest from 7.2.0 to 7.2.1 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1715
- build(deps-dev): bump pylint from 2.15.9 to 2.15.10 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1676
- build(deps-dev): bump moto from 4.0.13 to 4.1.0 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1675
- build(deps-dev): bump coverage from 7.0.3 to 7.0.4 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1678
- build(deps-dev): bump vulture from 2.6 to 2.7 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1677
- build(deps-dev): bump coverage from 7.0.4 to 7.0.5 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1688
- build(deps-dev): bump openapi-spec-validator from 0.5.1 to 0.5.2 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1716
- docs: Placed a comma in the Service Principal authentication paragraph by @Ozan-Ekinci in https://github.com/prowler-cloud/prowler/pull/1713
- docs(SECURITY.md): Include Security Policy by @toniblyx in https://github.com/prowler-cloud/prowler/pull/1697
New Contributors:
- @Leon114m made their first contribution in https://github.com/prowler-cloud/prowler/pull/1668
- @Ozan-Ekinci made their first contribution in https://github.com/prowler-cloud/prowler/pull/1713
- @Fennerr made their first contributions in in https://github.com/prowler-cloud/prowler/pull/1665 and https://github.com/prowler-cloud/prowler/pull/1710
Full Changelog: https://github.com/prowler-cloud/prowler/compare/3.0.2...3.1.0
Published by jfagoagas almost 2 years ago
Features
- feat(regions_update): changes in regions for AWS services. by @github-actions in https://github.com/prowler-cloud/prowler/pull/1629 and https://github.com/prowler-cloud/prowler/pull/1646
- feat(aws-regions): update refresh regions action by @sergargar in https://github.com/prowler-cloud/prowler/pull/1641
- feat(ec2): add ResourceArn by @gabrielsoltz in https://github.com/prowler-cloud/prowler/pull/1649
- feat(ecs_task_definitions_no_environment_secrets): update recommendation by @Fennerr in https://github.com/prowler-cloud/prowler/pull/1658
- feat(ecs_task_definitions_no_environment_secrets): add ECS task revision number by @Fennerr in https://github.com/prowler-cloud/prowler/pull/1657
Fixes
- fix(typo): Prowler for Azure by @cclauss in https://github.com/prowler-cloud/prowler/pull/1619
- fix(output_filename): Use custom output filename when set by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1632
- fix(iam_user_mfa_enabled_console_access): password enabled issues by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1634
- fix(security-hub): apply -q to security hub by @sergargar in https://github.com/prowler-cloud/prowler/pull/1637
- fix(security): update pipfile.lock by @sergargar in https://github.com/prowler-cloud/prowler/pull/1639
- fix(dockerfile): Remove additional
apk updatein Dockerfile by @PeterDaveHello in https://github.com/prowler-cloud/prowler/pull/1617 - fix(actions): add Github Action
contents: writepermission by @sergargar in https://github.com/prowler-cloud/prowler/pull/1643 - fix(actions): add GH Action
pull-requests: writepermissions by @sergargar in https://github.com/prowler-cloud/prowler/pull/1644 - fix(codeartifact): set Namespace attribute as optional by @sergargar in https://github.com/prowler-cloud/prowler/pull/1648
- fix(assume-role): Refresh credentials when assuming role by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1636
- fix(glacier): handle no vault policy error by @sergargar in https://github.com/prowler-cloud/prowler/pull/1650
- fix(contrib): update contrib folder by @sergargar in https://github.com/prowler-cloud/prowler/pull/1635
Docs
- docs(AWS-Role): fixed typo by @eltociear in https://github.com/prowler-cloud/prowler/pull/1610
- docs(installation): add multiple ways to install prowler in tabs by @toniblyx in https://github.com/prowler-cloud/prowler/pull/1627
New Contributors
- @eltociear made their first contribution in https://github.com/prowler-cloud/prowler/pull/1610
- @cclauss made their first contribution in https://github.com/prowler-cloud/prowler/pull/1619
- @PeterDaveHello made their first contribution in https://github.com/prowler-cloud/prowler/pull/1617
Full Changelog: https://github.com/prowler-cloud/prowler/compare/3.0.1...3.0.2
Published by toniblyx almost 2 years ago
Fixes
- fix(logs): add check_name to logs by @sergargar in https://github.com/prowler-cloud/prowler/pull/1574
- test(credential_report): Improve credential report tests by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1579
- build(deps-dev): bump coverage from 6.5.0 to 7.0.0 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1568
- docs(links): Update broken links to permissions folder by @JonoB in https://github.com/prowler-cloud/prowler/pull/1584
- build(deps-dev): bump moto from 4.0.11 to 4.0.12 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1570
- build(deps-dev): bump pylint from 2.15.8 to 2.15.9 by @dependabot in https://github.com/prowler-cloud/prowler/pull/1569
- fix(errors): handle S3 errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1585
- fix(ECR): handle ECR errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1586
- fix(iam): handle NoSuchEntity error by @sergargar in https://github.com/prowler-cloud/prowler/pull/1589
- fix(vpc): endpoint policy error by @sergargar in https://github.com/prowler-cloud/prowler/pull/1588
- fix(list services): Solve list services issue by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1587
- fix(shub): Handle Security Hub InvalidAccessException error by @sergargar in https://github.com/prowler-cloud/prowler/pull/1590
- fix(efs): handle PolicyNotFound error by @sergargar in https://github.com/prowler-cloud/prowler/pull/1591
- fix(aws-cn partition): solve aws-cn partition errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1576
- feat(errors): prettify unknown service errors by @sergargar in https://github.com/prowler-cloud/prowler/pull/1592
- fix(sqs): get sqs encryption by @sergargar in https://github.com/prowler-cloud/prowler/pull/1596
- fix(refresh-aws-regions): Change branch by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1598
- fix(check_report): Init status field and fix stats output by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1580
- fix(send to s3): fixed send to s3 feature by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1599
- docs: Include Azure requirements in README by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1600
- fix(global_services): handle global regions correctly by @sergargar in https://github.com/prowler-cloud/prowler/pull/1594
- fix(output-filename): Handle argument by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1604
New Contributors
- @JonoB made their first contribution in https://github.com/prowler-cloud/prowler/pull/1584
Full Changelog: https://github.com/prowler-cloud/prowler/compare/3.0.0...3.0.1
Published by toniblyx almost 2 years ago
Today we are releasing a new major version of Prowler 🎉🥳🎊🍾, the Version 3 aka Piece of Mind.
Take Prowler v3 as our 🎄Christmas gift 🎁 for the Cloud Security Community.

Artwork property of Iron Maiden
Piece of Mind was the fourth studio album of Iron Maiden. Its meaning fits perfectly with what we do with Prowler in both senses: being protected and at the same time, this is the software I would have wanted to write when I started Prowler back in 2016 (this is now, more than ever, a piece of my mind). Now this has been possible thanks to my awesome team at Verica.
No doubt that 2022 has been a pretty interesting year for us, we launched ProwlerPro and released many minor versions of Prowler. Now enjoy Sun and Steel while you keep reading these release notes.
If you are an Iron Maiden fan as I am, you have noticed the latest minor release of Prowler (2.12) was a song from this very same album, just a clue of what was coming! In Piece of Mind you can find one of the most popular heavy metal songs of all times, The Trooper, which will be a Prowler version to be released during 2023.
Prowler v3 is more than a new version of Prowler, it is a whole new piece of software, we have fully rewritten it in Python and we have made it multi-cloud adding Azure as our second supported Cloud Provider. Prowler v3 is also way faster, being able to scan an entire AWS account across all regions 37 times faster than before, yes! you read it correctly, what before took hours now it takes literally few minutes or even seconds.
New documentation site:
We are also releasing today our brand new documentation site for Prowler at https://docs.prowler.cloud and it is also stored in the docs folder in the repo.
What's Changed:
Here is a list of the most important changes in Prowler v3:
- 🐍 Python: we got rid of all bash and it is now all in Python.
pip install prowlerthen runprowlerthat’s all. - 🚀 Faster: huge performance improvements.
Scanning the same account takes from 2.5 hours to 4 minutes. - 💻 Developers and Community: we have made it easier to contribute with new checks and new compliance frameworks. We also included unit tests and native logging features. And now the CLI supports long arguments and options.
- ☁️ Multi-cloud: in addition to AWS, we have added Azure.
- ✅ Checks and Groups: all checks are now more comprehensive and we provide resolution actions in most of them. Their ID is no longer tight to CIS but they are self-explanatory. Groups now are dynamically generated based on checks metadata like services, categories, severity and more).
- ⚖️ Compliance: we are including full support for CIS 1.4, CIS 1.5 and the new Spanish ENS in this release, more to come soon! Compliance also has its own output file with their own metadata and to create your own is easier than ever before making more comprehensive reports.
- 🧩 Compatibility with v2: most of the options are the same in this version in order to support backward compatibility however some options like assume role or AWS Organizations query are now different and easier to use.
- 🔄 Consolidated output formats: now both CSV and JSON reports come with the same attributes and compared to v2, they come with more than 40 values per finding. HTML, CSV and JSON are created every time you run
prowler. - 📊 Quick Inventory: introduced in v2, we have fine tuned the Quick Inventory feature and now you can get a list of all resources in your AWS accounts within seconds.
Prowler new default overview:
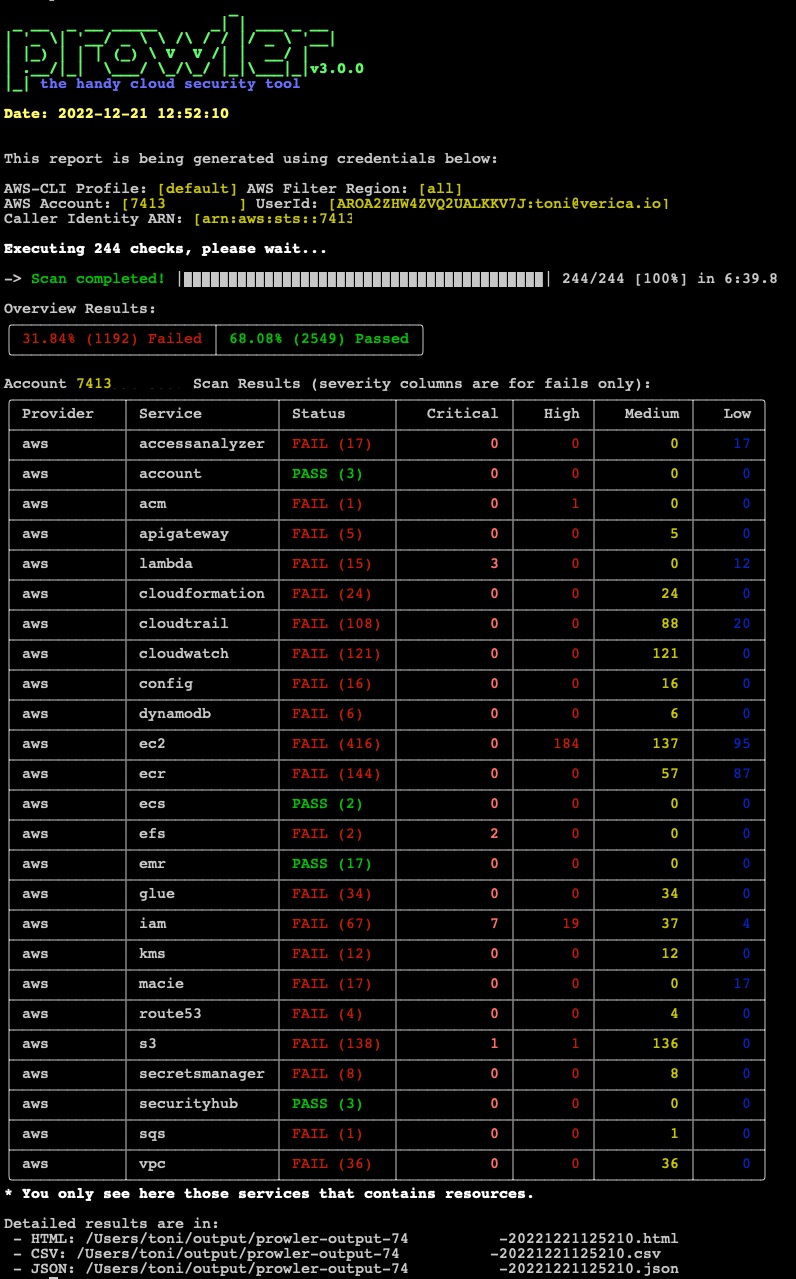
Prowler updated HTML report:
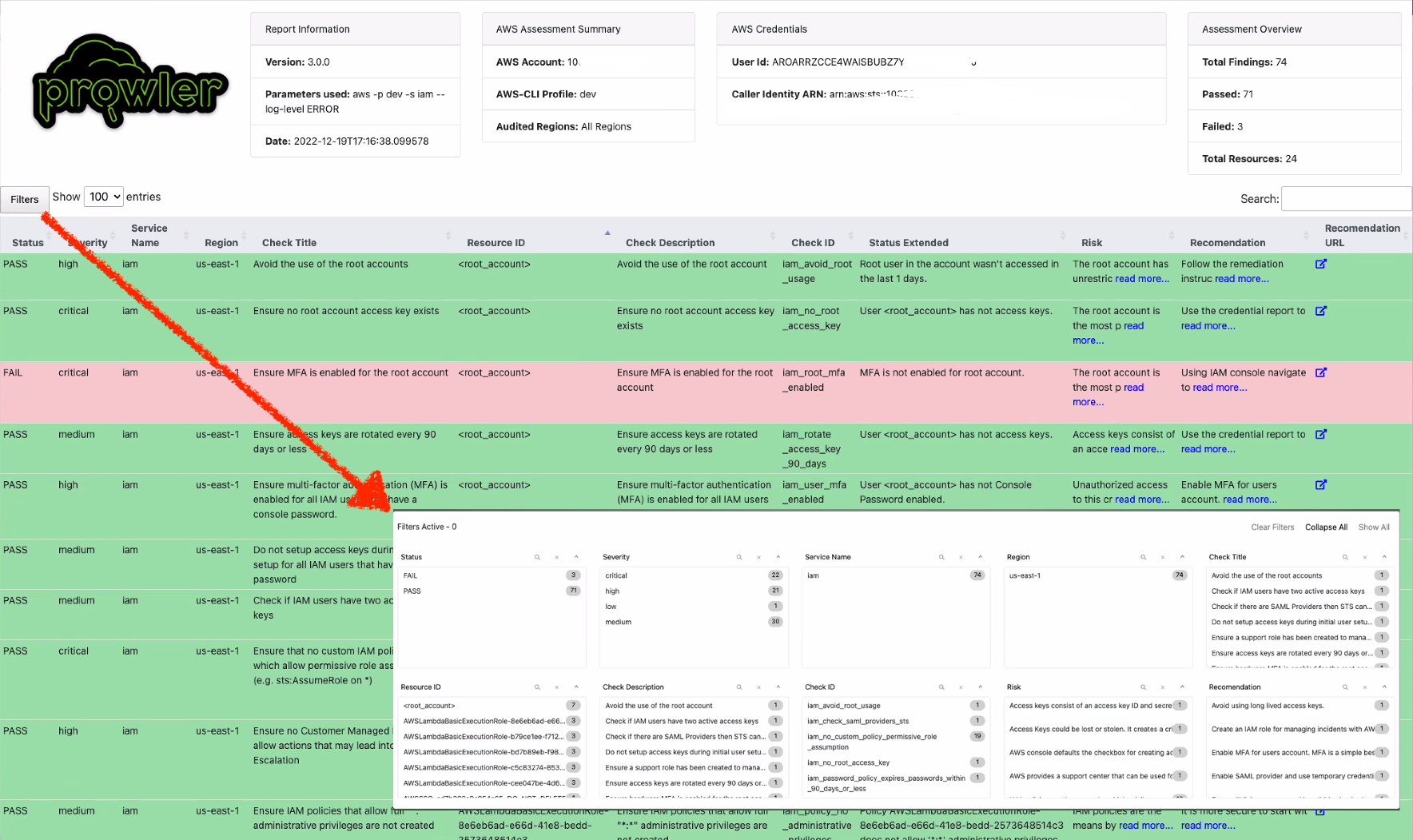
Prowler compliance overview:
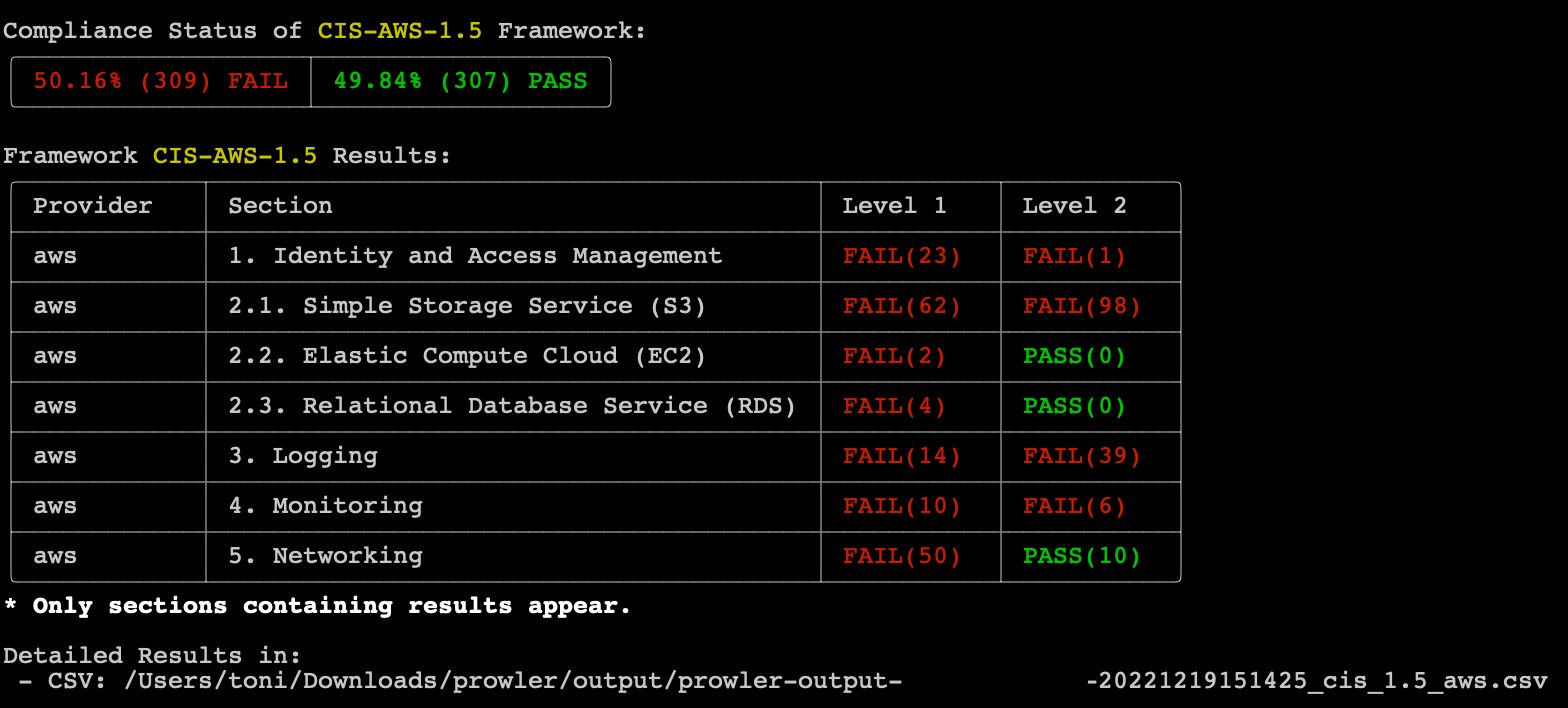
Prowler list of Azure checks:
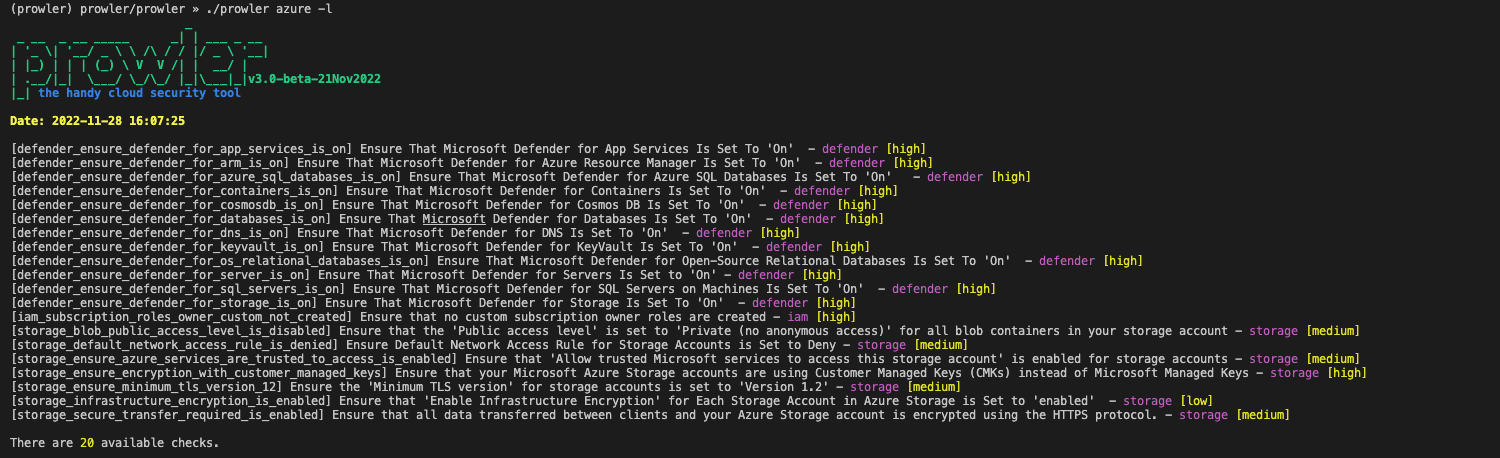
What is coming next?
- More Cloud Providers and more checks: in addition to keep adding new checks to AWS and Azure, we plan to include GCP and OCI soon, let us know if you want to contribute!
- XML-JUNIT support: we didn’t add that to v3, if you miss it, let us know in https://github.com/prowler-cloud/prowler/discussions
- Compliance: we will add more compliance frameworks to have as many as in Prowler v2, we appreciate help though!
- Tags based audit: you will be able to scan only those resources with specific tags.
New Contributors
In addition to the Prowler rock stars @jfagoagas @n4ch04 @sergargar we have a couple of new contributors in this release:
- @StylusFrost made their first contribution in https://github.com/prowler-cloud/prowler/pull/1350
- @alexr3y made their first contribution in https://github.com/prowler-cloud/prowler/pull/1502
For more information and a detailed list of changes see below:
Full Changelog: https://github.com/prowler-cloud/prowler/compare/2.10.0...3.0.0
Published by toniblyx almost 2 years ago
Fixes
- fix(extra7195): Update title by @Fennerr in https://github.com/prowler-cloud/prowler/pull/1440
- fix(extra71): Modified wrong remediation by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1445
- fix(README): include more details about db connector by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1507
- fix(extra723): corrected some typos for check_extra723 by @kagahd in https://github.com/prowler-cloud/prowler/pull/1511
- fix(CloudTrail): Fix CloudTrail trail S3 logging public bucket false positive result when trail bucket doesn't exist by @acknosyn in https://github.com/prowler-cloud/prowler/pull/1505
New Contributors
- @Fennerr made their first contribution in https://github.com/prowler-cloud/prowler/pull/1440
Full Changelog: https://github.com/prowler-cloud/prowler/compare/2.12.0...2.12.1
Published by toniblyx almost 2 years ago
Where Eagles Dare is the song that opens the Piece of Mind album of Iron Maiden, released back in 1983, the first one with Nicko McBrain as drummer after Clive Burr left the band, note his first seconds on this piece, it is like Nicko saying "here I go!". This song relates the adventure of a team of soldiers raiding a castle in Germany during the WWII, that is related in the movie with the same name starred by Clint Eastwood and Richard Burton.
For all of you that have contributed to this version (see list below), thank you ❤️!!! And reach out to me on Twitter (@toniblyx - DMs are open) if you want some laptop stickers.
🔥Important changes in this version (read this!)🔥:
New checks:
7.195 [check7195] Ensure CodeArtifact internal packages do not allow external public source publishing. - codeartifact [Critical]
Other changes:
- CloudTrail checks check21, check22, check23, check24, check26, check27 now include shadow trails in the results (those trails used for multi-region and AWS organizations)
- New group called
cisig2for CIS Critical Security Controls v8 by @artfulbodger - We have deprecated Discord and now we only use Slack, join us here!
New features:
- feat(checks): Adding commands for checks 117 and 118 by @belialboy in https://github.com/prowler-cloud/prowler/pull/1289
- feat(extra780): Check for Cognito or SAML authentication on OpenSearch by @kagahd in https://github.com/prowler-cloud/prowler/pull/1291
- feat(extra7195): Added check for dependency confusion in codeartifact by @congon4tor in https://github.com/prowler-cloud/prowler/pull/1329
- feat(group): CIS Critical Security Controls v8 by @artfulbodger in https://github.com/prowler-cloud/prowler/pull/1347
- feat(audit_id): add optional audit_id field to postgres connector by @sergargar in https://github.com/prowler-cloud/prowler/pull/1362
- feat(db-connector): Include UUID for findings ID by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1368
- feat(slack): add Slack badge to README instead of deprecated Discord by @sergargar in https://github.com/prowler-cloud/prowler/pull/1401
- feat(extra7111): Exception handling by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1408
- feat(stable tag): Inclusion of stable tag point to last release by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1419
- docs(spelling): Typo corrections by @olivier987654 in https://github.com/prowler-cloud/prowler/pull/1394
Enhancements:
- chore(issues): Link Q&A by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1305
- docs(outputs): added CVS and JSON details by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1313
- docs(dockerfile): Dockerfile build instructions by @walkerab in https://github.com/prowler-cloud/prowler/pull/1370
- chore(actions): Bump Trufflehog to v3.13.0 by @gliptak in https://github.com/prowler-cloud/prowler/pull/1382
- delete(shortcut.sh): Remove ScoutSuite by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1388
- fix(checks): CloudTrail checks 2.X now include shadow trails in the results (those trails used for multi-region and AWS organizations)
Fixes:
- fix(check12): Improve remediation by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1281
- fix(extra712): changed Macie service detection by @williambrady in https://github.com/prowler-cloud/prowler/pull/1286
- fix(permissions): Include missing appstream:DescribeFleets permission by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1278
- fix(appstream): Handle timeout errors by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1296
- fix(security-groups): Include TCP as the IpProtocol by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1323
- fix(credential_report): Do not generate for 117 and 118 by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1322
- fix(inventory): Variable assigning syntax in inventory mode by @JArmandoG in https://github.com/prowler-cloud/prowler/pull/1283
- fix(check120): correct AWS support policy name by @JArmandoG in https://github.com/prowler-cloud/prowler/pull/1328
- fix(postgresql): Connector field by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1372
- fix(postgresql): Missing space by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1374
- fix(checks): Include missing output in checks by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1380
- fix(checks): Handle checks not returning result by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1383
- fix(inventory): quick inventory input fixed by @sergargar in https://github.com/prowler-cloud/prowler/pull/1397
- fix(check_extra77): Add missing check_resource_id to the report by @kagahd in https://github.com/prowler-cloud/prowler/pull/1402
- fix(missing permissions): add missing permissions of checks by @sergargar in https://github.com/prowler-cloud/prowler/pull/1403
- fix(region_bugs): Remove duplicate outputs by @sergargar in https://github.com/prowler-cloud/prowler/pull/1390
- fix(extra740): remove additional info and fix max_items by @sergargar in https://github.com/prowler-cloud/prowler/pull/1405
- fix(extra77): Deleted resource id from exception results by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1409
- fix(extra7183): Exception handling error UnsupportedOperationException by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1410
- fix(extra7184): Error handling GetSnapshotLimits api call by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1411
New Contributors:
- @williambrady made their first contribution in https://github.com/prowler-cloud/prowler/pull/1286
- @belialboy made their first contribution in https://github.com/prowler-cloud/prowler/pull/1289
- @kagahd made their first contribution in https://github.com/prowler-cloud/prowler/pull/1291
- @JArmandoG made their first contribution in https://github.com/prowler-cloud/prowler/pull/1283
- @congon4tor made their first contribution in https://github.com/prowler-cloud/prowler/pull/1329
- @artfulbodger made their first contribution in https://github.com/prowler-cloud/prowler/pull/1347
- @walkerab made their first contribution in https://github.com/prowler-cloud/prowler/pull/1370
- @olivier987654 made their first contribution in https://github.com/prowler-cloud/prowler/pull/1394
Full Changelog: https://github.com/prowler-cloud/prowler/compare/2.11.0...2.12.0
Published by toniblyx over 2 years ago
Steve Harris, founder and bass guitar of Iron Maiden 🤘🏽 wrote this song when he lost his father, lyrics and music is beautiful. This release is for those that always look forward and only look back to be thankful and learn. Also this song and version is to thanks my Prowler brothers @jfagoagas, @n4ch04, @sergargar and @drewkerrigan, they are working as beasts every day to make this piece of software better and building something awesome with Prowler underneath called Prowler Pro.
For all of you that have contributed to this version (see list below), thank you ❤️!!! And reach out to me on Twitter (@toniblyx - DMs are open) if you want some laptop stickers.
🔥Important changes in this version (read this!):
- 14 New checks covering Directory Service, IAM, S3, Workspaces, AppStream and ECR:
7.181 [extra7181] Directory Service monitoring with CloudWatch logs - ds [Medium]
7.182 [extra7182] Directory Service SNS Notifications - ds [Medium]
7.183 [extra7183] Directory Service LDAP Certificates expiration - ds [Medium]
7.184 [extra7184] Directory Service Manual Snapshot Limit - ds [Low]
7.185 [extra7185] Ensure no Customer Managed IAM policies allow actions that may lead into Privilege Escalation - iam [High]
7.186 [extra7186] Check S3 Account Level Public Access Block - s3 [High]
7.187 [extra7187] Ensure that your Amazon WorkSpaces storage volumes are encrypted in order to meet security and compliance requirements - workspaces [High]
7.188 [extra7188] Ensure Radius server in DS is using the recommended security protocol - ds [Medium]
7.189 [extra7189] Ensure Multi-Factor Authentication (MFA) using Radius Server is enabled in DS - ds [Medium]
7.190 [extra7190] Ensure user maximum session duration is no longer than 10 hours. - appstream [Medium]
7.191 [extra7191] Ensure session disconnect timeout is set to 5 minutes or less. - appstream [Medium]
7.192 [extra7192] Ensure session idle disconnect timeout is set to 10 minutes or less. - appstream [Medium]
7.193 [extra7193] Ensure default Internet Access from your Amazon AppStream fleet streaming instances should remain unchecked. - appstream [Medium]
7.194 [extra7194] Check if ECR repositories have lifecycle policies enabled - ecr [Low]
-
New beta feature called Prowler Quick Inventory, run
./prowler -iand tell us how it works for you. More information here: https://github.com/prowler-cloud/prowler#inventory


-
Look at the new IAM check
extra7185that will help you find IAM customer managed policies that may lead into privilege escalation. -
Now you can send findings directly to a PostgreSQL DB. More here https://github.com/prowler-cloud/prowler#database-providers-connector.
-
We have refactored the whole core to improve how everything is put together, that is helping us to write the new v3 in python.
New features:
- feat(check) Directory Service by @lemelop in https://github.com/prowler-cloud/prowler/pull/1164
- feat(check): PublicAccessBlockConfiguration by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1167
- feat(check): Amazon WorkSpaces storage volumes are encrypted by @rajarshidas in https://github.com/prowler-cloud/prowler/pull/1166
- feat(inventory): Prowler quick inventory including IAM resources by @toniblyx in https://github.com/prowler-cloud/prowler/pull/1258
- feat(ecr_lifecycle): Check Lifecycle policy by @massyn in https://github.com/prowler-cloud/prowler/pull/1260
- feat(checks): New IAM privilege escalation check by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1168
- feat(codebuild_timeout): Increase codebuild timeout to maximum. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1192
- feat(db) Create a PostgreSQL connector for Prowler by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1171
- feat(checks): Amazon AppStream checks by @rajarshidas in https://github.com/prowler-cloud/prowler/pull/1216
- feat(check): Ensure default internet access from Amazon AppStream fleet should be disabled. by @rajarshidas in https://github.com/prowler-cloud/prowler/pull/1233
- feat(dockerfile): Include psql client in the Prowler scanner image by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1238
- feat(db-connector): Support environment variables by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1236
- feat(inventory): Prowler quick inventory by @toniblyx in https://github.com/prowler-cloud/prowler/pull/1245
Enhancements:
- feat(output): Consolidate prowler output functions by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1180
- refactor(Prowler): Main logic refactor by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1189
- feat(extra7185): Update severity of check extra7185 by @sergargar in https://github.com/prowler-cloud/prowler/pull/1178
- feat(actions): Trigger by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1209
- feat(check): Directory Service - Ensure Radius server is using the recommended security protocol by @rajarshidas in https://github.com/prowler-cloud/prowler/pull/1203
- docs(readme): Update inventory and checks by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1257
- feat(check7164): 365 days or more in a Cloudwatch log retention should be consider PASS by @bcarranza in https://github.com/prowler-cloud/prowler/pull/1240
Fixes:
- fix(extra767): Remove false positive for check_extra767 by @zsecducna in https://github.com/prowler-cloud/prowler/pull/1198
- fix(update_deprecate_runtimes): Deprecated runtimes for lambda were updated. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1170
- fix(runtimes_extra762): Detect nodejs versions correctly. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1177
- fix(SQS_encryption_type): Add SQS encryption types to extra728. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1175
- fix(typo): Max session duration error message by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1179
- fix(apigateway_iam): Error handling and permissions for extra745. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1176
- fix(assume_role): Use date instead of jq by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1181
- fix(check119_remediation): Update check remediation text. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1185
- fix(codebuild_update): AWS CLI and permissions update. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1183
- fix(extra7187): Remove commas from the metadata by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1187
- fix(outputs): Replace each comma occurrence before sending to csv file by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1188
- fix(shellcheck): Main variables by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1194
- fix(session_duration): Use jq with TZ=UTC by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1195
- fix(instance-metadata): Credentials recovering by @sergargar in https://github.com/prowler-cloud/prowler/pull/1207
- fix(actions): Dockerfile path by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1208
- fix(junit_xml output): Fix xml output integration. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1210
- fix(instance metadata): missing raw flag in jq parser by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1214
- fix(shub_fails): Treat failed findings as failed in SHub. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1219
- fix(extra7162): Query AWS log groups using LOG_GROUP_RETENTION_PERIOD_DAYS by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1232
- fix(backupInitialAWSCredentials): Do nothing if no initial creds by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1239
- fix(postgres): Fix postgres connector issues. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1244
- fix(add-checks-regions): Missing regions in checks by @sergargar in https://github.com/prowler-cloud/prowler/pull/1247
- fix(Dockerfile): Prowler path by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1254
- fix(apigatewayv2): handle BadRequestException by @sergargar in https://github.com/prowler-cloud/prowler/pull/1261
- fix(codebuild): expired token error by @sergargar in https://github.com/prowler-cloud/prowler/pull/1262
- fix(extra7173): Correct check and alternative name by @vigah in https://github.com/prowler-cloud/prowler/pull/1270
- docs(readme): Fix spelling by @r8bhavneet in https://github.com/prowler-cloud/prowler/pull/1271
- docs(readme): Fix spelling errors by @andsiu https://github.com/prowler-cloud/prowler/pull/1274
- fix(ci): Remove
yum check-updateby @jfagoagas https://github.com/prowler-cloud/prowler/pull/1275
New Contributors
- @lemelop made their first contribution in https://github.com/prowler-cloud/prowler/pull/1164
- @rajarshidas made their first contribution in https://github.com/prowler-cloud/prowler/pull/1166
- @zsecducna made their first contribution in https://github.com/prowler-cloud/prowler/pull/1198
- @bcarranza made their first contribution in https://github.com/prowler-cloud/prowler/pull/1240
- @massyn made their first contribution in https://github.com/prowler-cloud/prowler/pull/1260
- @vigah made their first contribution in https://github.com/prowler-cloud/prowler/pull/1270
- @r8bhavneet made their first contribution in https://github.com/prowler-cloud/prowler/pull/1271
Full Changelog: https://github.com/prowler-cloud/prowler/compare/2.10.0...2.11.0
Published by toniblyx over 2 years ago
Fly on your way, like an eagle
Fly as high as the sun
On your way, like an eagle
Fly, touch the sun
Flight of Icarus is a song of Iron Maiden released in 1983 as part of their Piece of Mind album. There are some amazing guitar solos in this song and it is so good, watch the video and enjoy it like this new version here:
https://www.youtube.com/watch?v=p4w2BZXL6Ss:

Image copyright by Iron Maiden
Important changes in this version (read this!):
- Now you can manage the Allow list feature using DynamoDB instead of just a text plain file.
- 7 new checks available for CodeBuild, EMR and Lambda:
7.174 [extra7174] CodeBuild Project last invoked greater than 90 days - codebuild [High]
7.175 [extra7175] CodeBuild Project with an user controlled buildspec - codebuild [High]
7.176 [extra7176] EMR Cluster without Public IP - emr [Medium]
7.177 [extra7177] Publicly accessible EMR Cluster - emr [High]
7.178 [extra7178] EMR Account Public Access Block enabled - emr [High]
7.179 [extra7179] Check Public Lambda Function URL - lambda [High]
7.180 [extra7180] Check Lambda Function URL CORS configuration - lambda [Medium]
New features:
- feat(new): New checks for lambda functions URL by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1148
- feat(new): New checks for CodeBuild and EMR added by @0xDivyanshu in https://github.com/prowler-cloud/prowler/pull/1112
- feat(emr): New check BlockPublicAccessConfiguration for EMR by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1120
- feat(new): New custom check extra9999 to build a custom check on the fly by @sectoramen in https://github.com/prowler-cloud/prowler/pull/1103
- feat(assume-role): Properly handle External ID variable by @chrisdlangton in https://github.com/prowler-cloud/prowler/pull/1128
- feat(dynamodb_allowlist): Support DynamoDB tables ARN for allowlist input by @sergargar in https://github.com/prowler-cloud/prowler/pull/1118
- feat(group7): Include extra7178 by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1121
- feat(contrib): Serverless multi account Prowler with SecurityHub Integration by @MorlaxAR in https://github.com/prowler-cloud/prowler/pull/1113
- feat(actions): Upload Prowler containers to registries by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1132
- feat(util): K8s cronjob sample files by @charles-josiah in https://github.com/prowler-cloud/prowler/pull/1140
Enhancements:
- Update CloudFormation template for CodeBuild by @jplock in https://github.com/prowler-cloud/prowler/pull/1114
- Updated multi-org ProwlerRole.yaml to match current Prowler additions policy by @ChrisGoKim in https://github.com/prowler-cloud/prowler/pull/1123
- docs(k8s-integration): Beautify README by @1vicente in https://github.com/prowler-cloud/prowler/pull/1153
Fixes:
- fix(checks): Handle AWS Gov Cloud regions #1160
- fix(check): check_extra7113: Fix wrong listing of RDS instances in regions without databases by @Sinnohd in https://github.com/prowler-cloud/prowler/pull/1124
- fix(custom-file-in-bucket): Custom file names are also support for S3 output. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1129
- fix(copyToS3): Upload to S3 only when indicated. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1134
- fix(actions): tag and push by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1142
- fix(readme): Fix correct permissions for DynamoDB allowlist. by @sergargar in https://github.com/prowler-cloud/prowler/pull/1147
- fix(actions): Ignore changes on Readme by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1149
- fix(timestamp): Timestamp to date casting issues solved by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1154
- fix(IllegalLocationConstraintException): Recover bucket policy using the right region endpoint by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1155
- fix(BucketLocation): Recover bucket policy using the right region endpoint by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1156
- fix(remediation): Fix empty remediation fields for checks 7164, 7144 and 7163 by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1157
New Contributors
- @0xDivyanshu made their first contribution in https://github.com/prowler-cloud/prowler/pull/1112
- @jplock made their first contribution in https://github.com/prowler-cloud/prowler/pull/1114
- @Sinnohd made their first contribution in https://github.com/prowler-cloud/prowler/pull/1124
- @ChrisGoKim made their first contribution in https://github.com/prowler-cloud/prowler/pull/1123
- @MorlaxAR made their first contribution in https://github.com/prowler-cloud/prowler/pull/1113
- @chrisdlangton made their first contribution in https://github.com/prowler-cloud/prowler/pull/1128
- @charles-josiah made their first contribution in https://github.com/prowler-cloud/prowler/pull/1140
- @1vicente made their first contribution in https://github.com/prowler-cloud/prowler/pull/1153
Full Changelog: https://github.com/prowler-cloud/prowler/compare/2.9.0...2.10.0
Published by jfagoagas over 2 years ago
In 1982, Iron Maiden released The Number of the Beast, their third studio album and the first with Bruce Dickinson as their lead vocalist. The song Run to the Hills gives me very good memories, as the time we are living will do the same in the future. That song is one of the greatest metal songs in music history. Enjoy it as we do while releasing this new version of Prowler!
https://www.youtube.com/watch?v=86URGgqONvA

Image copyright by Iron Maiden
Important changes in this version (read this!):
Now, if you want to use your allowlist or custom checks you can retrieve it from a S3 Bucket using -w option along with a S3 URI like s3://bucket/prefix/allowlist_sample.txt
Also, we have enriched some IAM checks to provide more information about resources when the check status is PASS.
New Features
- New Extra Check - Detect SGs created by the EC2 Launch Wizard by @sectoramen in https://github.com/prowler-cloud/prowler/pull/1081
- Support S3 URIs for custom checks paths by @sergargar in https://github.com/prowler-cloud/prowler/pull/1090
- Support S3 URIs for allowlist file by @sergargar in https://github.com/prowler-cloud/prowler/pull/1090
Enhancements
- Update example code for terraform-quickstart by @spazm in https://github.com/prowler-cloud/prowler/pull/1086
- Replace comma from csv input info to prevent breaking
csvformat by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1102 - IAM check116 and check122 now logs more detailed information with PASS results by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1107
Fixes
- Fix(secrets_library): Verify if detect-secrets library is missing by @sergargar in https://github.com/prowler-cloud/prowler/pull/1080
- Fix(extra729,extra740): Typo by @mourackb in https://github.com/prowler-cloud/prowler/pull/1083
- Fix(extra736): Missing $PROFILE_OPT by @soffensive in https://github.com/prowler-cloud/prowler/pull/1084
- Fix(extra792): TLS1.3 policies added as secure and TLS1.1/1.0 as insecure by @sergargar in https://github.com/prowler-cloud/prowler/pull/1091
- Fix(extra7172): IllegalLocationConstraintException properly handled by @sergargar in https://github.com/prowler-cloud/prowler/pull/1093
- Fix(extra764): NoSuchBucket error properly handled by @sergargar in https://github.com/prowler-cloud/prowler/pull/1094
- Fix(extra764): Deleted temporary file references by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1089
- Fix(extra7147): Handle unsupported AWS regions for Glacier by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1101
- Fix(extra79): Typo publiccly -> publicly by @carterjones in https://github.com/prowler-cloud/prowler/pull/1106
- Fix(extra75): Empty array check in SECURITYGROUPS object by @nealalan in https://github.com/prowler-cloud/prowler/pull/1099
New Contributors
- @mourackb made their first contribution in https://github.com/prowler-cloud/prowler/pull/1083
- @spazm made their first contribution in https://github.com/prowler-cloud/prowler/pull/1086
- @nealalan made their first contribution in https://github.com/prowler-cloud/prowler/pull/1099
- @carterjones made their first contribution in https://github.com/prowler-cloud/prowler/pull/1106
Full Changelog: https://github.com/prowler-cloud/prowler/compare/2.8.1...2.9.0
Published by sergargar over 2 years ago
What's Changed
- fix(bucket_region): check extra764 doesn't handle bucket region properly by @sergargar in https://github.com/prowler-cloud/prowler/pull/1077
- fix(detect-secrets): Include missing colon to link values by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1078
Full Changelog: https://github.com/prowler-cloud/prowler/compare/2.8.0...2.8.1
Published by toniblyx over 2 years ago
The Ides of March is an instrumental song that opens the second studio album of Iron Maiden called Killers. This song is great as an opening, March is the month when spring starts in my side of the world, is always time for optimism. Ides of March also means 15 of March in the Roman calendar (and the day of the assassination of Julius Caesar). Enjoy the song here.
We have put our best to make this release and with important help of the Prowler community of cloud security engineers around the world, thank you all! Special thanks to the Prowler full time engineers @jfagoagas, @n4ch04 and @sergargar! (and Bruce, my dog) ❤️

Important changes in this version (read this!):
Now, if you have AWS Organizations and are scanning multiple accounts using the assume role functionality, Prowler can get your account details like Account Name, Email, ARN, Organization ID and Tags and add them to CSV and JSON output formats. More information and usage here.
New Features
- 1 New check for S3 buckets have ACLs enabled by @jeffmaley in https://github.com/prowler-cloud/prowler/pull/1023 :
7.172 [extra7172] Check if S3 buckets have ACLs enabled - s3 [Medium] - feat(metadata): Include account metadata in Prowler assessments by @toniblyx in https://github.com/prowler-cloud/prowler/pull/1049
Enhancements
- Add whitelist examples for Control Tower resources by @lorchda in https://github.com/prowler-cloud/prowler/pull/1013
- Skip packages with broken dependencies when upgrading system by @dlorch in https://github.com/prowler-cloud/prowler/pull/1009
- Docs: Improve check_sample examples, add general comments by @lazize in https://github.com/prowler-cloud/prowler/pull/1039
- Added timestamp to temp folders for secrets related checks by @sectoramen in https://github.com/prowler-cloud/prowler/pull/1041
- Make python3 default in Dockerfile by @sectoramen in https://github.com/prowler-cloud/prowler/pull/1043
- Docs(readme): Fix typo by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1072
- Add(filter-region): Support comma separated regions by @thetemplateblog in https://github.com/prowler-cloud/prowler/pull/1071
Fixes
- Fix issue extra75 reports default SecurityGroups as unused #1001 by @jansepke in https://github.com/prowler-cloud/prowler/pull/1006
- Fix issue extra793 filtering out network LBs #1002 by @jansepke in https://github.com/prowler-cloud/prowler/pull/1007
- Fix formatting by @lorchda in https://github.com/prowler-cloud/prowler/pull/1012
- Fix docker references by @mike-stewart in https://github.com/prowler-cloud/prowler/pull/1018
- Fix(check32): filterName base64encoded to avoid space problems in filter names by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1020
- Fix: when prowler exits with a non-zero status, the remainder of the block is not executed by @lorchda in https://github.com/prowler-cloud/prowler/pull/1015
- Fix(extra7148): Error handling and include missing policy by @toniblyx in https://github.com/prowler-cloud/prowler/pull/1021
- Fix(extra760): Error handling by @lazize in https://github.com/prowler-cloud/prowler/pull/1025
- Fix(CODEOWNERS): Rename team by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1027
- Fix(include/outputs): Whitelist logic reformulated to exactly match input by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1029
- Fix CFN CodeBuild example by @mmuller88 in https://github.com/prowler-cloud/prowler/pull/1030
- Fix typo CodeBuild template by @dlorch in https://github.com/prowler-cloud/prowler/pull/1010
- Fix(extra736): Recover only Customer Managed KMS keys by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1036
- Fix(extra7141): Error handling and include missing policy by @lazize in https://github.com/prowler-cloud/prowler/pull/1024
- Fix(extra730): Handle invalid date formats checking ACM certificates by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1033
- Fix(check41/42): Added tcp protocol filter to query by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1035
- Fix(include/outputs):Rolling back whitelist checking to RE check by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1037
- Fix(extra758): Reduce API calls. Print correct instance state. by @lazize in https://github.com/prowler-cloud/prowler/pull/1057
- Fix: extra7167 Advanced Shield and CloudFront bug parsing None output without distributions by @NMuee in https://github.com/prowler-cloud/prowler/pull/1062
- Fix(extra776): Handle image tag commas and json output by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1063
- Fix(whitelist): Whitelist logic reformulated again by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1061
- Fix: Change lower case from bash variable expansion to tr by @lazize in https://github.com/prowler-cloud/prowler/pull/1064
- Fix(check_extra7161): fixed check title by @n4ch04 in https://github.com/prowler-cloud/prowler/pull/1068
- Fix(extra760): Improve error handling by @lazize in https://github.com/prowler-cloud/prowler/pull/1055
- Fix(check122): Error when policy name contains commas by @plarso in https://github.com/prowler-cloud/prowler/pull/1067
- Fix: Remove automatic PR labels by @jfagoagas in https://github.com/prowler-cloud/prowler/pull/1044
- Fix(ES): Improve AWS CLI query and add error handling for ElasticSearch/OpenSearch checks by @lazize in https://github.com/prowler-cloud/prowler/pull/1032
- Fix(extra771): jq fail when policy action is an array by @lazize in https://github.com/prowler-cloud/prowler/pull/1031
- Fix(extra765/776): Add right region to CSV if access is denied by @roman-mueller in https://github.com/prowler-cloud/prowler/pull/1045
- Fix: extra7167 Advanced Shield and CloudFront bug parsing None output without distributions by @NMuee in https://github.com/prowler-cloud/prowler/pull/1053
New Contributors
- @jansepke made their first contribution in https://github.com/prowler-cloud/prowler/pull/1006
- @lorchda made their first contribution in https://github.com/prowler-cloud/prowler/pull/1012
- @mike-stewart made their first contribution in https://github.com/prowler-cloud/prowler/pull/1018
- @n4ch04 made their first contribution in https://github.com/prowler-cloud/prowler/pull/1020
- @jeffmaley made their first contribution in https://github.com/prowler-cloud/prowler/pull/1023
- @roman-mueller made their first contribution in https://github.com/prowler-cloud/prowler/pull/1045
- @NMuee made their first contribution in https://github.com/prowler-cloud/prowler/pull/1053
- @plarso made their first contribution in https://github.com/prowler-cloud/prowler/pull/1067
- @thetemplateblog made their first contribution in https://github.com/prowler-cloud/prowler/pull/1071
- @sergargar made their first contribution in https://github.com/prowler-cloud/prowler/pull/1073
Full Changelog: https://github.com/prowler-cloud/prowler/compare/2.7.0...2.8.0
Published by toniblyx over 2 years ago
This release name is in honor of Brave New World, a great song of 🔥Iron Maiden🔥 from their Brave New World album. Dedicated to all of you looking forward to having the world we had before COVID... We hope is not hitting you bad. Enjoy!
Important changes in this version (read this!):
- As you can see, Prowler is now in a new organization called https://github.com/prowler-cloud/.
- When Prowler doesn't have permissions to check a resources or service it gives an INFO instead of FAIL. We have improved all checks error handling in those use cases when the CLI responds with a AccessDenied, UnauthorizedOperation or AuthorizationError.
- From this version,
masterbranch will be the latest available code and we will keep the stable code as each release, if you are installing or deploying Prowler usinggit cloneto master take that into account and use the latest release instead, i.e.:git clone --branch 2.7 https://github.com/prowler-cloud/prowlerorcurl https://github.com/toniblyx/prowler/archive/refs/tags/2.7.0.tar.gz -o prowler-2.7.0.tar.gz - For known issues please see https://github.com/prowler-cloud/prowler/issues the ones open with
bugas a red tag. - Discussions is now open in the Prowler repo https://github.com/prowler-cloud/prowler/discussions, feel free to use it if that works for you better than the current Discord server.
- 11 new checks!! Thanks to @michael-dickinson-sainsburys, @jonloza, @rustic, @Obiakara, @Daniel-Peladeau, @maisenhe, @7thseraph and @tekdj7. Now there have a total of 218 checks. See below for details.
- An issue with Security Hub integration when resolving closed findings are either a lot of new findings, or a lot of resolved findings is now working as expected thanks to @Kirizan
- When credential are in environment variable it failed to review, that was fixed by @lazize
- See below new features and more details for this version.
New Features
- 11 New checks for Redshift, EFS, CloudWatch, Secrets Manager, DynamoDB and Shield Advanced:
7.160 [extra7160] Check if Redshift has automatic upgrades enabled - redshift [Medium]
7.161 [extra7161] Check if EFS have protects sensative data with encryption at rest - efs [Medium]
7.162 [extra7162] Check if CloudWatch Log Groups have a retention policy of 365 days - cloudwatch [Medium]
7.163 [extra7163] Check if Secrets Manager key rotation is enabled - secretsmanager [Medium]
7.164 [extra7164] Check if CloudWatch log groups are protected by AWS KMS - logs [Medium]
7.165 [extra7165] Check if DynamoDB: DAX Clusters are encrypted at rest - dynamodb [Medium]
7.166 [extra7166] Check if Elastic IP addresses with associations are protected by AWS Shield Advanced - shield [Medium]
7.167 [extra7167] Check if Cloudfront distributions are protected by AWS Shield Advanced - shield [Medium]
7.168 [extra7168] Check if Route53 hosted zones are protected by AWS Shield Advanced - shield [Medium]
7.169 [extra7169] Check if global accelerators are protected by AWS Shield Advanced - shield [Medium]
7.170 [extra7170] Check if internet-facing application load balancers are protected by AWS Shield Advanced - shield [Medium]
7.171 [extra7171] Check if classic load balancers are protected by AWS Shield Advanced - shield [Medium]
- Add
-Doption to copy to S3 with the initial AWS credentials instead of the assumed as with-Boption by @sectoramen in https://github.com/toniblyx/prowler/pull/974 - Add new functions to backup and restore initial AWS credentials, for better handling chaining role by @sectoramen in https://github.com/toniblyx/prowler/pull/978
- Add additional action permissions for Glue and Shield Advanced checks by @lazize in https://github.com/toniblyx/prowler/pull/995
Enhancements
- Update Dockerfile to use Amazon Linux container image by @Kirizan in https://github.com/toniblyx/prowler/pull/972
- Update Readme:
-Toption is not mandatory by @jfagoagas in https://github.com/toniblyx/prowler/pull/944 - Add $PROFILE_OPT to CopyToS3 commands by @sectoramen in https://github.com/toniblyx/prowler/pull/976
- Remove unneeded package "file" from Dockerfile by @sectoramen in https://github.com/toniblyx/prowler/pull/977
- Update docs (templates): Improve bug template with more info by @jfagoagas in https://github.com/toniblyx/prowler/pull/982
Fixes
- Fix in README and multiaccount serverless deployment templates by @dlorch in https://github.com/toniblyx/prowler/pull/939
- Fix assume-role: check if
-Tand-Aoptions are set together by @jfagoagas in https://github.com/toniblyx/prowler/pull/945 - Fix
group25FTR by @lopmoris in https://github.com/toniblyx/prowler/pull/948 - Fix in README link for
group25FTR by @lopmoris in https://github.com/toniblyx/prowler/pull/949 - Fix issue #938 assume_role multiple times by @halfluke in https://github.com/toniblyx/prowler/pull/951
- Fix and clean assume-role to better handle AWS STS CLI errors by @jfagoagas in https://github.com/toniblyx/prowler/pull/946
- Fix issue with Security Hub integration when resolving closed findings are either a lot of new findings, or a lot of resolved findings by @Kirizan in https://github.com/toniblyx/prowler/pull/953
- Fix broken link in README.md by @rtcms in https://github.com/toniblyx/prowler/pull/966
- Fix checks with comma issues in checks by @j2clerck in https://github.com/toniblyx/prowler/pull/975
- Fix: Credential chaining from environment variables by @lazize in https://github.com/toniblyx/prowler/pull/996
New Contributors
- @jonloza made their first contribution in https://github.com/toniblyx/prowler/pull/932
- @Obiakara made their first contribution in https://github.com/toniblyx/prowler/pull/935
- @dlorch made their first contribution in https://github.com/toniblyx/prowler/pull/939
- @Daniel-Peladeau made their first contribution in https://github.com/toniblyx/prowler/pull/937
- @lopmoris made their first contribution in https://github.com/toniblyx/prowler/pull/948
- @halfluke made their first contribution in https://github.com/toniblyx/prowler/pull/951
- @maisenhe made their first contribution in https://github.com/toniblyx/prowler/pull/956
- @rtcms made their first contribution in https://github.com/toniblyx/prowler/pull/966
- @sectoramen made their first contribution in https://github.com/toniblyx/prowler/pull/974
- @j2clerck made their first contribution in https://github.com/toniblyx/prowler/pull/975
- @lazize made their first contribution in https://github.com/toniblyx/prowler/pull/995
Full Changelog: https://github.com/toniblyx/prowler/compare/2.6.1...2.7
Published by toniblyx almost 3 years ago
What's Changed
- e4edb5e - Enhancement IAM assumed role session duration error handling by @jfagoagas
- 3e78f01 - Fix Terraform Kickstarter path in README by @z0ph
- cee6437 - Fix issue #926 resource id and remediation typo
- b251f31 - Fix issue #925 replace sensible by sensitive in multiple checks
- 50de9f2 - Fix output for checks check3x when no CW group is in place
- a6ba580 - Fix severity case variable
New Contributors
- @z0ph made their first contribution in https://github.com/toniblyx/prowler/pull/927
- Thanks @fredski-github for reporting bugs.
Full Changelog: https://github.com/toniblyx/prowler/compare/2.6.0...2.6.1
Published by toniblyx almost 3 years ago
Prowler 2.6.0 - Phantom
This release name is in honor to Phantom of the Opera, one of my favorite songs and a master piece of 🔥Iron Maiden🔥. It starts by "I've been lookin' so long for you now" like looking for security issues, isn't it? 🤘🏼 Enjoy it here while reading the rest of this note.
Important changes in this version:
- CIS level parameter (ITEM_LEVEL) has been reverted to the csv, json and html outputs (it was removed in 2.5), CIS Scored is not added since it is not relevant in the global Prowler reports. dd398a9
- Security Hub integration has been fixed due to a conflict with duplicated findings in the management account by @xeroxnir
- 12 New checks!! Thanks to @kbgoll05, @qumei, @georgie969, @ShubhamShah11, @jarrettandrulis, @dsensibaugh, @ShubhamShah11, @ManuelUgarte, @tekdj7: Now there are a total of 207. See below for details.
- Known issues, please review https://github.com/toniblyx/prowler/issues?q=is%3Aissue+is%3Aopen+label%3Abug.
- Now there is a Discord server for Prowler available, check it out in README.md.
- There is a maintained Docker Hub repo for Prowler and AWS ECR public repo as well. See badges in README.md for details.
- See below new features for more details of new cool stuff in this version.
New Features:
- 12 New checks for efs, redshift, elb, dynamodb, route53, cloiudformation, elb and apigateway:
7.148 [extra7148] Check if EFS File systems have backup enabled - efs [Medium]
7.149 [extra7149] Check if Redshift Clusters have automated snapshots enabled - redshift [Medium]
7.150 [extra7150] Check if Elastic Load Balancers have deletion protection enabled - elb [Medium]
7.151 [extra7151] Check if DynamoDB tables point-in-time recovery (PITR) is enabled - dynamodb [Medium]
7.152 [extra7152] Enable Privacy Protection for for a Route53 Domain - route53 [Medium]
7.153 [extra7153] Enable Transfer Lock for a Route53 Domain - route53 [Medium]
7.154 [extra7154] Enable termination protection for Cloudformation Stacks - cloudformation [MEDIUM]
7.155 [extra7155] Check whether the Application Load Balancer is configured with defensive or strictest desync mitigation mode - elb [MEDIUM]
7.156 [extra7156] Checks if API Gateway V2 has Access Logging enabled - apigateway [Medium]
7.157 [extra7157] Check if API Gateway V2 has configured authorizers - apigateway [Medium]
7.158 [extra7158] Check if ELBV2 has listeners underneath - elb [Medium]
7.159 [extra7159] Check if ELB has listeners underneath - elb [Medium]
- New checks group FTR (AWS Foundational Technical Review) by @jfagoagas
- New feature added flags
Zto control if Prowler returns exit code 3 on a failed check by @Kirizan in https://github.com/toniblyx/prowler/pull/865 - New Prowler Terraform Kickstarter by @singergs
- New way to deploy Prowler at Organizational level with serverless by @bella-kwon
- New feature: adding the ability to provide a file for checks
-Cto be ran by @Kirizan in https://github.com/toniblyx/prowler/pull/891
Enhancements:
- Enhanced scoring when only INFO is detected
- Enhanced ignore archived findings in GuardDuty for check extra7139 by @chbiel in https://github.com/toniblyx/prowler
- /pull/851
- Updated prowler-codebuild-role name for CFN StackSets name length limit by @varunirv in https://github.com/toniblyx/prowler/pull/846
- Added feature to allow role ARN while using -R parameter by @mmuller88 in https://github.com/toniblyx/prowler/pull/860
- Updated documentation regarding a confusion with the
-qoption (issue #884) by @w0rmr1d3r in https://github.com/toniblyx/prowler/pull/890
Fixes:
- Fixed extra737 remove false positives due to policies with condition by @rinaudjaws in https://github.com/toniblyx/prowler/pull/849
- Fixed title, remediation and doc link for check extra768 by @w0rmr1d3r in https://github.com/toniblyx/prowler/pull/853
- Fixed typo in risk description for check29 by @kamiryo in https://github.com/toniblyx/prowler/pull/858
- Fixed bug in extra784 by @tayivan-sg in https://github.com/toniblyx/prowler/pull/856
- Fixed support policy arn in check120 by @hersh86 in https://github.com/toniblyx/prowler/pull/862
- Fixed typo and HTTP capitalisation in extra7142 by @acknosyn in https://github.com/toniblyx/prowler/pull/863
- Fixed Security Hub conflict with duplicated findings in the management account #711 by @xeroxnir in https://github.com/toniblyx/prowler/pull/873
- Fixed doc reference link in check23 @FallenAtticus by @FallenAtticus in https://github.com/toniblyx/prowler/pull/864
- Fixed duplicated region in textFail message for extra741 by @pablopagani in https://github.com/toniblyx/prowler/pull/880
- Updated parts from check7152 accidentally left in by @jarrettandrulis in https://github.com/toniblyx/prowler/pull/895
- Fix check extra734 about S3 buckets default encryption with StringNotEquals by @rustic in https://github.com/toniblyx/prowler/pull/896
- Fix Shodan typo in -h usage text by @jfagoagas in https://github.com/toniblyx/prowler/pull/899
- Fixed typo in README.md by @bevel-zgates in https://github.com/toniblyx/prowler/pull/908
New Contributors
- @varunirv made their first contribution in https://github.com/toniblyx/prowler/pull/846
- @rinaudjaws made their first contribution in https://github.com/toniblyx/prowler/pull/849
- @chbiel made their first contribution in https://github.com/toniblyx/prowler/pull/851
- @tayivan-sg made their first contribution in https://github.com/toniblyx/prowler/pull/856
- @bella-kwon made their first contribution in https://github.com/toniblyx/prowler/pull/857
- @mmuller88 made their first contribution in https://github.com/toniblyx/prowler/pull/860
- @hersh86 made their first contribution in https://github.com/toniblyx/prowler/pull/862
- @acknosyn made their first contribution in https://github.com/toniblyx/prowler/pull/863
- @FallenAtticus made their first contribution in https://github.com/toniblyx/prowler/pull/864
- @georgie969 made their first contribution in https://github.com/toniblyx/prowler/pull/866
- @ManuelUgarte made their first contribution in https://github.com/toniblyx/prowler/pull/869
- @jarrettandrulis made their first contribution in https://github.com/toniblyx/prowler/pull/875
- @ShubhamShah11 made their first contribution in https://github.com/toniblyx/prowler/pull/877
- @dsensibaugh made their first contribution in https://github.com/toniblyx/prowler/pull/889
- @rustic made their first contribution in https://github.com/toniblyx/prowler/pull/896
- @zqumei0 made their first contribution in https://github.com/toniblyx/prowler/pull/894
- @bevel-zgates made their first contribution in https://github.com/toniblyx/prowler/pull/908
Full Changelog: https://github.com/toniblyx/prowler/compare/2.5.0...2.6.0
Thank you all for your contributions, Prowler community is awesome! 🥳
Published by toniblyx about 3 years ago
Prowler 2.5.0 - Senjutsu

This new version was planned to celebrate AWS re:Inforce that would have taken place on August 24th and 25th but has been cancelled and the new studio album of Iron Maiden (Senjutsu) to be released on September 3rd 2021. In any case, enjoy this new version. More cool stuff coming soon!
Prowler would have been present in the re:Inforce 2021 conference with a pretty expected workshop called "Building Prowler into a QuickSight powered AWS security dashboard". Templates and workshop link to be public soon. For updates follow me on Twitter: https://twitter.com/ToniBlyx.

As Prowler keeps growing in user base and downloads (averages 1400 clones/day), there are more contributions and I want to thank you all for your feedback and code. Please keep contributing to make the Internet more secure.
New Features:
Please read carefully this new features and changes (for CSV output and also to improve the data in json ASFF for Security Hub integration) if you have integrations using CSV, it may affect you.
- New CSV headers, added PROWLER_START_TIME:
PROFILE{SEP}ACCOUNT_NUM,REGION,TITLE_ID,CHECK_RESULT,ITEM_SCORED,ITEM_LEVEL,TITLE_TEXT,CHECK_RESULT_EXTENDED,CHECK_ASFF_COMPLIANCE_TYPE,CHECK_SEVERITY,CHECK_SERVICENAME,CHECK_ASFF_RESOURCE_TYPE,CHECK_ASFF_TYPE,CHECK_RISK,CHECK_REMEDIATION,CHECK_DOC,CHECK_CAF_EPIC,CHECK_RESOURCE_ID,PROWLER_START_TIME. - 14 New checks (@jfagoagas, @nayabpatel, @Outrun207 and @pablopagani):
7.134 [extra7134] Ensure no security groups allow ingress from 0.0.0.0/0 or ::/0 to FTP ports 20 or 21 - ec2 [High]
7.135 [extra7135] Ensure no security groups allow ingress from 0.0.0.0/0 or ::/0 to Kafka port 9092 - ec2 [High]
7.136 [extra7136] Ensure no security groups allow ingress from 0.0.0.0/0 or ::/0 to Telnet port 23 - ec2 [High]
7.137 [extra7137] Ensure no security groups allow ingress from 0.0.0.0/0 or ::/0 to Windows SQL Server ports 1433 or 1434 - ec2 [High]
7.138 [extra7138] Ensure no Network ACLs allow ingress from 0.0.0.0/0 to any port - ec2 [High]
7.139 [extra7139] There are High severity GuardDuty findings - guardduty [High]
7.140 [extra7140] Check if there are SSM Documents set as public - ssm [High]
7.141 [extra7141] Find secrets in SSM Documents - ssm [Critical]
7.142 [extra7142] Check if Application Load Balancer is dropping invalid packets to prevent header based http request smuggling - elb [Medium]
7.143 [extra7143] Check if EFS have policies which allow access to everyone - efs [Critical]
7.144 [extra7144] Check if CloudWatch has allowed cross-account sharing - cloudwatch [Medium]
7.145 [extra7145] Check if Lambda functions have policies which allow access to any AWS account - lambda [Critical]
7.146 [extra7146] Check if there is any unassigned Elastic IP - ec2 [Low]
7.147 [extra7147] Check if S3 Glacier vaults have policies which allow access to everyone - glacier [Critical]
- Docker images are available in the official ECR https://gallery.ecr.aws/prowler/prowler (if you run Prowler with Fargate this will help you). Images at https://hub.docker.com/r/toniblyx/prowler won't be updated.
- Now when using -M option prowler shows standard output but saves desired reports in background
- Added code for better experience running Prowler in AWS CloudShell @hackersifu
- Added support for custom output folder and S3 bucket (see
./prowler -hfor details) using bucket-owner-full-control. - Added support for custom output file (see
./prowler -hfor details) @yangsec888 - Added servicename to the title for ASFF and used for QuickSight dashboard
- Added resourceid and more metadata to the ASFF file to be imported in Security Hub @singergs
- Added s3 and glue required permissions and removed obsoletes
- Added section with info about regions in README.md
- Added WAF CLASSIC check for extra7129 @kamiryo
- Added severity and servicename to the default output, removed blue color on check ID.
- Removed duplicated checks extra756 and extra737 @w0rmr1d3r
Enhancements:
- HTML report: filtering and other nice things @nickmalcolm
- License file and banner cosolidation
- Now it shows default output regardless custom outputs called with -M
- Clean up check title without info related to CIS (like scored, etc. CIS support still in Prowler)
- Updated Docker image to Alpine to 3.13 and with py3-pip in Dockerfile @gliptak
- Improved error handling sts get-caller-identity @pablopagani
- Improved error handling when listing regions @pablopagani
- Updated html report color contrast for WCAG 2.1 accessibility standards @danielperez660
- Updated Prowler additions policy
- Updated check12 - Missing MFA at the beginning of remediation @thorkill
- Removed CSV header in stdout
- Updated README to include reference to CloudShell https://github.com/toniblyx/prowler/tree/2.5/util/cloudshell @hackersifu
- Updated README with better coverage of
-f <filterregion>usage info
Fixes:
- Fixed Security Hub integration error resource type is always empty #776
- Fixed credential renewal broke on Alpine Linux #775
- Fixed check extra747 grammar #774
- Fixed grammar issue in scoring @w0rmr1d3r
- Fixed check21 to fail if trail is off
- Fixed aws organizations multi-account deployment s3 upload issue @owlvat
- Corrected bug on groups when listing checks @pablopagani
- Fixed issue #811 @h1008
- Fixed kms keys compatibility in cli v2 and v1 @dbellizzi
- Fixed typo in check extra7141 ID
- Fixed alias of extra7139
- Fixed link to doc for check45 check46 extra7138 and extras
*If you have made a contribution to this released and I missed your Github id here, my apologies and please let me know to include you. Thank you!