
vuls
Agent-less vulnerability scanner for Linux, FreeBSD, Container, WordPress, Programming language libraries, Network devices
GPL-3.0 License
Bot releases are visible (Hide)
Published by github-actions[bot] about 4 years ago
Changelog
a0e592b fix(report): fix segfault while uploading to s3 (#1033)
Published by github-actions[bot] about 4 years ago
Changelog
7eccc53 fix(msfdb): udpate go-msfdb-deps (#1032)
Published by github-actions[bot] about 4 years ago
Changelog
59daa85 fix(gost): suppress err logging when unsupported debian (#1031)
3f52d31 fix(log): suppress err msg if no access priv to logfile (#1029)
Published by github-actions[bot] over 4 years ago
Changelog
11a7a0c Display metasploit module information for each detected CVE-IDs (#1011)
New features
Display metasploit module information for each detected CVE-IDs
- config.toml
Add [metasploit] to the database sections(cveDict, ovalDict...)
[metasploit]
type = "sqlite3"
SQLite3Path = "/path/to/go-msfdb.sqlite3"
# url = ""
- type : the method of access for the database
- SQLite3Path : Should only be set when using "sqlite" otherwise unused.
- url : specifies the url to access the database.
For more Details, see the Document
Published by github-actions[bot] over 4 years ago
Changelog
89f49b0 Fix trivy parser test (#1014)
72457cb bump up version
c11ba27 fix(libscan): include a lockfile path of libs (#1012)
8a611f9 add diff-mode info (#1008)
Published by github-actions[bot] over 4 years ago
Changelog
4a73875 bump up version (#1007)
d9d5e61 Support ProxyJump option when using ssh command (#1004)
4d8599e update deps (#1006)
59c7061 Fix SSH failure due to .ssh/config owner (#1005)
996557c support alpine3.11 (#1002)
519fb19 Added ReportedAt time for server mode reports (#996)
36456cb feat(wordpress): Cache WpVulnDB (#989)
4ae87cc Fix releaser (#988)
b37df89 Support SMTPS when using report -to-email (#991)
d18e7a7 add trivy parser (#981)
8d5ea98 add -wp-ignore-inactive flag which ignores inactive plugin or themes (#974)
Published by github-actions[bot] over 4 years ago
Changelog
1e2a299 delete 32 bit releaser
0e0f946 add 32 bit releaser and add exit code in cmd
621fa8a fix releaser
1ac0750 fix releaser
5e37ec8 fix releaser
a6009c4 fix releaser
d18e7a7 add trivy parser (#981)
8d5ea98 add -wp-ignore-inactive flag which ignores inactive plugin or themes (#974)
Published by github-actions[bot] over 4 years ago
Ubuntu20.04 Support
Thanks @DaikiYamakawa
Changelog
835dc08 fix .golangci.yml
62c9409 add a github actions config (#985)
2374f57 Bump up version
34e2f03 add kernelnames ubuntu20.04 (#982)
420825c remove append (#978)
Published by kotakanbe over 4 years ago
- Container image scanning has been deprecated since v0.9.5 (#971 ).
- Fixed some bugs.
https://github.com/future-architect/vuls/compare/v0.9.4...v0.9.5
Published by kotakanbe over 4 years ago
Fixed some bugs.
https://github.com/future-architect/vuls/compare/v0.9.3...v0.9.4
Published by kotakanbe over 4 years ago
https://github.com/future-architect/vuls/compare/v0.9.2...v0.9.3
feat(report): display "fixed" when updatable even in fast mode #957
https://github.com/future-architect/vuls/pull/957
Ubuntu18 (fast scan mode)
-
before

-
after

Debian9 (fast scan mode)
- before

-after

fix(report): kernel vulns detection BUG in Ubuntu #958
OVAL for Ubuntu has been changed. The kernel used to be described as linux-image-*, but the -image- has been removed. ex: changed linux-image-aws to linux-aws.
For this reason, the detection logic was changed.
Published by kotakanbe over 4 years ago
Display fixed-in version for each package in report
TUI

Report

JSON
fixedIn is added to affectedPackages.
"CVE-2016-9840": {
"cveID": "CVE-2016-9840",
"confidences": [
{
"score": 100,
"detectionMethod": "OvalMatch"
}
],
"affectedPackages": [
{
"name": "rsync",
"fixedIn": "3.1.2-2.1ubuntu1.1"
}
],
Published by kotakanbe about 5 years ago
You need to rm cve.sqlite3 and re-fetch NVD (and JVN) database.
Go v1.13 or later is needed to compile https://github.com/future-architect/vuls/issues/903
Changelog
3ffed18 Change GPL v3 to AGPL v3 because of aquasecurity/trivy dependency (#897)
f54e725 fix(report): fill cert alerts from NVD and JVN feeds (#899)
cc13b6a fix(report): enable to report without NVD, exit if no OVAL data (#900)
8877db1 udpate deps, go 1.13 (#901)
af58122 for Amazon Linux image (#896)
b7ca5e5 feat(scan): add -wordpress-only and -libs-only flag (#898)
69b6d87 scanVuln => GetScanResults and writeScanResults (#891)
1fbd516 fix(report): fix too many variables while reporting (#888)
dec5d3b No warning(s) in the output file with -quiet option. Report command (#885)
d5e2040 awk is useless because ps already formats the output. Also, this syntaxe isn't correct when the command is excuted on a container because of the ' . (#883)
4326bef Allow Offline scanning on Alpine (#877)
Published by kotakanbe about 5 years ago
Changelog
3d4a5d9 fix(report): Unsupport family: centos (#876)
Published by kotakanbe over 5 years ago
Changelog
d770034 fix centos yum makecache --assumeyes (#872)
a977533 Fix performance and bug (#867)
c5e13dd fix(configtest): remove yum-plugin-ps check on Amazon Linux (#870)
a8040fe fix(wordpress): add --allow-root to wp cmd for docker based wp (#865)
9e06600 fix go module problems & update trivy version (#864)
22c6601 make fmt
425464f fix(scan): allow exit 1 for no match lsof | grep (#863)
ccb0751 fix(scan): show listening ip:port of procs (#862)
f832de8 feat(saas): log.info done after uploading
8a37de0 Add ips flag to scan (#861)
Published by kotakanbe over 5 years ago
Changelog
836e470 feat(scan): Display listen port of affected procs for each vulnerable pkgs (#859)
3e53903 feat(redhat): ignore will not fix vulns (#858)
f8c0b38 feat(fast-root): get running procs for each pkgs (all RHEL, CentOS, AmazonLinux, Ubuntu, Debian) (#855)
65e6070 Fix race condition in server mode (#857)
7b78ebb retrieve ips(deep security) identifiers (#852)
Published by kotakanbe over 5 years ago
Changelog
03c3189 Changes don't required config.toml in server mode (#853)
Published by kotakanbe over 5 years ago
New features
Support Amazon Linux in server mode
#850
Conent-Type: text/plain
$ ./vuls server -listen 0.0.0.0:5515 -format-json
# test amazon linux 1
$ docker run -it --rm amazonlinux:2016.09.0.20161028 /bin/bash
$ curl -X POST -H "X-Vuls-Server-Name: local" -H "Content-Type: text/plain" -H "X-Vuls-OS-Family: amazon" -H "X-Vuls-OS-Release: 2 (Karoo)" -H "X-Vuls-Kernel-Release: 4.9.125-linuxkit" --data-binary "`rpm -qa --queryformat "%{NAME} %{EPOCHNUM} %{VERSION} %{RELEASE} %{ARCH}\n"`" http://${HOST_IP}:5515/vuls
# test amazon linux 2
$ docker run -it --rm amazonlinux:2.0.20190508 /bin/bash
$ curl -X POST -H "X-Vuls-Server-Name: local" -H "Content-Type: text/plain" -H "X-Vuls-OS-Family: amazon" -H "X-Vuls-OS-Release: 2016.09" -H "X-Vuls-Kernel-Release: 4.9.125-linuxkit" --data-binary "`rpm -qa --queryformat "%{NAME} %{EPOCHNUM} %{VERSION} %{RELEASE} %{ARCH}\n"`" http://${HOST_IP}:5515/vuls
# test ec2 amazon linux2
$ curl -X POST -H "X-Vuls-Server-Name: local" -H "Content-Type: text/plain" -H "X-Vuls-OS-Family: amazon" -H "X-Vuls-OS-Release: 2 (Karoo)" -H "X-Vuls-Kernel-Release: 4.14.121-109.96.amzn2.x86_64" --data-binary "`rpm -qa --queryformat "%{NAME} %{EPOCHNUM} %{VERSION} %{RELEASE} %{ARCH}\n"`" http://${HOST_IP}:5515/vuls
Content-Type: application/json
$ ./vuls server -listen 0.0.0.0:5515 -to-localfile -format-json
$ curl -X POST -H "Content-Type: application/json" -d '{"Family": "amazon", "Release": "2 (Karoo)", "RunningKernel": {"Release": "4.14.121-109.96.amzn2.x86_64", "Version": ""}, "Packages": {"kernel": {"Name": "kernel", "Version": "4.14.114", "Release": "105.126.amzn2", "Arch": "x86_64"}, "dracut": {"Name": "dracut", "Version": "033", "Release": "535.amzn2.1.2", "Arch": "x86_64"}}}' http://localhost:5515/vuls
Changelog
4a34dfe Support amazonlinux via http text/plain (#850)
Published by kotakanbe over 5 years ago
Vulsrepo GitHub issue moved
GitHub issue of usiusi360 no more available.
If you find a issue of usiusi360/vulsrepo, add it to future-architect/vuls.
How to Update to v0.8.0
Update Go
Go over v1.12 needed.
Compile error will be occurred with Go under v11.
update and re-fetch with a new database
- goval-dictionary
- go-cve-dictinoary
- Vuls
New features
Container Image Scan
https://github.com/future-architect/vuls/pull/829
[servers]
[servers.image]
type="pseudo"
# GCR
[servers.image.images.hyperkube]
name="gcr.io/google-containers/hyperkube"
tag="v1.11.10"
# Local
[servers.image.images.web-dvwa]
name="vulnerables/web-dvwa"
tag="latest"
# Local
[servers.image.images.gcr]
name="asia.gcr.io/bizshift-stg/api"
tag="latest"
[servers.image.images.gcr.dockerOption]
gcpCredPath="/Users/amachi/Downloads/key.json"
Smart Programming Language Library Scan
https://github.com/future-architect/vuls/pull/829
[servers]
[servers.abuntu]
host = "xxx.xxx.xxx"
port = "22"
user = "tamachi"
keyPath = "/Users/amachi/.ssh/id_dsa"
findLock = true # auto detect lockfile
lockfiles = [
"/home/tamachi/lockfiles/package-lock.json"
"/home/tamachi/lockfiles/yarn.lock"
]
Speed up Oval Reporting
https://github.com/future-architect/vuls/pull/834
| os | before | after |
|---|---|---|
| alpine3.9 | over 1hour | 0.26s |
| Ubuntu | 180s | 3s |
Support Amazon OVAL Scan
https://github.com/future-architect/vuls/pull/824
Support OVAL scanning for Amazon Linux 1/2.
You should update to the latest version of goval-dictionary and fetch-amazon
$ goval-dictionary fetch-amazon
see also
- https://github.com/kotakanbe/goval-dictionary/pull/63
- https://github.com/kotakanbe/goval-dictionary#usage-fetch-amazon-alas-as-oval-data-type
Support RHEL8
You have to fetch RedHat OVAL before reporting.
To fetch
$ goval-dictionary fetch-redhat 5 6 7 8
see
- https://github.com/kotakanbe/goval-dictionary#usage-fetch-oval-data-from-redhat
- https://github.com/future-architect/vuls/pull/813
Bug Fix
- fix(scan): false negative of kernel related vulns on Ubuntu 16 #819
- fix(scan): a bug of kernel Vulns detection on Ubuntu18
- fix(report): Critical Bug Fix for CPE based scanning
- fix(report): fix the number of fixed/total in reporting
Changelog
4cf9a72 set GO111MODULE=on in .goreleaser.yml
bd1b135 Add vulsrepo issue template
8c3b305 fix(readme): typo in news (#841)
a371903 fix(scan): scan Amazon Linux with offline mode (#840)
c68a261 Update README.md
75fea79 feat(scan): Support RHEL8 (#813)
eb9f968 refactor(scan): remove yum-security related code (#836)
3634afd enhance issue_template (#837)
77b5df8 update goval-dictionary dependency to valid version (#839)
b81f640 fix(report): remove extra check logic #802 (#835)
a8a90d7 refactor(report): speed up oval reporting #833 (#834)
17bb575 fix(scan): enable to report if some warnings occured on scanning (#805)
abcea1a add Library Scan (with image scan) (#829)
10942f7 fix(scan): fetch only updatable package changelogs (#815)
87ee829 fix(scan): exec yum makecache to update metadata on RedHat based linux (#810)
fcc2c1e Changing the scannedAt time in the original result (#823)
269095d feat(report): support Amazon OVAL scanning (#824)
40492ee fix typos, extraneous text (#831)
64cdd5a fix(report): WordPress(WPVULNDB API) 429 Too Many Requests (#826)
3bb650c fix(report-redhat): fix false negative of affected vulns #827 (#828)
774544c fix(report): warning only if the kernel version is unknown (#822)
299805a [WIP]fix(scan): false negative of kernel related vulns on Ubuntu 16 (#819)
276363e fix(scan): a bug of kernel Vulns detection on Ubuntu18 (#818)
e750bd5 fix(report): fix the number of fixed/total in reporting (#817)
98fee7b Implement Vuls's own error code (#812)
53aaea9 add scannedVia field to know the way of access such as SSH, local or pseudo (#811)
824fbb6 Updated config.toml reference url (#809)
80566b9 fix(report): exit 1 when scan result has errors (#804)
533d05a fix(report): Error when GitHub integration failed (#800)
Published by kotakanbe over 5 years ago
New Features
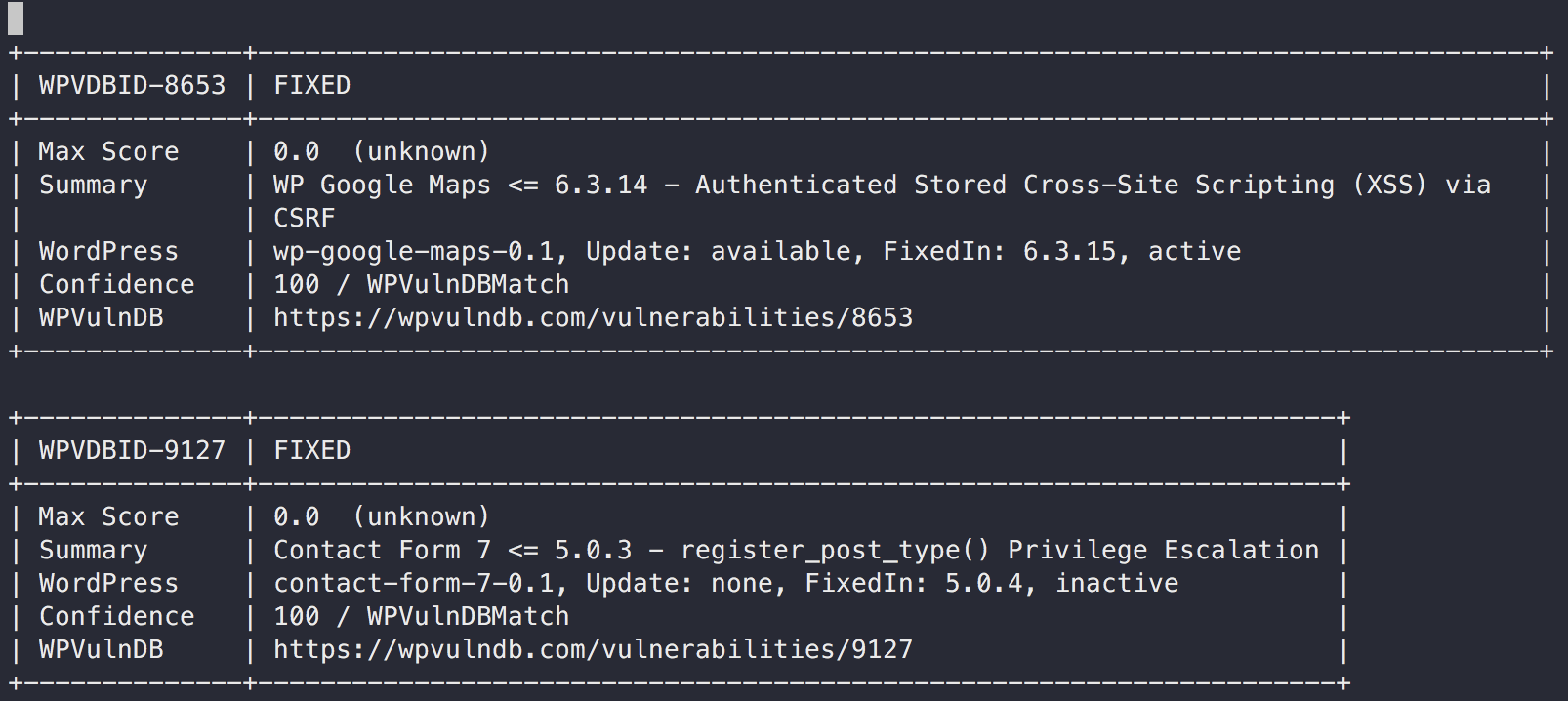
WordPress Vulnerability Scan (core, plugin, theme)
For non-commercial use, you can use this WordPress integration for free.
But for commercial use, You have to send a E-Mail to the WPVulnDB team.
For Details, see the NOTE:
If you are under any doubt if your software is classed as non-commercial and/or would like to inquire about commercial usage of our databases get in touch.
First, you need to register a user and get the API token from your profile page on wpvulndb.com.
And then, check whether the wp command is insatalled on the scan target server.
A sample configuration is below.
- config.toml
[servers.kusanagi]
user = "root"
host = "10.10.10.10"
port = "22"
[servers.kusanagi.wordpress]
cmdPath = "/usr/local/bin/wp"
osUser = "wordpress"
docRoot = "/home/kusanagi/wp/DocumentRoot/"
wpVulnDBToken = "xxxxTokenxxxx"
ignoreInactive = false
- cmdPath: A path of
wp-clion the WordPress server - osUser: A OS user of
wp-clion the WordPress server - docRoot: A path of document root on the WordPress server
- wpVulnDBToken: A token of WPVULNDB API
- ignoreInactive: Ignore plugins or themes which are inactive state
Scan
To scan WordPress, execute as below.
$ vuls scan kusanagi
Vuls collects WordPrss Core version, plugins and themes via wp-cli.
Reporting
$ vuls report
Vuls detects vulnerabilities via accessing WPVulnDB.com via HTTP.
- Slack


- TUI

- Full-Text
Changelog
6a1fc4f Merge branch 'master' of https://github.com/future-architect/vuls
9008d0d Add news to readme
583f457 fix goreleaser.yml
e5716d5 Add news to readme
7192ae1 Bump up version
99c65ef feat(scan): WordPress Vulnerability Scan (core, plugin, theme) (#769)
91df593 Editorial fixes (#798)
07aeaeb update go-exploitdb (#797)
cfeecda update pkgs (#796)
564dfa8 update cve dictionary (#795)
75dd6f2 Specify VOLUME using json syntax (#791)
e26fd0b fix(report): Critical Bug Fix for CPE based scanning #793 (#794)
d630680 feat(slack): enable -format-one-line-text with -to-slack (#792)
1723c3f fix(report): cpe match bug: go-cve-dictionary#120 (#790)
53dd903 fix(scan): parse error on SUSE #515 (#786)
5c6e06b Handle no-auth SMTP Servers and one liner email fix (#772)
cf6fb0c models: fix no-op append calls (#785)
e0e71b2 add scanner info in -to-saas (#783)
53f4a29 change implemention of integration (#780)



