
hydra
OpenID Certified™ OpenID Connect and OAuth Provider written in Go - cloud native, security-first, open source API security for your infrastructure. SDKs for any language. Works with Hardware Security Modules. Compatible with MITREid.
APACHE-2.0 License
Bot releases are visible (Hide)
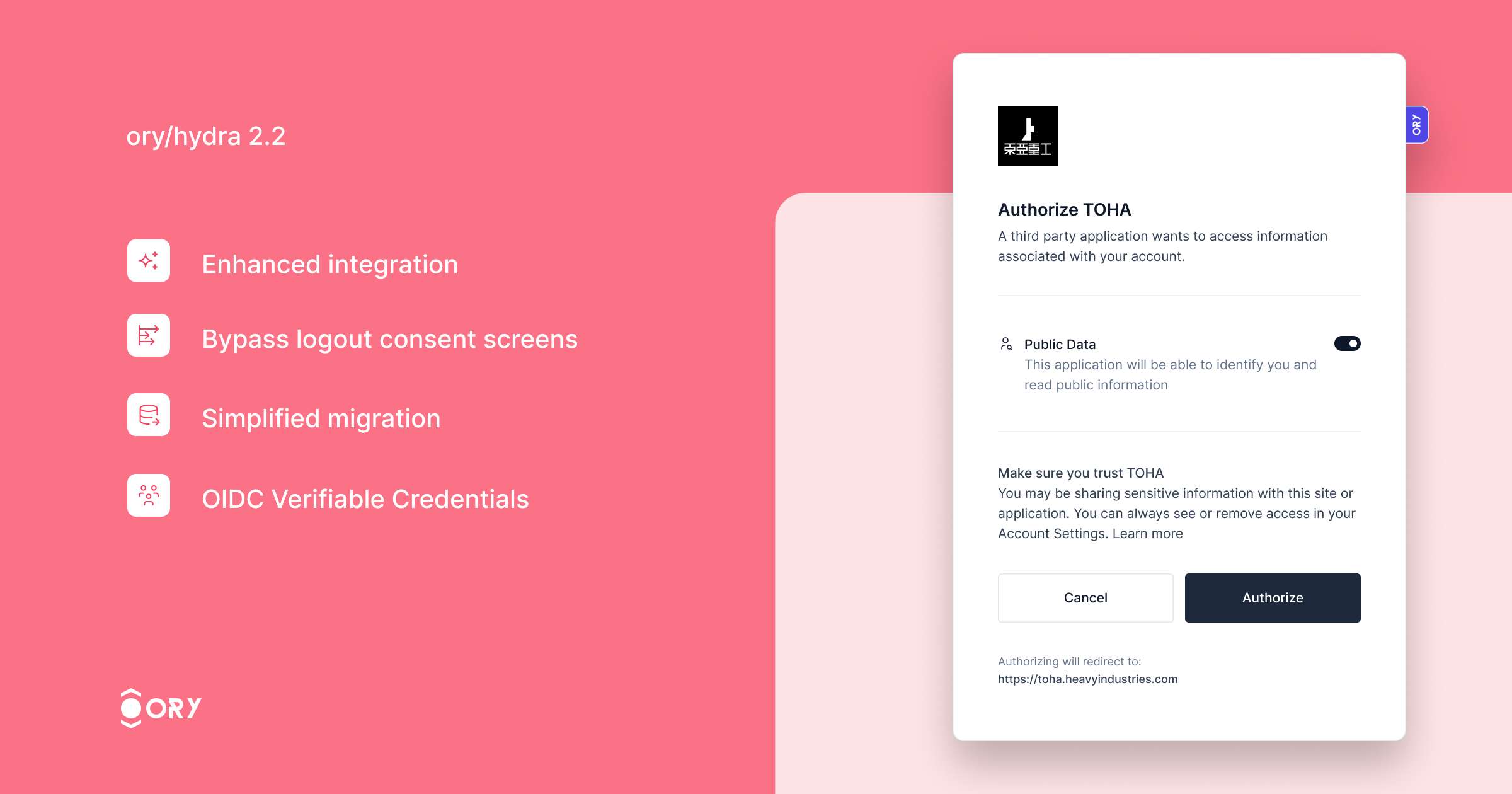
Ory Hydra, the OAuth2 and OpenID Connect server designed for web-scale deployments introduces over 6x higher OAuth2 throughput on a single PostgreSQL instance!
Want to check out Ory Hydra yourself? Try common OAuth2 flows in the Ory OAuth2 Get Started guide!
This version significantly enhances performance, processing over 6x more authorization flows than version 2.1, thanks to architectural improvements that minimize database interactions for login and consent processes.
Key improvements include:
- Enhanced integration with Ory Kratos, ensuring seamless synchronization of login and logout states across both services. Users logged out from Ory Hydra will automatically log out from Ory Kratos, enhancing security and user experience.
- The ability to bypass the logout consent screen for specific clients, streamlining the logout process.
- Simplified migration with the new feature to import OAuth2 Client IDs, making the transition to Ory Hydra smoother.
- Support for the OIDC Verifiable Credentials specification, expanding the server's capabilities in identity verification.
Thank all contributors who have made this release available!
Bug Fixes
-
Return empty slice if requested_scope or audience is null (#3711) (65165e7)
-
Correct id token type in token exchange response (#3625) (d1f9ba8):
-
Handle subject mismatch gracefully (#3619) (af0d477):
We now redirect to the original request URL if the subjects between
the remembered Hydra session and what was confirmed by the login
screen does not match. -
Handle token hook auth config (#3677) (1a40833):
- fix: handle token hook auth config
- fix: bump golangci-lint
-
Incorrect down migration (#3708) (8812e0e), closes /github.com/ory/hydra/pull/3705#discussion_r1471514014
-
Timeout in jwt-bearer grants when too many grants are available (#3692) (a748797)
-
Deflake ttl test (6741a49)
-
Only query access tokens by hashed signature (a21e945)
-
Reject invalid JWKS in client configuration / dependency cleanup and bump (#3603) (1d73d83)
-
Restore ability to override auth and token urls for exemplary app (#3590) (dfb129a)
-
Return proper error when the grant request cannot be parsed (#3558) (26f2d34)
Documentation
Features
-
Add prompt=registration (#3636) (19857d2):
Ory Hydra now supports a
registrationvalue for thepromptparameter of
the authorization request. When specifyingprompt=registration, Ory Hydra
will redirect the user to the URL found underurls.registration
(instead ofurls.login). -
Add skip_logout_consent option to clients (#3705) (2a653e6):
Adds a special field which disables the logout consent screen when performing OIDC logout.
-
Re-enable legacy client IDs (#3628) (5dd7d30):
This patch changes the primary key of the
hydra_clienttable. We do not expect issues, as that table is probably not overly huge in any deployment. We do however highly recommend to test the migration performance on a staging environment with a similar database setup. -
Remove flow cookie (#3639) (cde3a30):
This patch removes the flow cookie. All information is already tracked in the request query parameters as part of the {login|consent}_{challenge|verifier}.
-
Remove login session cookie during consent flow (#3667) (5f41949)
-
Add more resolution to events and collect client metrics (#3568) (466e66b)
-
Add state override (b8b9154)
-
Add support for OIDC VC (#3575) (219a7c0):
This adds initial support for issuing verifiable credentials
as specified in https://openid.net/specs/openid-connect-userinfo-vc-1_0.html.Because the spec is still in draft, public identifiers are
suffixed withdraft_00. -
Allow to disable claim mirroring (#3563) (c72a316):
This PR introduces another config option called
oauth2:mirror_top_level_claimswhich may be used to disable the mirroring of custom claims into theextclaim of the jwt.
This new config option is an opt-in. If unused the behavior remains as-is to ensure backwards compatibility.Example:
oauth2: allowed_top_level_claims: - test_claim mirror_top_level_claims: false # -> this will prevent test_claim to be mirrored within ext -
Bump fosite and add some more tracing (0b56f53)
-
cmd: Add route that redirects to the auth code url (4db6416)
-
Propagate logout to identity provider (#3596) (c004fee):
- feat: propagate logout to identity provider
This commit improves the integration between Hydra and Kratos when logging
out the user.This adds a new configuration key for configuring a Kratos admin URL.
Additionally, Kratos can send a session ID when accepting a login request.
If a session ID was specified and a Kratos admin URL was configured,
Hydra will disable the corresponding Kratos session through the admin API
if a frontchannel or backchannel logout was triggered.- fix: add special case for MySQL
- chore: update sdk
- chore: consistent naming
- fix: cleanup persister
-
Support different jwt scope claim strategies (#3531) (45da11e)
Changelog
- b346f90e autogen(docs): generate and bump docs
- 01aeffc6 autogen(docs): regenerate and update changelog
- 3a65840d autogen(docs): regenerate and update changelog
- 2dc52b4d autogen(docs): regenerate and update changelog
- 74732591 autogen(docs): regenerate and update changelog
- 4b8c9715 autogen(docs): regenerate and update changelog
- d0dfc0f0 autogen(docs): regenerate and update changelog
- 9e9be2d2 autogen(docs): regenerate and update changelog
- ada59a5f autogen(docs): regenerate and update changelog
- cdd2647c autogen(docs): regenerate and update changelog
- e4c160f5 autogen(docs): regenerate and update changelog
- 5121dba3 autogen(docs): regenerate and update changelog
- 21e0a9bd autogen(docs): regenerate and update changelog
- 89b1b1bd autogen(docs): regenerate and update changelog
- 0a5e0439 autogen(docs): regenerate and update changelog
- 6cbe0893 autogen(docs): regenerate and update changelog
- 78617027 autogen(docs): regenerate and update changelog
- c9f4b5f3 autogen(docs): regenerate and update changelog
- fe260d10 autogen(docs): regenerate and update changelog
- fbf39dd3 autogen(docs): regenerate and update changelog
- 9b33fc55 autogen(docs): regenerate and update changelog
- f9cee328 autogen(docs): regenerate and update changelog
- 841d58b8 autogen(docs): regenerate and update changelog
- 4a8e9a4c autogen(docs): regenerate and update changelog
- cdc0bec3 autogen(openapi): regenerate swagger spec and internal client
- 4a00e3e0 autogen(openapi): regenerate swagger spec and internal client
- dedcf5b4 autogen(openapi): regenerate swagger spec and internal client
- 92eb03a0 autogen(openapi): regenerate swagger spec and internal client
- f9a87d35 autogen(openapi): regenerate swagger spec and internal client
- 1ff8f20a autogen(openapi): regenerate swagger spec and internal client
- 11bf9df8 autogen(openapi): regenerate swagger spec and internal client
- e7968931 autogen(openapi): regenerate swagger spec and internal client
- 27f2ef50 autogen(openapi): regenerate swagger spec and internal client
- 35d62950 autogen(openapi): regenerate swagger spec and internal client
- ce00a428 autogen(openapi): regenerate swagger spec and internal client
- db4fd7d1 autogen(openapi): regenerate swagger spec and internal client
- 146b1625 autogen(openapi): regenerate swagger spec and internal client
- e1636d1e autogen(openapi): regenerate swagger spec and internal client
- 9389773a autogen(openapi): regenerate swagger spec and internal client
- af859fe4 autogen(openapi): regenerate swagger spec and internal client
- f1708f2a autogen(openapi): regenerate swagger spec and internal client
- 3e8413e9 autogen(openapi): regenerate swagger spec and internal client
- 11c8c724 autogen(openapi): regenerate swagger spec and internal client
- 800ce0a1 autogen: add v2.2.0-rc.3 to version.schema.json
- 8168ee31 autogen: pin v2.2.0-pre.1 release commit
- 04872174 autogen: render config schema
- a0c06ecb chore(deps): bump @cypress/request and cypress (#3641)
- b177f81a chore(deps): bump axios and @openapitools/openapi-generator-cli (#3701)
- 23c81943 chore(deps): bump debug from 3.2.6 to 3.2.7 (#3640)
- 18d97936 chore(deps): bump follow-redirects in /test/e2e/oauth2-client (#3697)
- 4fa28890 chore(deps): bump github.com/docker/docker (#3707)
- 2ba35473 chore(deps): bump golang.org/x/crypto from 0.15.0 to 0.17.0 (#3680)
- efc00a8b chore(deps): bump golang.org/x/net from 0.14.0 to 0.17.0 (#3645)
- 083c90de chore: build tag (#3613)
- 3615e3df chore: bump docker base images (#3632)
- aa8a364e chore: bump openapi-generator (#3696)
- 2dc66061 chore: improve context (#3656)
- 8e949299 chore: update otel (#3686)
- f0501d2c docs: fix typo (#3649)
- f502d6e3 feat: add --skip-logout-consent flag to CLI (#3709)
- 5c8e7923 feat: add authentication options to hooks (#3633)
- 62c006b9 feat: add flag to export public keys (#3684)
- 39ee5e1f feat: add missing index for jwk table (#3691)
- 19857d20 feat: add prompt=registration (#3636)
- 2a653e66 feat: add skip_logout_consent option to clients (#3705)
- 88b0b7cf feat: allow injecting extra fosite strategies (#3646)
- 5dd7d306 feat: re-enable legacy client IDs (#3628)
- cde3a30a feat: remove flow cookie (#3639)
- 5f41949a feat: remove login session cookie during consent flow (#3667)
- 95cc2735 feat: support multiple token URLs (#3676)
- d1f9ba8e fix: correct id token type in token exchange response (#3625)
- 22f0119a fix: dropped persistence/sql test errors (#3670)
- 5133cf97 fix: handle logout double-submit gracefully (#3675)
- af0d477e fix: handle subject mismatch gracefully (#3619)
- 1a40833e fix: handle token hook auth config (#3677)
- 24c3be57 fix: improved SSRF protection (#3669)
- 8812e0e6 fix: incorrect down migration (#3708)
- 3a764a05 fix: remove required mark (#3693)
- a7487977 fix: timeout in jwt-bearer grants when too many grants are available (#3692)
- 0176adc1 fix: verifiable credentials JWT format (#3614)
- 8e6c4bfa autogen(docs): regenerate and update changelog
- 33950db8 autogen(docs): regenerate and update changelog
- 28e9e31b autogen(openapi): regenerate swagger spec and internal client
- 57096be9 autogen: pin v2.2.0 release commit
- bfc05d00 chore(deps): bump github.com/opencontainers/runc from 1.1.8 to 1.1.12 (#3710)
- 65165e77 fix: return empty slice if requested_scope or audience is null (#3711)
Artifacts can be verified with cosign using this public key.
Published by ory-bot about 1 year ago
Introduces logout compatibility with Ory Kratos.
Bug Fixes
- Add exceptions for internal IP addresses (#3608) (1f1121c)
- Add kid to verifiable credential header (#3606) (9f1c8d1)
- Deflake ttl test (6741a49)
- Docker build (#3609) (01ff9da)
- Enable CORS with hot-reloaded origins (#3601) (6f592fc)
- Only query access tokens by hashed signature (a21e945)
- Racy random string generation (#3555) (1b26c4c)
- Reject invalid JWKS in client configuration / dependency cleanup and bump (#3603) (1d73d83)
- Restore ability to override auth and token urls for exemplary app (#3590) (dfb129a)
- Return proper error when the grant request cannot be parsed (#3558) (26f2d34)
- Use correct tracer in middleware (#3567) (807cbd2)
Code Generation
- Pin v2.2.0-rc.3 release commit (ad8a4ba)
Features
-
Add more resolution to events and collect client metrics (#3568) (466e66b)
-
Add state override (b8b9154)
-
Add support for OIDC VC (#3575) (219a7c0):
This adds initial support for issuing verifiable credentials
as specified in https://openid.net/specs/openid-connect-userinfo-vc-1_0.html.Because the spec is still in draft, public identifiers are
suffixed withdraft_00. -
Allow to disable claim mirroring (#3563) (c72a316):
This PR introduces another config option called
oauth2:mirror_top_level_claimswhich may be used to disable the mirroring of custom claims into theextclaim of the jwt.
This new config option is an opt-in. If unused the behavior remains as-is to ensure backwards compatibility.Example:
oauth2: allowed_top_level_claims: - test_claim mirror_top_level_claims: false # -> this will prevent test_claim to be mirrored within ext -
Bump fosite and add some more tracing (0b56f53)
-
cmd: Add route that redirects to the auth code url (4db6416)
-
Propagate logout to identity provider (#3596) (c004fee):
- feat: propagate logout to identity provider
This commit improves the integration between Hydra and Kratos when logging
out the user.This adds a new configuration key for configuring a Kratos admin URL.
Additionally, Kratos can send a session ID when accepting a login request.
If a session ID was specified and a Kratos admin URL was configured,
Hydra will disable the corresponding Kratos session through the admin API
if a frontchannel or backchannel logout was triggered.- fix: add special case for MySQL
- chore: update sdk
- chore: consistent naming
- fix: cleanup persister
-
Support different jwt scope claim strategies (#3531) (45da11e)
Changelog
- 2c452efd autogen(docs): regenerate and update changelog
- 551c359d autogen(docs): regenerate and update changelog
- 93ebaee6 autogen(docs): regenerate and update changelog
- 7cfba846 autogen(docs): regenerate and update changelog
- cb647702 autogen(docs): regenerate and update changelog
- 938d4bba autogen(docs): regenerate and update changelog
- 0072ddf7 autogen(docs): regenerate and update changelog
- c30de7f8 autogen(docs): regenerate and update changelog
- 6c298b2f autogen(docs): regenerate and update changelog
- a547a749 autogen(docs): regenerate and update changelog
- 5704640c autogen(docs): regenerate and update changelog
- e586cc2c autogen(docs): regenerate and update changelog
- 2bdad2c2 autogen(docs): regenerate and update changelog
- dc878b82 autogen(docs): regenerate and update changelog
- 425c977a autogen(docs): regenerate and update changelog
- 339bf40e autogen(docs): regenerate and update changelog
- ea40d443 autogen(docs): regenerate and update changelog
- 71d18536 autogen(docs): regenerate and update changelog
- be85c29a autogen(docs): regenerate and update changelog
- 598c21d7 autogen(docs): regenerate and update changelog
- 42a9615a autogen(docs): regenerate and update changelog
- 330530d7 autogen(openapi): regenerate swagger spec and internal client
- 254a21b2 autogen(openapi): regenerate swagger spec and internal client
- ad8a4bab autogen: pin v2.2.0-rc.3 release commit
- 6631c213 autogen: render config schema
- 59ec76ba chore(deps): bump semver from 5.7.0 to 5.7.2 (#3569)
- 9fd59e2b chore(deps): bump semver from 5.7.0 to 5.7.2 in /test/e2e/oauth2-client (#3570)
- 3c5c1265 chore(deps): bump tough-cookie, @cypress/request and wait-on (#3592)
- 48d5df43 chore: add hperl as codeowner (#3607)
- efd9ca7d chore: bump deps (#3560)
- d5099cbb chore: remove fosite branch override (#3599)
- 39145855 chore: replace fosite rewrite (#3564)
- 8ed2a2d3 chore: support in README (#3565)
- 1a1f5044 chore: update repository templates to https://github.com/ory/meta/commit/ac80097fa427e7ae39820c59cac62dc6e11b9aff
- eb89af7c chore: update repository templates to https://github.com/ory/meta/commit/af28aff50b62a9eeb69de4842e0e164f82c9e066
- 4db64161 feat(cmd): add route that redirects to the auth code url
- 749eb8db feat: add
hydra migrate statussubcommand (#3579) - 466e66bd feat: add more resolution to events and collect client metrics (#3568)
- b8b91540 feat: add state override
- 219a7c06 feat: add support for OIDC VC (#3575)
- 8eed3068 feat: allow Go migrations (#3602)
- 8900cbb7 feat: allow additional SQL migrations (#3587)
- c72a3164 feat: allow to disable claim mirroring (#3563)
- 0b56f53a feat: bump fosite and add some more tracing
- 5bd9002d feat: parallel generation of JSON web key set (#3561)
- c004fee6 feat: propagate logout to identity provider (#3596)
- 45da11e4 feat: support different jwt scope claim strategies (#3531)
- 1f1121ca fix: add exceptions for internal IP addresses (#3608)
- 9f1c8d19 fix: add kid to verifiable credential header (#3606)
- 6741a49f fix: deflake ttl test
- 01ff9da8 fix: docker build (#3609)
- 6f592fc8 fix: enable CORS with hot-reloaded origins (#3601)
- a21e9451 fix: only query access tokens by hashed signature
- 1b26c4cb fix: racy random string generation (#3555)
- 1d73d83e fix: reject invalid JWKS in client configuration / dependency cleanup and bump (#3603)
- dfb129a5 fix: restore ability to override auth and token urls for exemplary app (#3590)
- 26f2d344 fix: return proper error when the grant request cannot be parsed (#3558)
- 807cbd20 fix: use correct tracer in middleware (#3567)
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 1 year ago
Test release
Code Generation
- Pin v2.2.0-pre.0 release commit (116c1e8)
Features
Changelog
- be99edea autogen(docs): generate and bump docs
- 4877c59d autogen(docs): regenerate and update changelog
- 4b4c033e autogen(docs): regenerate and update changelog
- d4ad1073 autogen: add v2.2.0-rc.2 to version.schema.json
- 116c1e89 autogen: pin v2.2.0-pre.0 release commit
- 6a0be838 autogen: render config schema
- 47582578 chore: bump ory/x
- c1e1a569 feat: add distroless docker image (#3539)
- 44ed0ac8 feat: add event tracing (#3546)
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 1 year ago
This release optimizes the performance of authorization code grant flows by minimizing the number of database queries. We acheive this by storing the flow in an AEAD-encoded cookie and AEAD-encoded request parameters for the authentication and consent screens.
BREAKING CHANGE:
- The client that is used as part of the authorization grant flow is stored in the AEAD-encoding. Therefore, running flows will not observe updates to the client after they were started.
- Because the login and consent challenge values now include the AEAD-encoded flow, their size increased to around 1kB for a flow without any metadata (and increases linearly with the amount of metadata). Please adjust your ingress / gateway accordingly.
Bug Fixes
- Version clash in apk install (24ebdd3)
Code Generation
- Pin v2.2.0-rc.2 release commit (b183040)
Features
Changelog
- 4194d750 autogen(docs): regenerate and update changelog
- 898aa001 autogen(docs): regenerate and update changelog
- b183040a autogen: pin v2.2.0-rc.2 release commit
- a8ecf807 feat: hot-reload Oauth2 CORS settings (#3537)
- 3ec683d7 feat: sqa metrics v2 (#3533)
- 24ebdd3f fix: version clash in apk install
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 1 year ago
We are excited to announce the next Ory Hydra release! This release includes the following important changes:
- Fixed a memory leak in the OpenTelemetry implementation, improving overall memory usage and stability.
- Added a missing index for faster janitor cleanup, resulting in quicker and more efficient cleanup operations.
- Fixed a bug related to SameSite in dev mode, ensuring proper functionality and consistency in handling SameSite attributes during development.
We appreciate your continuous support and feedback. Please feel free to reach out to us with any further suggestions or issues.
Bug Fixes
-
Add index on requested_at for refresh tokens and use it in janitor (#3516) (5b8e712)
-
Do not use prepared SQL statements and bump deps (#3506) (31b9e66)
-
sql: Incorrect JWK query (#3499) (13ce0d6):
persister_grant_jwkhad an OR statement without bracket leading to not using the last part of the query.
Code Generation
- Pin v2.1.2 release commit (d94ed6e)
Documentation
Features
Changelog
- 0e84c241 autogen(docs): generate and bump docs
- 9f371723 autogen(docs): regenerate and update changelog
- 872720b3 autogen(docs): regenerate and update changelog
- 49072237 autogen(docs): regenerate and update changelog
- ba45af00 autogen(docs): regenerate and update changelog
- 3703e5a7 autogen(docs): regenerate and update changelog
- ca85a170 autogen(docs): regenerate and update changelog
- 0e7e95fc autogen(docs): regenerate and update changelog
- be8f7266 autogen: add v2.1.1 to version.schema.json
- d94ed6e4 autogen: pin v2.1.2 release commit
- 20c6fa76 autogen: render config schema
- 400b9af0 chore(deps): bump @nestjs/core and @openapitools/openapi-generator-cli (#3493)
- f2f007db chore(deps): bump github.com/docker/distribution (#3514)
- b69a332b chore: bump ory/x (#3518)
- cf20054f chore: remove unneeded dependency (#3494)
- e2b7665c chore: update nodemon version for oauth2 client (#3503)
- b71a36bf docs: incorrect json output format example (#3497)
- 083d518c feat: add --skip-consent flag to hydra cli (#3492)
- 13ce0d6f fix(sql): incorrect JWK query (#3499)
- 5b8e7121 fix: add index on requested_at for refresh tokens and use it in janitor (#3516)
- eddf7f38 fix: disable health check request logs (#3496)
- 31b9e663 fix: do not use prepared SQL statements and bump deps (#3506)
- 5751fae7 fix: proper SameSite=None in dev mode (#3502)
- 1b1899e9 fix: sqa config values unified across projects (#3490)
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 1 year ago
We are excited to share this year's Q1 release of Ory Hydra: v2.1!
Highlights:
- Support for Datadog tracing (#3431).
- Ability to skip consent for trusted clients (#3451).
- Setting access token type in the OAuth2 Client is now possible (#3446).
- Revoke login sessions by SessionID (#3450).
- Session lifespan extended on session refresh (#3464).
- Token request hooks added for all grant types (#3427).
- Reduced SQL tracing noise (#3481).
Don't want to run the upgrade yourself? Switch to Ory Network!
Bug Fixes
- Double-hashed access token signatures (#3486) (8720b25), closes #3485
- Reduce SQL tracing noise (#3481) (6e1f545)
Code Generation
- Pin v2.1.1 release commit (6efae7c)
Changelog
- df16a26c autogen(docs): generate and bump docs
- ed2ac06b autogen(docs): regenerate and update changelog
- 6078f85a autogen(docs): regenerate and update changelog
- ddfbd659 autogen: add v2.1.0 to version.schema.json
- 6efae7cf autogen: pin v2.1.1 release commit
- ad549d61 autogen: pin v2.1.1 release commit
- 2f7cda5f autogen: render config schema
- 0448284f chore: update ory/x (#3480)
- 8720b250 fix: double-hashed access token signatures (#3486)
- 6e1f5454 fix: reduce SQL tracing noise (#3481)
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 1 year ago
We are excited to share this year's Q1 release of Ory Hydra: v2.1.0!
Highlights:
- Support for Datadog tracing (#3431).
- Ability to skip consent for trusted clients (#3451).
- Setting access token type in the OAuth2 Client is now possible (#3446).
- Revoke login sessions by SessionID (#3450).
- Session lifespan extended on session refresh (#3464).
- Token request hooks added for all grant types (#3427).
- Reduced SQL tracing noise (#3481).
Don't want to run the upgrade yourself? Switch to Ory Network!
Bug Fixes
Code Generation
- Pin v2.1.0 release commit (3649832)
Changelog
- 5c2e2271 autogen(docs): regenerate and update changelog
- 36498324 autogen: pin v2.1.0 release commit
- 6e1f5454 fix: reduce SQL tracing noise (#3481)
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 1 year ago
autogen: pin v2.1.0-pre.2 release commit
Code Generation
- Pin v2.1.0-pre.2 release commit (3b1d87e)
Changelog
- 3b1d87e3 autogen: pin v2.1.0-pre.2 release commit
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 1 year ago
autogen: pin v2.1.0-pre.1 release commit
Code Generation
- Pin v2.1.0-pre.1 release commit (2289e6b)
Changelog
- 2289e6b8 autogen: pin v2.1.0-pre.1 release commit
- 0d740d9d chore(deps): bump github.com/opencontainers/runc from 1.1.4 to 1.1.5 (#3476)
- c29b9680 chore: update alpine version
Artifacts can be verified with cosign using this public key.
Published by ory-bot almost 2 years ago
Bugfixes for migration and pagination regressions and a new endpoint.
Bug Fixes
-
Add
client_idandclient_secrettorevokeOAuth2Token(#3373) (93bac07) -
Docker build (48217bd)
-
Invalidate tokens with inconsistent state (#3385) (542ea77), closes #3346:
This patch includes SQL migrations targeting environments which have not yet migrated to Ory Hydra 2.0. It removes inconsistent records which resolves issues during the migrations process. Please be aware that some users might be affected by this change. They might need to re-authorize certain apps. However, most active records should not be affected by this.
Installations already on Ory Hydra 2.0 will not be affected by this change.
-
No longer auto-generate system secret (c5fe043):
This patch changes Ory Hydra's behavior to no longer auto-generate a temporary secret when no global secret was set. The APIs now return an error instead.
-
Prevent multiple redirections to post logout url (#3366) (50666b9), closes #3342
Code Generation
- Pin v2.0.3 release commit (16831c5)
Features
Changelog
- 5d79e57a autogen(docs): generate and bump docs
- bd190868 autogen(docs): regenerate and update changelog
- 2720839b autogen(docs): regenerate and update changelog
- a400a354 autogen(docs): regenerate and update changelog
- 6710ddc4 autogen(docs): regenerate and update changelog
- d7a28e94 autogen(docs): regenerate and update changelog
- f2925ee4 autogen(docs): regenerate and update changelog
- 2986605e autogen(docs): regenerate and update changelog
- c586e035 autogen(openapi): regenerate swagger spec and internal client
- c65342e2 autogen: add v2.0.2 to version.schema.json
- 16831c55 autogen: pin v2.0.3 release commit
- b28bad38 chore(deps): bump decode-uri-component in /test/e2e/oauth2-client (#3377)
- cb23cca0 chore(deps): bump minimatch in /test/e2e/oauth2-client (#3381)
- 93fc0a1b chore(deps): bump qs from 6.5.2 to 6.5.3 (#3380)
- 316b5820 chore(deps): bump qs, body-parser and express in /test/e2e/oauth2-client (#3379)
- f9f0337f chore: list contributors in file (#3345)
- d275ad66 feat: list consent sessions by session id (#2853)
- 93bac074 fix: add
client_idandclient_secrettorevokeOAuth2Token(#3373) - 48217bd2 fix: docker build
- 4ee4456d fix: introspect command CLI example (#3353)
- 542ea771 fix: invalidate tokens with inconsistent state (#3385)
- c5fe0433 fix: no longer auto-generate system secret
- 50666b96 fix: prevent multiple redirections to post logout url (#3366)
- 3831b448 fix: strip
publicfrom schema (#3374) - e8d8de90 fix: token pagination (#3384)
Artifacts can be verified with cosign using this public key.
Published by ory-bot almost 2 years ago
This release resolves bugs and SDK publishing issues.
Bug Fixes
-
Correct migration file name (01f80a8)
-
Incorrect consent removal on authentication revokation (ccf2388):
This patch resolves a regression where, in a certain condition, an accepted consent could be incorrectly deleted when the related authentication session was removed.
-
Isolate transactions for crdb (f22046f)
-
Scope type should be string instead of int (#3337) (f59f1c6):
Code Generation
- Pin v2.0.2 release commit (ce96826)
Documentation
- Add refresh token grant type (c752125)
- Fix typo (dcfd11f)
- Standardize license headers (#3216) (d768cf6)
- Update README link (6184b6a)
Features
Tests
Changelog
- 94aadf83 autogen(docs): generate and bump docs
- 0eeea900 autogen(docs): regenerate and update changelog
- 8d92030a autogen(docs): regenerate and update changelog
- 48603bac autogen(docs): regenerate and update changelog
- bedaf486 autogen(docs): regenerate and update changelog
- 3749a736 autogen(docs): regenerate and update changelog
- cec489fe autogen(docs): regenerate and update changelog
- d37b3234 autogen(docs): regenerate and update changelog
- cdfcf451 autogen(docs): regenerate and update changelog
- 70e6fe9c autogen(docs): regenerate and update changelog
- 4fd6baaf autogen(docs): regenerate and update changelog
- fd020496 autogen(openapi): regenerate swagger spec and internal client
- 74d4569a autogen(openapi): regenerate swagger spec and internal client
- 164f4b5f autogen: add v2.0.1 to version.schema.json
- ce968261 autogen: pin v2.0.2 release commit
- 80a1335b chore: license checker (#3328)
- f8a7ced6 chore: remove obsolete header (#3334)
- 90152fab chore: update Ory CLI with breaking changes to the format task (#3338)
- 0b322806 chore: update repository templates to https://github.com/ory/meta/commit/852a1aece5fefac0a03f928672538c5d8c536ad8
- cda9fd42 chore: update repository templates to https://github.com/ory/meta/commit/a2fba7e968572391ac4a55ce362dca0c4800c97d
- 54184337 chore: update repository templates to https://github.com/ory/meta/commit/b41b1ee5ed62f47bac563014929c64bff0c14163
- 736aaefb chore: update repository templates to https://github.com/ory/meta/commit/d3f8710e356fb833d4bd71b4ba19d062df2ea89e
- c7521253 docs: add refresh token grant type
- dcfd11f0 docs: fix typo
- d768cf65 docs: standardize license headers (#3216)
- 6184b6a0 docs: update README link
- 16bd568f feat: enable simultaneous auth flows by creating client related csrf co… (#3059)
- c54b9dbf fix: add v2 suffix (#3340)
- 01f80a85 fix: correct migration file name
- ccf23886 fix: incorrect consent removal on authentication revokation
- 729102ff fix: incorrect jwk import order (#3344)
- f22046fc fix: isolate transactions for crdb
- f59f1c68 fix: scope type should be string instead of int (#3337)
- c417be1e test: fix flaky test
- 643e88c3 test: resolve time race
Artifacts can be verified with cosign using this public key.
Published by ory-bot almost 2 years ago
Resolves an issues with post-release steps and adds the introspect command to the Ory Hydra CLI.
Bug Fixes
- Add missing introspect command (c43aba3)
- Bump quickstart images to 2.0.0 (8c763ad)
- Post-release steps with yq (b6300e3)
Code Generation
- Pin v2.0.1 release commit (403223c)
Documentation
Changelog
- 8297cfc5 autogen(docs): regenerate and update changelog
- 403223cc autogen: pin v2.0.1 release commit
- c48e4811 docs: update README (#3323)
- c43aba3e fix: add missing introspect command
- 8c763ad8 fix: bump quickstart images to 2.0.0
- b6300e34 fix: post-release steps with yq
Artifacts can be verified with cosign using this public key.
Published by ory-bot almost 2 years ago
Ory Hydra 2.0 is available now! It ships major internal data restructuring and adds support for additional OAuth2 flows such as OAuth2 Token Exchange. Ory Hydra now natively integrates with Ory Kratos, an open source Identity Server.
Install the Ory CLI for the best developer experience to try out Ory Hydra 2.0 right away!
bash <(curl https://raw.githubusercontent.com/ory/meta/master/install.sh) -b . ory
sudo mv ./ory /usr/local/bin/
brew install ory/tap/cli
create a new project (you may also use Docker)
ory create project --name "Ory Hydra 2.0 Example"
project_id="{set to the id from output}"
and follow the quick & easy steps below.
Create an OAuth 2.0 Client, and run the OAuth 2.0 Client Credentials flow:
ory create oauth2-client --project $project_id \
--name "Client Credentials Demo" \
--grant-type client_credentials
client_id="{set to client id from output}"
client_secret="{set to client secret from output}"
ory perform client-credentials --client-id=$client_id --client-secret=$client_secret --project $project_id
access_token="{set to access token from output}"
ory introspect token $access_token --project $project_id
Try out the OAuth 2.0 Authorize Code grant right away!
By accepting permissions openid and offline_access at the consent screen, Ory refreshes and OpenID Connect ID token,
ory create oauth2-client --project $project_id \
--name "Authorize Code with OpenID Connect Demo" \
--grant-type authorization_code \
--response-type code \
--redirect-uri ttp://127.0.0.1:4446/callback
code_client_id="{set to client id from output}"
code_client_secret="{set to client secret from output}"
ory perform authorization-code \
--project $project_id \
--client-id $code_client_id \
--client-secret $code_client_secret
code_access_token="{set to access token from output}"
ory introspect token $code_access_token --project $project_id
What's changed in Ory Hydra 2.0?
- Ory Identities is now compatible with the Ory OAuth2 Login and Consent Flow. This means, for example, that Ory Kratos can be the login provider for Ory Hydra with a bit of configuration.
- The Ory Network enables this integration as a default.
- Ory Hydra 2.0 now natively supports key types such as ES256 for signing ID Tokens and OAuth 2.0 Access Tokens in JWT format.
- Additionally, the key naming mechanism was updated to conform with industry best practices.
- Ory Hydra 2.0 ships a complete refactoring of the internal database structure, reducing database storage at scale and optimizing query performance.
- All primary keys are now UUIDs to avoid hotspots in distributed systems. Please note that as part of this change it is no longer possible to choose the OAuth 2.0 Client ID. Instead, Ory chooses the best-performing ID format for the petabyte scale.
- Ory chose to denormalize tables that had a negative performance impact due to excessive JOIN statements.
- Using BCrypt as the primary hashing algorithm for OAuth 2.0 Client Secrets creates excessive CPU consumption at scale. OAuth 2.0 Client Secrets are auto-generated in Ory Hydra 2.x, removing the need for excessive hashing costs.
- The new PKBDF2 hasher can be fine-tuned to support hashing at scale without a significant threat model impact.
- This section only applies in scenarios where Ory Hydra is working in a do-it-yourself fashion e.g. on Docker. An Ory Hydra 2.0 compatible service is already available on the Ory Network.
- The database schema changed significantly from the previous structure. Please be aware that there might be a period where the database tables will be locked for writes while the upgrade runs. A full backup of the database before upgrading is essential! We recommend trying out the upgrade on a copy of a production database first.
Detailed Overview
Find a list of detailed changes below!
SQL Migrations
To run the SQL migrations using:
hydra migrate sql $DSN
SDK changes
Ory Hydra 1.x is a crucial service at Ory. Version 2.0 streamlines the APIs and SDKs to follow Ory API’s semantics and specification.
To better support TB-scale environments, the OAuth2 Client HTTP API's query
parameters for pagination have changed from limit and offset to page_token
and page_size. The page_token is an opaque string contained in the HTTP
Link Header, which expresses the next, previous, first, and last page.
Administrative endpoints now have an /admin prefix (e.g. POST /admin/keys instead of POST /keys). Existing administrative endpoints will redirect to this new prefixed path for backward compatibility.
HTTP endpoint /oauth2/flush, used to flush inactive access tokens was deprecated and has been removed. Please use hydra janitor instead.
To conform with the Ory V1 SDK, several SDK methods and payloads were renamed. Please check the CHANGELOG for a complete list of changes.
Configuration changes
The iss (issuer) value no longer appends a trailing slash but instead uses the raw value set in the config.
Setting
urls:
self:
issuer: https://auth.example.com
has changed
- "iss": "https://auth.example.com/"
+ "iss": "https://auth.example.com"
To set a trailing slash make sure to set it in the config value:
urls:
self:
issuer: https://auth.example.com/
CLI Changes
Flags --dangerous-allow-insecure-redirect-url and --dangerous-force-http have been removed. Use the --dev flag instead to denote a development environment with reduced security restrictions.
We now recommend using the Ory CLI to manage OAuth2 resources. As part of this restructuring, some of the commands were renamed. Here are some examples:
- hydra client create
+ ory create oauth2-client
- hydra clients list
+ ory list oauth2-clients
Additionally, array arguments now use the singular form:
hydra create client \
- --redirect-uris foo --redirect-uris bar \
+ --redirect-uri foo --redirect-uri bar \
- --grant-types foo --grant-types bar \
+ --grant-type foo --grant-type bar \
- --response-types foo --response-types bar \
+ --response-type foo --response-type bar \
- --allowed-cors-origins foo --allowed-cors-origins bar \
+ --allowed-cors-origin foo --allowed-cors-origin bar \
- --post-logout-callbacks foo --post-logout-callbacks bar \
+ --post-logout-callback foo --post-logout-callback bar
To manage resources in a do-it-yourself installation, continue using the hydra CLI.
Please check the CHANGELOG for a complete list of changes.
Ory Hydra 2.0 ships with support for OpenTelemetry. The previous telemetry solution using OpenTracing format is deprecated with this release.
Breaking Changes
SDK naming has changed for the following operations:
ory.
- V0alpha2Api.AdminDeleteOAuth2Token(context.Background()).
+ OAuth2Api.DeleteOAuth2Token(context.Background()).
ClientId("foobar").Execute()
ory.
- V0alpha2Api.RevokeOAuth2Token(
+ OAuth2Api.RevokeOAuth2Token(
context.WithValue(context.Background(), sdk.ContextBasicAuth, sdk.BasicAuth{
UserName: clientID,
Password: clientSecret,
})).Token(token).Execute()
ory.
- V0alpha2Api.AdminIntrospectOAuth2Token(context.Background()).
+ OAuth2Api.IntrospectOAuth2Token(context.Background()).
Token(token).
Scope("foo bar")).Execute()
SDK naming has changed for the following operations:
ory.
- V0alpha2Api.DiscoverJsonWebKeys(context.Background()).
+ WellknownApi.DiscoverJsonWebKeys(context.Background()).
Execute()
ory.
- V0alpha2Api.AdminGetJsonWebKeySet(context.Background(), setID).
+ JwkApi.GetJsonWebKeySet(context.Background(), setID).
Execute()
ory.
- V0alpha2Api.AdminGetJsonWebKey(context.Background(), setID, keyID).
+ JwkApi.GetJsonWebKey(context.Background(), setID, keyID).
Execute()
ory.
- V0alpha2Api.AdminCreateJsonWebKeySet(context.Background(), setID).
- AdminCreateJsonWebKeySetBody(hydra.AdminCreateJsonWebKeySetBody{
- Alg: "RS256",
- Use: "sig",
+ JwkApi.CreateJsonWebKeySet(context.Background(), setID).
+ CreateJsonWebKeySet(hydra.CreateJsonWebKeySet{
+ Alg: "RS256",
+ Use: "sig",
}).Execute()
ory.
- V0alpha2Api.AdminUpdateJsonWebKey(context.Background(), setID, keyID).
+ JwkApi.SetJsonWebKey(context.Background(), setID, keyID).
JsonWebKey(jsonWebKey).Execute()
ory.
- V0alpha2Api.AdminUpdateJsonWebKeySet(context.Background(), setID).
+ JwkApi.SetJsonWebKeySet(context.Background(), setID).
JsonWebKeySet(jsonWebKeySet).Execute()
ory.
- V0alpha2Api.AdminDeleteJsonWebKey(context.Background(), setID, keyID).
JwkApi.DeleteJsonWebKey(context.Background(), setID, keyID).
Execute()
ory.
- V0alpha2Api.AdminDeleteJsonWebKeySet(context.Background(), setID).
JwkApi.DeleteJsonWebKeySet(context.Background(), setID).
Execute()
SDK naming has changed for the following operations:
ory.
- V0alpha2Api.DiscoverJsonWebKeys(context.Background()).
+ WellknownApi.DiscoverJsonWebKeys(context.Background()).
Execute()
ory.
- V0alpha2Api.AdminGetJsonWebKeySet(context.Background(), setID).
+ JwkApi.GetJsonWebKeySet(context.Background(), setID).
Execute()
ory.
- V0alpha2Api.AdminGetJsonWebKey(context.Background(), setID, keyID).
+ JwkApi.GetJsonWebKey(context.Background(), setID, keyID).
Execute()
ory.
- V0alpha2Api.AdminCreateJsonWebKeySet(context.Background(), setID).
- AdminCreateJsonWebKeySetBody(hydra.AdminCreateJsonWebKeySetBody{
- Alg: "RS256",
- Use: "sig",
+ JwkApi.CreateJsonWebKeySet(context.Background(), setID).
+ CreateJsonWebKeySet(hydra.CreateJsonWebKeySet{
+ Alg: "RS256",
+ Use: "sig",
}).Execute()
ory.
- V0alpha2Api.AdminUpdateJsonWebKey(context.Background(), setID, keyID).
+ JwkApi.SetJsonWebKey(context.Background(), setID, keyID).
JsonWebKey(jsonWebKey).Execute()
ory.
- V0alpha2Api.AdminUpdateJsonWebKeySet(context.Background(), setID).
+ JwkApi.SetJsonWebKeySet(context.Background(), setID).
JsonWebKeySet(jsonWebKeySet).Execute()
ory.
- V0alpha2Api.AdminDeleteJsonWebKey(context.Background(), setID, keyID).
JwkApi.DeleteJsonWebKey(context.Background(), setID, keyID).
Execute()
ory.
- V0alpha2Api.AdminDeleteJsonWebKeySet(context.Background(), setID).
JwkApi.DeleteJsonWebKeySet(context.Background(), setID).
Execute()
SDK naming has changed for the following operations:
ory.
- V0alpha2Api.AdminRevokeOAuth2ConsentSessions(cmd.Context()).
+ OAuth2Api.RevokeOAuth2ConsentSessions(context.Background()).
Client(clientId).Execute()
ory.
- V0alpha2Api.AdminListOAuth2SubjectConsentSessions(cmd.Context(), id).
+ OAuth2Api.RevokeOAuth2ConsentSessions(context.Background()).
Client(clientId).Execute()
ory.
- V0alpha2Api.AdminListOAuth2SubjectConsentSessions(context.Background()).
+ OAuth2Api.ListOAuth2ConsentSessions(context.Background()).
Subject(subjectId).Execute()
ory.
- V0alpha2Api.AdminRevokeOAuth2LoginSessions(context.Background()).
+ OAuth2Api.RevokeOAuth2LoginSessions(context.Background()).
Subject(subjectId).Execute()
ory.
- V0alpha2Api.AdminGetOAuth2LoginRequest(context.Background()).
+ OAuth2Api.GetOAuth2LoginRequest(context.Background()).
LoginChallenge(challenge).Execute()
ory.
- V0alpha2Api.AdminAcceptOAuth2LoginRequest(context.Background()).
+ OAuth2Api.AcceptOAuth2LoginRequest(context.Background()).
AcceptOAuth2LoginRequest(body).
LoginChallenge(challenge).Execute()
ory.
- V0alpha2Api.AdminRejectOAuth2LoginRequest(context.Background()).
+ OAuth2Api.RejectOAuth2LoginRequest(context.Background()).
RejectOAuth2Request(body).
LoginChallenge(challenge).Execute()
ory.
- V0alpha2Api.AdminGetOAuth2ConsentRequest(context.Background()).
+ OAuth2Api.GetOAuth2ConsentRequest(context.Background()).
ConsentChallenge(challenge).Execute()
ory.
- V0alpha2Api.AdminAcceptOAuth2ConsentRequest(context.Background()).
+ OAuth2Api.AcceptOAuth2ConsentRequest(context.Background()).
AcceptOAuth2ConsentRequest(body).
ConsentChallenge(challenge).Execute()
ory.
- V0alpha2Api.AdminRejectOAuth2ConsentRequest(context.Background()).
+ OAuth2Api.RejectOAuth2ConsentRequest(context.Background()).
RejectOAuth2Request().
ConsentChallenge(challenge).Execute()
ory.
- V0alpha2Api.AdminAcceptOAuth2LogoutRequest(context.Background()).
+ OAuth2Api.AcceptOAuth2LogoutRequest(context.Background()).
LogoutChallenge(challenge).
Execute()
ory.
- V0alpha2Api.AdminRejectOAuth2LogoutRequest(context.Background()).
+ OAuth2Api.RejectOAuth2LogoutRequest(context.Background()).
LogoutChallenge(challenge).
Execute()
ory.
V0alpha2Api.AdminGetOAuth2LogoutRequest(context.Background()).
+ OAuth2Api.GetOAuth2LogoutRequest(context.Background()).
LogoutChallenge(challenge).
Execute()
- var AlreadyHandledError HandledOAuth2LoginRequest
+ var AlreadyHandledError ErrorOAuth2LoginRequestAlreadyHandled
- var AlreadyHandledError HandledOAuth2LoginRequest
+ var AlreadyHandledError ErrorOAuth2ConsentRequestAlreadyHandled
- var OAuth2SuccessResponse SuccessfulOAuth2RequestResponse
+ var OAuth2SuccessResponse OAuth2RedirectTo
Error models in the generated SDK have been renamed:
- oAuth2ApiError
+ errorOAuth2
The SDK API for the following has changed:
// Go example
ory.
- V0alpha2Api.AdminUpdateOAuth2Client(cmd.Context(), id)
+ Oauth2Api.SetOAuth2Client(cmd.Context(), id).
OAuth2Client(client).Execute()
ory.
- V0alpha2Api.AdminGetOAuth2Client(cmd.Context(), id).
+ Oauth2Api.GetOAuth2Client(cmd.Context(), id).
Execute()
ory.
- V0alpha2Api.AdminDeleteOAuth2Client(cmd.Context(), id).
+ Oauth2Api.DeleteOAuth2Client(cmd.Context(), id).
Execute()
ory.
- V0alpha2Api.AdminCreateOAuth2Client(cmd.Context()).
+ Oauth2Api.CreateOAuth2Client(cmd.Context()).
OAuth2Client(client).Execute()
ory.
- V0alpha2Api.DynamicClientRegistrationGetOAuth2Client(cmd.Context(), id).
+ OidcApi.GetOidcDynamicClient(cmd.Context(), id).
Execute()
ory.
- V0alpha2Api.DynamicClientRegistrationGetOAuth2Client(cmd.Context()).
+ OidcApi.CreateOidcDynamicClient(cmd.Context()).
OAuth2Client(client).Execute()
ory.
- V0alpha2Api.DynamicClientRegistrationDeleteOAuth2Client(cmd.Context()).
+ OidcApi.DeleteOidcDynamicClient(cmd.Context()).
OAuth2Client(client).Execute()
ory.
- V0alpha2Api.DynamicClientRegistrationUpdateOAuth2Client(cmd.Context(), id).
+ OidcApi.SetOidcDynamicClient(cmd.Context(), id).
Execute()
We removed compatibility with unsupported database versions (e.g. MySQL 5.6). Ory Hydra v2.x is now compatible with MySQL 8.0.13+, PostgreSQL 11.8+, CockroachDB v22.1.2+.
Configuration keys have changed:
serve: {
public: {
- access_log: {
+ request_log: {
disable_for_health: true
},
},
admin: {
- access_log: {
+ request_log: {
disable_for_health: true
},
}
}
Rename SDK method from deleteOAuth2Token to adminDeleteOAuth2Token.
Rename SDK method from oauth2Token to performOAuth2TokenFlow.
Rename SDK method from introspectOAuth2Token to adminIntrospectOAuth2Token.
Rename SDK method from userinfo to getOidcUserInfo.
Rename SDK method from discoverOpenIDConfiguration to discoverOidcConfiguration.
Rename SDK method from listTrustedJwtGrantIssuers to adminListTrustedOAuth2JwtGrantIssuers.
Rename SDK method from deleteTrustedJwtGrantIssuer to adminDeleteTrustedOAuth2JwtGrantIssuer.
Rename SDK method from getTrustedJwtGrantIssuer to adminGetTrustedOAuth2JwtGrantIssuer.
Rename SDK method from trustJwtGrantIssuer to adminTrustOAuth2JwtGrantIssuer.
Rename SDK method from rejectLogoutRequest to adminRejectOAuth2LogoutRequest.
Rename SDK method from rejectConsentRequest to rejectOAuth2ConsentRequest.
Rename SDK method from acceptConsentRequest to adminAcceptOAuth2ConsentRequest.
Rename SDK method from getOAuth2ConsentRequest to adminGetOAuth2ConsentRequest.
Rename SDK method from rejectLoginRequest to rejectOAuth2LoginRequest.
Rename SDK method from acceptLoginRequest to adminAcceptOAuth2LoginRequest.
Rename SDK method from getLoginRequest to adminGetOAuth2LoginRequest.
Rename SDK method from revokeAuthenticationSession to adminRevokeOAuth2LoginSessions.
Rename SDK method from adminListSubjectConsentSessions to adminListOAuth2SubjectConsentSessions.
Rename SDK method from revokeConsentSessions to adminRevokeOAuth2ConsentSessions
This release updates SDK services from public and admin to v2. Methods exposed at the admin interface are now prefixed with admin (e.g. adminCreateJsonWebKeySet). Administrative endpoints now have an /admin prefix (e.g. POST /admin/keys). Existing administrative endpoints will redirect to this new prefixed path for backwards compatibility.
This release updates SDK services from public and admin to v2. Methods exposed at the admin interface are now prefixed with admin (e.g. adminCreateOAuth2Client). Administrative endpoints now have an /admin prefix (e.g. POST /admin/clients). Existing administrative endpoints will redirect to this new prefixed path for backwards compatibility.
The default names of cookies have changed:
- oauth2_authentication_csrf
+ ory_hydra_login_csrf
- oauth2_consent_csrf
+ ory_hydra_consent_csrf
- oauth2_authentication_session
+ ory_hydra_session
Use the new configuration option to change the cookie names back to v1.x if required.
CLI flag --dangerous-force-http has been removed. Please use the --dev flag instead!
CLI flag --dangerous-allow-insecure-redirect-url has been removed. Please use the --dev flag instead!
The hydra token revoke command has been renamed to hydra revoke token and now supports structured output (JSON, tables, ...).
The hydra token introspect command has been renamed to hydra introspect token and now supports structured output (JSON, tables, ...).
The hydra token delete command has been renamed to hydra delete access-tokens and now supports structured output (JSON, tables, ...).
The hydra token client command has been renamed to hydra perform client-credentials and now supports structured output (JSON, tables, ...).
The hydra keys create|delete|get|import commands have changed to follow other Ory project's guidelines, including structured output and improved handling. They are now:
hydra create jwks
hydra get jwks
hydra delete jwks
hydra import jwk
Please head over to the documentation for more information or use the --help CLI flag for each command.
HTTP endpoint /oauth2/flush, used to flush inactive access token was deprecated and has been removed. Please use hydra janitor instead.
Command hydra clients import is now hydra import client.
Command hydra clients update is now hydra update client. Additionally, all flags are now singular:
hydra update client [client-id] \
- --redirect-uris foo --redirect-uris bar \
+ --redirect-uri foo --redirect-uri bar \
- --grant-types foo --grant-types bar \
+ --grant-type foo --grant-type bar \
- --response-types foo --response-types bar \
+ --response-type foo --response-type bar \
- --allowed-cors-origins foo --allowed-cors-origins bar \
+ --allowed-cors-origin foo --allowed-cors-origin bar \
- --post-logout-callbacks foo --post-logout-callbacks bar \
+ --post-logout-callback foo --post-logout-callback bar
To better support TB-scale environments, the OAuth2 Client HTTP API's query parameters for pagination have changed from limit and offset to page_token and page_size. The page_token is an opaque string contained in the HTTP Link Header, which expresses the next, previous, first, and last page.
Command hydra clients list is now hydra list client. Please notice that the pagination flags have changed to --page-token and page-size!
Command hydra clients delete is now hydra delete client.
Command hydra clients get is now hydra get client.
Command hydra clients create is now hydra create client. Additionally, all flags are now singular:
hydra create client \
- --redirect-uris foo --redirect-uris bar \
+ --redirect-uri foo --redirect-uri bar \
- --grant-types foo --grant-types bar \
+ --grant-type foo --grant-type bar \
- --response-types foo --response-types bar \
+ --response-type foo --response-type bar \
- --allowed-cors-origins foo --allowed-cors-origins bar \
+ --allowed-cors-origin foo --allowed-cors-origin bar \
- --post-logout-callbacks foo --post-logout-callbacks bar \
+ --post-logout-callback foo --post-logout-callback bar
This change is backwards compatible, but changes the default hashing algorithm to PBKDF2. To keep using BCrypt for hashing new OAuth2 Client Secrets set the following configuration option in your configuration file:
oauth2:
hashers:
algorithm: bcrypt
To improve security and scalability (in particular sharding), OAuth 2.0 Client IDs can no longer be chosen but are always assigned a random generated UUID V4. OAuth 2.0 Clients created with custom IDs before the v2.0 release will continue working with their legacy Client ID in Ory Hydra v2.x.
Additionally, the hydra create client command no longer supports flag --id and flag --callbacks has been renamed to --redirect-uris.
The iss (issuer) value no longer appends a trailing slash but instead uses the raw value set in the config.
Setting
urls:
self:
issuer: https://auth.example.com
has changed
- "iss": "https://auth.example.com/"
+ "iss": "https://auth.example.com"
To set a trailing slash make sure to set it in the config value:
urls:
self:
issuer: https://auth.example.com/
SDK object PatchDocument was renamed to JsonPatchDocument.
TLS is no longer enabled by default. We want to make deployments behind TLS termination easier. To expose Ory Hydra directly to the public internet, configure keys serve.<public|admin>.tls.
JSON Web Keys are no longer prefixed with public or private. This affects keys generated in Ory Hydra after upgrading to this patch. Existing keys are unaffected by this.
OAuth2 errors can no longer be returned in the legacy error format. Essentially, fields error_hint, error_debug have been removed. Option oauth2.include_legacy_error_fields has been removed.
The HS512 and HS256 JSON Web Key generators has been removed. It is now only possible to generate asymmetric keys in Ory Hydra. It will still be possible to save HS512 or HS256 keys.
if using MySQL, hydra_jwk/kid and hydra_oauth2_trusted_jwt_bearer_issuer/key_id may only contain ascii/utf-8 symbols 0-127
Encode MySQL columns hydra_oauth2_trusted_jwt_bearer_issuer/key_id and hydra_jwk/kid in ascii as
a workaround for the 3072-byte index entry size limit1.
Signed-off-by: Grant Zvolsky [email protected]
This patch merges four SQL Tables into a new table, deleting the old tables in the process. The migrations in this patch are expected to be applied offline. Please be aware that there are no down migrations, and if something goes wrong, data loss is possible. Always back up your database before applying migrations. For more information, see Hydra 2.x Migration Guide.
Rows with NULL login_challenge in hydra_oauth2_consent_request and corresponding hydra_oauth2_consent_request_handled are deleted as a side effect of the merge migration. This is done with the assumption that only a very small number of sessions, issued by pre-1.0 Hydra, will be affected. Please contact us if this assumption doesn't apply or if the deletion adversely affects your deployment.
Signed-off-by: Grant Zvolsky [email protected]
Bug Fixes
-
Add CORS to public health handler (#3114) (02c6d5d):
Co-authored-by: Reaper [email protected]
Co-authored-by: Patrik [email protected]
Co-authored-by: Alano Terblanche [email protected]
Co-authored-by: Reaper [email protected] -
Add json1 tag everywhere (dd1d733)
-
Add missing down migrations (a98c067)
-
Allow retries of unused login & consent requests (51a586b), closes #2914 #3085 #2824
-
Cache migration status (7e25fdb)
-
cli: Output format issues (fe3c899)
-
Cockroach migration fixes (7bed244)
-
Compile errors (d1f5a0e)
-
Compile issue (83983c2)
-
Compile issues (68cb7d5)
-
Conditionals in db-diff (a006b04)
-
config: Add default to supported types. (f4812c8)
-
config: Correct salt detection (2b6350c)
-
config: Disallow additional properties (9022769)
-
config: Support number (ab6a9ee)
-
ConfirmLoginSession, missing FKs; add tests (1f7bf40)
-
Conformity health check (e163c80)
-
Consistently use RS256 in hot reloading (6376135)
-
Default back to RS256 keys (891fb55)
-
Disable NID tests with HSM enabled (142cd13):
We currently don't support NID isolation in combination with HSM.
-
Docker image build (1d8a8ff)
-
Docker instructions (063f61b)
-
Dont close crdb for reuse purposes (11587ae)
-
Fix hydra_client pk change mysql down migration (#2791) (560acce)
-
Fix unbatched select in flushInactiveTokens (a5cc6ea):
chore: code review
chore: format
don't delete more tokens than expected.
correct test.
add nid in flush tokens.
-
Handle server error when refresh token requests come same time (#3207) (b0196c0)
-
Hsm compile issues (8571a67)
-
HSM test (ca748a1)
-
hsm: Public key extraction (57cf46c)
-
hsm: Public key extraction everywhere (c9c2e01)
-
Ignore cypress screenshots in git (668a319)
-
Improve duration pattern (6c8dda8)
-
Improve health check reporting (1bd0c52)
-
Improve jwk generator defaults (ece5ca6)
-
Improve lazy initialization of JWKs (8cffc5b)
-
Improve migration status speed (1a4abd6)
-
Improve time validation (b32ff33)
-
Incorrect queries (255b4e2)
-
jwk: Expose correct metadata algorithms (0a786b7)
-
Lazy load PKI (d65aa3a)
-
Lint issues (72a5cd8)
-
Make servicelocator explicit (3a26385)
-
Move to v0alpha2 api spec (a364db4)
-
Mysql slice delete (c56b958):
- Add a workaround for mysql slice delete
- Optimize logout verification (save 1 db rountrip)
- Update a test to use StaticContextualizer & revert CleanAndMigrate workaround
- Ensure a Client generated with faker satisfies the DB schema
- Remove unused argument from HandleConsentRequest
-
mysql: Fix mysql key too long error (ba16958)
-
oauth2: Incorrect TTL override (7893a98)
-
Optimise sql update to avoid redundant writes (#3289) (1aa6cc4), closes #3137:
The SQL update here would potentially update a lot of rows, which did not need updating. In some DB engines, this would not be an issue, because the redundant writes are ignored. But on PostgreSQL engines, it is another story; here it would actually carry out the writes, leading to a potentially high number of redundant iops when the engine is vaccuming outdated records. With this change, the SQL update will only affect the rows which is not in the desired state already.
-
Pop compile issue (3e7b6b4)
-
Prefix paths correctly with /admin (e130dfa)
-
Regression in database layer (1d78e79)
-
Remove deprecated config value (8994190)
-
Remove goswagger generated client (e2c8809)
-
Remove incorrect aliases (2a20080)
-
Remove obsolete type patches (e670d68)
-
Remove unnecessary load of TLS certificates at boot (13691d3)
-
Remove unused swagger struct (4ff0690)
-
Replace of consent session expires values (e1731ba)
-
Resolve a merge conflict in migration_test (#2811) (acb16c1)
-
Resolve conformance build issues (f6ee1d3)
-
Resolve internal SDK regressions (937e6ba)
-
Resolve merge conflicts (6eee09c)
-
Resolve migration regressions (5552e4d)
-
Resolve test issues and regressions introduced by the new JWK generator (77b1ac7)
-
Resolve token prefix regression (1fd6ea3)
-
Retry transient crdb transaction failures (f0f3139)
-
Revert to normal crdb (c9a248d)
-
sdk: GenericError type (21c579a)
-
sdk: Make session uniquely named (468e27d)
-
sdk: Omit DefaultSession (954aa5f)
-
sdk: Remove pattern from scope parameter (1332fe6), closes #3142
-
sdk: Resolve type issues and regenerate SDK (6880fea)
-
sdk: Use correct struct for response (04b308f)
-
Speed up health checks (eafa2bb)
-
Support issuer with and without trailing slash (d746fa4), closes #1482
-
Update benchmark script (63a84de)
-
Use --yes flag in db-diff (36ddb61)
-
Use config func everywhere (d1af32d)
-
Use correct context (3ceefd7)
-
Use CreateWith (9fbbbdf)
-
Use StringSliceJSONFormat instead of StringSlicePipeDelimiter (#3112) (1d9891d):
Code Generation
- Pin v2.0.0 release commit (4d83a28)
Code Refactoring
-
hydra keyscommand (e466d7c) -
hydra token clientcommand (81e79f2) -
hydra token deletecommand (aa338e1) -
hydra token introspectcommand (da3e2b4) -
hydra token revokecommand (42e75c3) -
CLI environment variables
HYDRA_URLhas been renamed toORY_SDK_URL(08bbbab):BREKAING CHANGE: To follow ecosystem convention, environment variables
HYDRA_URL,HYDRA_ADMIN_URLhave been renamed toORY_SDK_URL. -
client: Make OAuth2 Client IDs system-chosen and immutable (4002224), closes #2911
-
client: Rename SDK methods and introduce
/adminprefix (0752721) -
client: Replace limit and offset parameters with page_token and page_size (23585b5)
-
consent: Rename SDK method from
acceptConsentRequesttoadminAcceptOAuth2ConsentRequest(5885ab3) -
consent: Rename SDK method from
acceptLoginRequesttoadminAcceptOAuth2LoginRequest(fa27d0c) -
consent: Rename SDK method from
adminListSubjectConsentSessionstoadminListOAuth2SubjectConsentSessions(bb51ba0) -
consent: Rename SDK method from
getLoginRequesttoadminGetOAuth2LoginRequest(9053040) -
consent: Rename SDK method from
getOAuth2ConsentRequesttoadminGetOAuth2ConsentRequest(475efbc) -
consent: Rename SDK method from
rejectConsentRequesttorejectOAuth2ConsentRequest(e0e3da9) -
consent: Rename SDK method from
rejectLoginRequesttorejectOAuth2LoginRequest(37a8839) -
consent: Rename SDK method from
rejectLogoutRequesttoadminRejectOAuth2LogoutRequest(cdffa1e) -
consent: Rename SDK method from
revokeAuthenticationSessiontoadminRevokeOAuth2LoginSessions(0a5ebe8) -
consent: Rename SDK method from
revokeConsentSessionstoadminRevokeOAuth2ConsentSessions(1108409) -
Deprecate
--dangerous-allow-insecure-redirect-urlflag (46b5887) -
Deprecate
--dangerous-force-httpflag (062734e) -
Drop TLS by default (edb042e)
-
Environment variable
DATABASE_URLhas been deprecated (8023d2a) -
Finalize consent SDK methods (53d225a)
-
Generated UUID variant & version test (#2793) (697813e), closes #2792
-
Improve performance and reduce data use of consent persistence layer (#2836) (53862f2):
This patch changes the internal data structure and reduces four (sort of redundant) tables into one. As part of this change, a few new tools have been added:
-
Introduce the
hydra sql gencommand and a convenience Make target with autocompletion. The command reads migration templates from a source directory and produces migration files in a target directory. Its main function is to split a single source file into multiple files using split marks. -
Introduce the
hack/db-diff.shcommand to generate database schema diffs at different commits. This script is used to view and review the impact of migrations on the database schema.
-
-
jwk: No longer prefix keys with
publicorprivate(5e2ea0b) -
jwk: Rename SDK methods and introduce
/adminprefix (cd007bb) -
Make commands easier to consume (cc9d9e5)
-
oauth2: Clean up changes (c12b45c)
-
oauth2: Rename SDK method from
deleteOAuth2TokentoadminDeleteOAuth2Token(ea4caf7) -
oauth2: Rename SDK method from
discoverOpenIDConfigurationtodiscoverOidcConfiguration(df467a0) -
oauth2: Rename SDK method from
introspectOAuth2TokentoadminIntrospectOAuth2Token(f2bd9a3) -
oauth2: Rename SDK method from
oauth2TokentoperformOAuth2TokenFlow(51b58e7) -
oauth2: Rename SDK method from
userinfotogetOidcUserInfo(4e554e7) -
Remove
/oauth2/flushendpoint (17c226c) -
Remove
oauth2.include_legacy_error_fieldsconfig (148cadb) -
Remove HS512 and HS256 jwk key generator (5fb3049)
-
Rename
access_logtorequest_log(223c8bc) -
Rename
hydra clients createcommand (76eb93c):Renames the command to
hydra create clientand changes CLI flags. -
Rename
hydra clients deletecommand (dea2fdd):Renames the command to
hydra delete clientand changes CLI flags. -
Rename
hydra clients getcommand (edd4b43):Renames the command to
hydra get clientand changes CLI flags. -
Rename
hydra clients importcommand (7de7841):The
hydra clients importcommand now supports reading from STDIN as well as the file system, and ships with output formats such asjsonandjson-pretty. -
Rename
hydra clients listcommand (1c0f971):Renames the command to
hydra list clientand changes CLI flags. -
Rename
hydra clients updatecommand (7482b77) -
Replace custom key generator with jose key generator (d2d5512):
-
sdk: Consent SDK (e800002)
-
sdk: JSON Web Key SDK API (06d565e)
-
sdk: OAuth 2.0 Trust Relationship SDK (b0a2b05)
-
sdk: OAuth2 SDK API (142b55f)
-
sdk: Rename errors (6b60156)
-
sdk: Rename oauth2 client operations and payloads (cb742ad)
-
sdk: Rename PatchDocument to JsonPatchDocument (a54ea69)
-
trust: Rename SDK method from
deleteTrustedJwtGrantIssuertoadminDeleteTrustedOAuth2JwtGrantIssuer(e0be7cf) -
trust: Rename SDK method from
getTrustedJwtGrantIssuertoadminGetTrustedOAuth2JwtGrantIssuer(210116e) -
trust: Rename SDK method from
listTrustedJwtGrantIssuerstoadminListTrustedOAuth2JwtGrantIssuers(cb7b9e0) -
trust: Rename SDK method from
trustJwtGrantIssuertoadminTrustOAuth2JwtGrantIssuer(7edf8df)
Documentation
- Add required key to all versions in the version schema (#3233) (ac61740)
- Clarify command usage strings (34cde51)
- Remove mention of CircleCI (#3240) (75f7b50)
- Update config key descriptions (919170f)
Features
-
Add
db.ignore_unknown_table_columnsconfiguration property (#3192) (#3193) (5842946):The property allows to ignore scan errors when columns in the SQL result have no fields in the destination struct.
-
Add ability to allow token refresh from hook without overriding the session claims (#3146) (afa2ea0), closes #3082
-
Add new key
serve.public.tls.enabled(ecacc6d) -
Add SQLite dependency to SQLite Dockerfile (#3282) (841a153)
-
Add tag descriptions (c111a4c)
-
Add token prefixes (60bab08), closes #2845:
This patch adds token prefixes to access tokens (
ory_at_), refresh tokens (ory_rt_), and authorize codes (ory_ac_). Token prefixes are useful when scanning for secrets in e.g. git repositories. Token prefixes are only issued for non-JWTs. -
Allow config context (d894c97)
-
Better control for cookie secure flag (90d539f)
-
client: Respect ip restrictions in client validation (cafe89a)
-
cli: Improve migrate command handling (e252654)
-
cli: Significantly improved
create client(bb9c8ba), closes #3091:This patch adds output formats to
hydra create clientand makes all client fields configurable as flags. -
Config hot reloading architecture (bbe0406)
-
Custom client token ttl (#3206) (9ef671f), closes #3157:
This change introduces a new endpoint that allows you to control how long client tokens last. Now you can configure the lifespan for each valid combination of Client, GrantType, and TokenType.
-
Deprecate autoincrement primary key in hydra_client (#2784) (6d01e2e), closes #2781
-
Deprecate autoincrement primary key in hydra_jwk (#2789) (b76a151), closes #2788
-
Implement NID (b7fc2bf)
-
Improve CLI messages (e934c4f)
-
Improve cloud cli compatibility (93a626d)
-
Improve cookie settings (9717cad)
-
Improve refresh token error messages (2769c9b)
-
Improved cookie controls (e7834ec):
New cookie configuration options have been introduced, allowing a higher degree of control:
serve: cookies: same_site_mode: Lax same_site_legacy_workaround: false domain: example.com names: login_csrf: ory_hydra_login_csrf consent_csrf: ory_hydra_consent_csrf session: ory_hydra_session -
Make all ui urls relative (370a487)
-
Make CORS config hot reloadable (2d5c893)
-
Make perform commands ory cloud-able (954693f)
-
Pass options from root (2f91ef4)
-
Rebuild containers on start (5b616d8)
-
Replace hydra's transaction impl with ory/popx/transaction (77d8dac)
-
Respect local DNS restrictions (7eb1d1c)
-
sdk: Add missing bearer security definition (a85bc7a)
-
sdk: Type nulls (fe70395)
-
Support alternate hashing algorithms for client secrets (ddba42f), closes rfc6819#section-5 /datatracker.ietf.org/doc/html/rfc6819#section-5:
This patch adds support for hashing client secrets using pbkdf2 instead of bcrypt, which might be a more appropriate algorithm in certain settings. As we assume that most environments fall in this category, we also changed the default to pbkdf2 with 25.000 rounds (roughly 1-3ms per hash on an Apple M1 Max core).
High hash costs are needed when hashing user-chosen passwords, as users often reuse passwords across sites. A high hash cost will make it much harder for the attacker to guess the user-chosen password and try using it on other sites (e.g. Google).
As most client secrets are auto-generated, using high hash costs is not useful. The password (OAuth2 Client Secret) is not user chosen and unlikely to be reused. As such, there is little point in using excessive hash costs to protect users. High hash costs in a system like Ory Hydra will cause high CPU costs from mostly automated traffic (OAuth2 Client interactions). It has also been a point of critizism from some who wish for better RPS on specific endpoints.
Other systems like Keycloak do not hash client secrets at all, referencing more secure authentication mechanisms such as assertion-based client authentication.
-
Support ES256 for generating JWTs (9a080ad)
-
Tls on public port can now be configured without restrictions (73d9517)
-
Upgrade go-swagger (cce8d60)
Tests
- Add test for access token strategy (b4865dd)
- conformance: Add directory (f5d0885)
- conformity: Revert admin prefix (580f33b)
- conformity: Sdk regression (15f3cfc)
- e2e: Add trailing slash to issuer (fa23960)
- e2e: Fix build instructions (415658d)
- e2e: Fix issuer URL (03b2340)
- e2e: Fix jwt regression (647822d)
- e2e: Resolve test regressions (30855d9)
- e2e: Respect metadata (7bea2e8)
- e2e: Upgrade cypress (40be7bb)
- e2e: Upgrade jwks-rsa (8ddf880)
- Fix a flaky test (51600f4)
- Fix assertions on nil pointers (8710590)
- Fix conformity issues (2875c19)
- Fix failing master pipeline (#3283) (f979adb)
- Fix flaky equal check (1100aba)
- Fix flaky equal check (2c4615c)
- Fix resp.bodyclose lint error (f0f5223)
- hsm: Do not evaluate HSM private key (3420026)
- hsm: Resolve test issues (8db9e5b)
- Implement network test structure for clients (8a09175)
- Improve jwk test layout (3b7a1a7)
- migratest: Add missing cockroach migrations and debug test failures (5e6c099)
- Refactor migration tests to use fixtures (#2936) (7b96651), closes #2901
- Remove unused fixture (1cf5bd0)
- Resolve test migration issues (63b7303)
- Test client update and double delete (3a50926)
- Update fixtures (e77c0d3)
- Update paths to reflect new admin api (549deda)
- Update resource limits (9e9ea94)
- Update snapshot (1c9a0d2)
- Update snapshots (5f5c81e)
- Update snapshots (01dbc0e)
- Update snapshots (34bc743)
- Update snapshots (c66a536)
- Use fixed time.Now function in pop (08968aa)
Unclassified
- unstaged - refactor sdk use across the board (34dfc0f)
- code review: add missing nid (2592451)
- code review (8e961d0)
- code review: contextualize config (10c146b)
- code review: make sure CreateClient doesn't use provided ID (8eec85d)
- code review: generate first NID randomly; add/update tests; fix db-diff (00490cb)
- Create networks table (a2c5e14)
Changelog
- 52154bc1 autogen(docs): generate and bump docs
- 9d01e248 autogen(docs): generate cli docs
- 3895d8a4 autogen(docs): regenerate and update changelog
- c16ffb46 autogen(docs): regenerate and update changelog
- 984185fb autogen(docs): regenerate and update changelog
- 181dda57 autogen(docs): regenerate and update changelog
- e70a6ce0 autogen(docs): regenerate and update changelog
- 07e02124 autogen(docs): regenerate and update changelog
- 1cab9408 autogen(docs): regenerate and update changelog
- 200dc9a4 autogen(docs): regenerate and update changelog
- 60b93459 autogen(docs): regenerate and update changelog
- 09b9318f autogen(docs): regenerate and update changelog
- e4d17df7 autogen(openapi): Regenerate swagger spec and internal client
- 20f2bcda autogen(openapi): Regenerate swagger spec and internal client (#2812)
- 8b12c914 autogen(openapi): regenerate swagger spec and internal client
- f9e71cfe autogen(openapi): regenerate swagger spec and internal client
- f148145a autogen(openapi): regenerate swagger spec and internal client
- 8db8cd7a autogen: pin v2.0.0 release commit
- 4d83a289 autogen: pin v2.0.0 release commit
- c68e1303 autogen: pin v2.0.0-alpha.0.pre.0 release commit
- 71226bc9 autogen: pin v2.0.0-alpha.0.pre.1 release commit
- 0cafe8fb autogen: pin v2.0.0-alpha.0.pre.2 release commit
- e27e2901 chore(deps): bump minimist and minimist in /test/e2e/oauth2-client (#3246)
- 8e351373 chore(sdk): remove obsolete template
- c38e700f chore: add json1 tag to db-diff
- 22d4a924 chore: address merge conflicts
- 3ba28f2b chore: backport migration fix to migration source (#3267)
- f4676194 chore: bump go to 1.19
- ac279c38 chore: change metric name and make Go 1.19 compatible (#3223)
- dc119136 chore: code review
- 96adcb84 chore: delete unused code
- 9fd2a473 chore: fix CLI command description (#3248)
- 81503e03 chore: fix compile and lint issues
- 922b43aa chore: fix formatting (#3269)
- 3632a6cf chore: fix lint issues
- 046b1ebe chore: fix typo (#3236)
- da0feb75 chore: format
- 56d1286b chore: format
- 6e593025 chore: format
- 2ef71d97 chore: format
- 655f8aa5 chore: format
- a76cda3e chore: format
- 15cdb885 chore: format using Make (#3257)
- b849d3d8 chore: go mod tidy
- 2adb928c chore: regenerate SDKs
- f5d89636 chore: regenerate SDKs
- 336ccaf8 chore: regenerate values
- 019f6bf3 chore: remove cypress screenshots
- 0b643a36 chore: remove double tabs from Makefile (#3273)
- abca5edb chore: remove fosite replace
- cc5d7701 chore: remove mod rewrites
- bbd48047 chore: remove stray console.log's
- 925013e3 chore: remove unused OpenAPI specifications and update snapshots
- 47daf0a1 chore: remove unused code
- 098a9831 chore: reorganize definition
- a28bcf1f chore: styles
- 49d48477 chore: update Prettier and ory-prettier-style and format everything (#3242)
- 82ba4467 chore: update formatter and formatting
- 5835ede1 chore: update fosite dependency
- aa7d0592 chore: update go mod
- b067680c chore: update golang and alpine
- f1b0603a chore: update openapi-generator to 6.0.1
- 8cea91d4 chore: update ory/x
- 686d59cb chore: update package locks
- e07e578b chore: update prettierignore
- 216352e3 chore: update repository templates
- a9c8da01 chore: update repository templates to https://github.com/ory/meta/commit/19eed817e5d5b64509887ef5f1e3eff3e3ce03a1
- 8b8e73d5 chore: update repository templates to https://github.com/ory/meta/commit/23d918a32533554c30d720dc44e821de3cda18f8
- 1c9f3e0c chore: update repository templates to https://github.com/ory/meta/commit/4a68ca0e3b70305c4a49a65777cb7f83a5eb9d89
- a73301c1 chore: update repository templates to https://github.com/ory/meta/commit/4ef13422e91f15b9f70014a0d67b92498ab728d1
- 8177cb5e chore: update repository templates to https://github.com/ory/meta/commit/6ab5ce6da0cc57d4492e932602bbfd4a76547795
- be24b804 chore: update repository templates to https://github.com/ory/meta/commit/935cc0443464fd76fbf41dff1081b368080c9353
- 791f5d12 chore: upgrade crdb to v22.x
- c8c3dbce chore: upgrade golangci-lint
- 55948d86 ci: add missing npm dependencies for changelog generation
- b4931a3c ci: do not use --verbose flag
- f040caf0 ci: install changelog-generator-cli
- 1cb56dfe ci: update crdb
- 8e961d0e code review
- 2592451b code review: add missing nid
- 10c146b4 code review: contextualize config
- 00490cbb code review: generate first NID randomly; add/update tests; fix db-diff
- 8eec85d3 code review: make sure CreateClient doesn't use provided ID
- ac617401 docs: add required key to all versions in the version schema (#3233)
- 34cde517 docs: clarify command usage strings
- 75f7b500 docs: remove mention of CircleCI (#3240)
- 919170ff docs: update config key descriptions
- e2526547 feat(cli): improve migrate command handling
- bb9c8ba4 feat(cli): significantly improved
create client - cafe89ad feat(client): respect ip restrictions in client validation
- a85bc7ab feat(sdk): add missing bearer security definition
- fe70395a feat(sdk): type nulls
- 2ee92293 feat(tracing): add lots of tracing spans (#3125)
- 841a1535 feat: add SQLite dependency to SQLite Dockerfile (#3282)
- 5842946d feat: add
db.ignore_unknown_table_columnsconfiguration property (#3192) (#3193) - afa2ea03 feat: add ability to allow token refresh from hook without overriding the session claims (#3146)
- ee9032ce feat: add embedx helpers (#3189)
- ecacc6de feat: add new key
serve.public.tls.enabled - a84c5f50 feat: add nid tests and resolve issues (#3102)
- c111a4ce feat: add tag descriptions
- 60bab083 feat: add token prefixes
- d894c974 feat: allow config context
- 90d539f5 feat: better control for cookie secure flag
- bbe0406d feat: config hot reloading architecture
- 9ef671f2 feat: custom client token ttl (#3206)
- 6d01e2e7 feat: deprecate autoincrement primary key in hydra_client (#2784)
- b76a1514 feat: deprecate autoincrement primary key in hydra_jwk (#2789)
- 1d13be6d feat: hot-reload TLS certificate (#3265)
- b7fc2bff feat: implement NID
- e934c4f7 feat: improve CLI messages
- 93a626d1 feat: improve cloud cli compatibility
- 9717cad6 feat: improve cookie settings
- 2769c9b3 feat: improve refresh token error messages
- e7834ecb feat: improved cookie controls
- 2d5c8930 feat: make CORS config hot reloadable
- 370a4874 feat: make all ui urls relative
- 954693fe feat: make perform commands ory cloud-able
- 2f91ef47 feat: pass options from root
- 5b616d8a feat: rebuild containers on start
- fbcaaade feat: renaming to Ory Network (#3298)
- 77d8dacb feat: replace hydra's transaction impl with ory/popx/transaction
- 7eb1d1c0 feat: respect local DNS restrictions
- 9a080ad2 feat: support ES256 for generating JWTs
- ddba42f4 feat: support alternate hashing algorithms for client secrets
- 05eaf6d3 feat: switch to otelx (#3108)
- 47d0518e feat: switch to otelx (#3108)
- 73d95175 feat: tls on public port can now be configured without restrictions
- cce8d609 feat: upgrade go-swagger
- a2c5e142 feature: create networks table
- fe3c8990 fix(cli): output format issues
- f4812c85 fix(config): add default to supported types.
- 2b6350c0 fix(config): correct salt detection
- 90227699 fix(config): disallow additional properties
- ab6a9ee2 fix(config): support number
- 57cf46c4 fix(hsm): public key extraction
- c9c2e016 fix(hsm): public key extraction everywhere
- 0a786b7c fix(jwk): expose correct metadata algorithms
- ba16958c fix(mysql): fix mysql key too long error
- 7893a980 fix(oauth2): incorrect TTL override
- 21c579ad fix(sdk): genericError type
- 1ab345b9 fix(sdk): handle all error codes (#3153)
- 468e27d0 fix(sdk): make session uniquely named
- 954aa5f3 fix(sdk): omit DefaultSession
- 1332fe6c fix(sdk): remove pattern from scope parameter
- 6880feaf fix(sdk): resolve type issues and regenerate SDK
- 04b308f3 fix(sdk): use correct struct for response
- 1f7bf40e fix: ConfirmLoginSession, missing FKs; add tests
- ca748a1d fix: HSM test
- cd2c252b fix:
allowed_top_level_claimsset to nil (#3245) - 2597f190 fix:
max_age=0forces authentication - 02c6d5d4 fix: add CORS to public health handler (#3114)
- dd1d733b fix: add json1 tag everywhere
- a98c0671 fix: add missing down migrations
- 51a586b0 fix: allow retries of unused login & consent requests
- 7e25fdbd fix: cache migration status
- 9a4f9e99 fix: client specific CORS
- 7bed2445 fix: cockroach migration fixes
- d1f5a0ef fix: compile errors
- 83983c2b fix: compile issue
- 68cb7d51 fix: compile issues
- a006b048 fix: conditionals in db-diff
- e163c803 fix: conformity health check
- 63761357 fix: consistently use RS256 in hot reloading
- 891fb551 fix: default back to RS256 keys
- 142cd133 fix: disable NID tests with HSM enabled
- 1d8a8fff fix: docker image build
- 05bda6bf fix: docker image build (#3247)
- 063f61be fix: docker instructions
- 11587aed fix: dont close crdb for reuse purposes
- 560accee fix: fix hydra_client pk change mysql down migration (#2791)
- a5cc6eae fix: fix unbatched select in flushInactiveTokens
- b0196c04 fix: handle server error when refresh token requests come same time (#3207)
- 4bf995d2 fix: high db cpu utilisation on query (#3260)
- 8571a671 fix: hsm compile issues
- 668a3192 fix: ignore cypress screenshots in git
- 6c8dda86 fix: improve duration pattern
- 1bd0c523 fix: improve health check reporting
- ece5ca6a fix: improve jwk generator defaults
- 8cffc5b1 fix: improve lazy initialization of JWKs
- 1a4abd6d fix: improve migration status speed
- b32ff33f fix: improve time validation
- 255b4e22 fix: incorrect queries
- d65aa3a9 fix: lazy load PKI
- 72a5cd8c fix: lint issues
- 3a263854 fix: make servicelocator explicit
- c51b21bb fix: missing data in JWT grant (#3143)
- a364db4f fix: move to v0alpha2 api spec
- c56b9585 fix: mysql slice delete
- 1aa6cc43 fix: optimise sql update to avoid redundant writes (#3289)
- 3e7b6b41 fix: pop compile issue
- d6e7f94f fix: postgres migration script (#3249)
- e130dfa9 fix: prefix paths correctly with /admin
- 8b77f5ad fix: proper introspection output format (#3312)
- e58d3d15 fix: quickstart with SQLite
- 1d78e796 fix: regression in database layer
- 89941900 fix: remove deprecated config value
- e2c8809b fix: remove goswagger generated client
- 2a20080d fix: remove incorrect aliases
- e670d68d fix: remove obsolete type patches
- 13691d39 fix: remove unnecessary load of TLS certificates at boot
- 4ff0690d fix: remove unused swagger struct
- e1731baf fix: replace of consent session expires values
- acb16c1c fix: resolve a merge conflict in migration_test (#2811)
- f6ee1d3b fix: resolve conformance build issues
- 937e6baa fix: resolve internal SDK regressions
- 6eee09cc fix: resolve merge conflicts
- 5552e4df fix: resolve migration regressions
- 77b1ac74 fix: resolve test issues and regressions introduced by the new JWK generator
- 1fd6ea3d fix: resolve token prefix regression
- f0f3139e fix: retry transient crdb transaction failures
- f2daa7d6 fix: revert latest docker image changes (#3286)
- c9a248dd fix: revert to normal crdb
- eafa2bb4 fix: speed up health checks
- d746fa49 fix: support issuer with and without trailing slash
- 63a84de3 fix: update benchmark script
- 36ddb615 fix: use --yes flag in db-diff
- 9fbbbdf4 fix: use CreateWith
- 1d9891dc fix: use StringSliceJSONFormat instead of StringSlicePipeDelimiter (#3112)
- d1af32dc fix: use config func everywhere
- 3ceefd73 fix: use correct context
- aea37d6a fix: use correct sdk tag (#3318)
- 40022244 refactor(client): make OAuth2 Client IDs system-chosen and immutable
- 0752721d refactor(client): rename SDK methods and introduce
/adminprefix - 23585b57 refactor(client): replace limit and offset parameters with page_token and page_size
- 5885ab31 refactor(consent): rename SDK method from
acceptConsentRequesttoadminAcceptOAuth2ConsentRequest - fa27d0cf refactor(consent): rename SDK method from
acceptLoginRequesttoadminAcceptOAuth2LoginRequest - bb51ba0c refactor(consent): rename SDK method from
adminListSubjectConsentSessionstoadminListOAuth2SubjectConsentSessions - 9053040f refactor(consent): rename SDK method from
getLoginRequesttoadminGetOAuth2LoginRequest - 475efbcf refactor(consent): rename SDK method from
getOAuth2ConsentRequesttoadminGetOAuth2ConsentRequest - e0e3da9e refactor(consent): rename SDK method from
rejectConsentRequesttorejectOAuth2ConsentRequest - 37a8839f refactor(consent): rename SDK method from
rejectLoginRequesttorejectOAuth2LoginRequest - cdffa1e0 refactor(consent): rename SDK method from
rejectLogoutRequesttoadminRejectOAuth2LogoutRequest - 0a5ebe8f refactor(consent): rename SDK method from
revokeAuthenticationSessiontoadminRevokeOAuth2LoginSessions - 1108409a refactor(consent): rename SDK method from
revokeConsentSessionstoadminRevokeOAuth2ConsentSessions - 5e2ea0b6 refactor(jwk): no longer prefix keys with
publicorprivate - cd007bbb refactor(jwk): rename SDK methods and introduce
/adminprefix - c12b45cc refactor(oauth2): clean up changes
- ea4caf73 refactor(oauth2): rename SDK method from
deleteOAuth2TokentoadminDeleteOAuth2Token - df467a06 refactor(oauth2): rename SDK method from
discoverOpenIDConfigurationtodiscoverOidcConfiguration - f2bd9a30 refactor(oauth2): rename SDK method from
introspectOAuth2TokentoadminIntrospectOAuth2Token - 51b58e7e refactor(oauth2): rename SDK method from
oauth2TokentoperformOAuth2TokenFlow - 4e554e7a refactor(oauth2): rename SDK method from
userinfotogetOidcUserInfo - 06d565eb refactor(sdk): JSON Web Key SDK API
- b0a2b053 refactor(sdk): OAuth 2.0 Trust Relationship SDK
- 142b55f2 refactor(sdk): OAuth2 SDK API
- e800002d refactor(sdk): consent SDK
- a54ea697 refactor(sdk): rename PatchDocument to JsonPatchDocument
- 6b601564 refactor(sdk): rename errors
- cb742ad0 refactor(sdk): rename oauth2 client operations and payloads
- e0be7cfe refactor(trust): rename SDK method from
deleteTrustedJwtGrantIssuertoadminDeleteTrustedOAuth2JwtGrantIssuer - 210116e3 refactor(trust): rename SDK method from
getTrustedJwtGrantIssuertoadminGetTrustedOAuth2JwtGrantIssuer - cb7b9e00 refactor(trust): rename SDK method from
listTrustedJwtGrantIssuerstoadminListTrustedOAuth2JwtGrantIssuers - 7edf8df1 refactor(trust): rename SDK method from
trustJwtGrantIssuertoadminTrustOAuth2JwtGrantIssuer - 08bbbab1 refactor: CLI environment variables
HYDRA_URLhas been renamed toORY_SDK_URL - e466d7c9 refactor:
hydra keyscommand - 81e79f2a refactor:
hydra token clientcommand - aa338e17 refactor:
hydra token deletecommand - da3e2b44 refactor:
hydra token introspectcommand - 42e75c32 refactor:
hydra token revokecommand - 46b58874 refactor: deprecate
--dangerous-allow-insecure-redirect-urlflag - 062734e1 refactor: deprecate
--dangerous-force-httpflag - edb042e1 refactor: drop TLS by default
- 8023d2a7 refactor: environment variable
DATABASE_URLhas been deprecated - 53d225a9 refactor: finalize consent SDK methods
- 697813e1 refactor: generated UUID variant & version test (#2793)
- 53862f29 refactor: improve performance and reduce data use of consent persistence layer (#2836)
- cc9d9e5b refactor: make commands easier to consume
- 5fb3049e refactor: remove HS512 and HS256 jwk key generator
- 17c226cc refactor: remove
/oauth2/flushendpoint - 148cadb2 refactor: remove
oauth2.include_legacy_error_fieldsconfig - 223c8bc2 refactor: rename
access_logtorequest_log - 76eb93c3 refactor: rename
hydra clients createcommand - dea2fdd0 refactor: rename
hydra clients deletecommand - edd4b43d refactor: rename
hydra clients getcommand - 7de78410 refactor: rename
hydra clients importcommand - 1c0f971e refactor: rename
hydra clients listcommand - 7482b77c refactor: rename
hydra clients updatecommand - d2d55123 refactor: replace custom key generator with jose key generator
- f5d08853 test(conformance): add directory
- 580f33b1 test(conformity): revert admin prefix
- 15f3cfcb test(conformity): sdk regression
- fa239607 test(e2e): add trailing slash to issuer
- 415658d8 test(e2e): fix build instructions
- 03b23408 test(e2e): fix issuer URL
- 647822d7 test(e2e): fix jwt regression
- 30855d9e test(e2e): resolve test regressions
- 7bea2e8f test(e2e): respect metadata
- 40be7bb5 test(e2e): upgrade cypress
- 8ddf880c test(e2e): upgrade jwks-rsa
- 3420026a test(hsm): do not evaluate HSM private key
- 8db9e5bb test(hsm): resolve test issues
- 5e6c0995 test(migratest): add missing cockroach migrations and debug test failures
- b4865dd1 test: add test for access token strategy
- 51600f49 test: fix a flaky test
- 87105903 test: fix assertions on nil pointers
- 2875c190 test: fix conformity issues
- f979adb4 test: fix failing master pipeline (#3283)
- 2c4615ce test: fix flaky equal check
- 1100aba1 test: fix flaky equal check
- f0f5223a test: fix resp.bodyclose lint error
- 8a091750 test: implement network test structure for clients
- 3b7a1a75 test: improve jwk test layout
- 7b966515 test: refactor migration tests to use fixtures (#2936)
- 1cf5bd0f test: remove unused fixture
- 63b7303d test: resolve test migration issues
- 3a50926a test: test client update and double delete
- e77c0d35 test: update fixtures
- 549deda8 test: update paths to reflect new admin api
- 9e9ea946 test: update resource limits
- 1c9a0d2d test: update snapshot
- 5f5c81ea test: update snapshots
- 34bc743e test: update snapshots
- 01dbc0eb test: update snapshots
- c66a536a test: update snapshots
- 08968aa9 test: use fixed time.Now function in pop
- 34dfc0fe unstaged - refactor sdk use across the board
Artifacts can be verified with cosign using this public key.
Published by ory-bot about 2 years ago
This release resolves a critical regression introduced in Ory Hydra v1.11.9. Upgrade to this version and skip Ory Hydra v1.11.9 if you have an existing system. The bug can break existing refresh tokens from working.
It includes no other significant changes.
Bug Fixes
- Improve refresh webhook getter (d40b1da)
- Omit null lifespans (#3212) (2d080a0)
- Regression in session store (5c4321d)
- Remove special char from snapshot symbols (7128ad2)
- Revert config changes (4da64de)
- Session unmarshalling (3bb943a)
Code Generation
- Pin v1.11.10 release commit (1a6c220)
Changelog
- 75bdfc04 autogen(docs): generate and bump docs
- 40c8c2de autogen(docs): regenerate and update changelog
- e7faec91 autogen(docs): regenerate and update changelog
- 958895b8 autogen(docs): regenerate and update changelog
- 4b5cc903 autogen(docs): regenerate and update changelog
- e1bb9361 autogen(docs): regenerate and update changelog
- 1a6c2207 autogen: pin v1.11.10 release commit
- b3abc58d chore: update repository templates
- 3c0a6ec4 chore: update repository templates
- 2cee9e1a chore: update version schema to be compatible with current ory/cli (#3211)
- 5205a36b ci: pin go to 1.18
- 1d94bfda ci: workaround for linter issue
- d40b1daf fix: improve refresh webhook getter
- 2d080a01 fix: omit null lifespans (#3212)
- 5c4321d8 fix: regression in session store
- 7128ad2a fix: remove special char from snapshot symbols
- 4da64de7 fix: revert config changes
- 3bb943a9 fix: session unmarshalling
Artifacts can be verified with cosign using this public key.
Published by ory-bot about 2 years ago
☠️ WARNING ☠️
This version contains a regression which can cause the refresh flow to fail for existing consent sessions. Please do not upgrade to this version. For new systems, you can still use this version.
This release introduces two new features:
- The ability to specify token lifespans on a per-client basis using a new HTTP endpoint;
- The additional context in the refresh token hook.
Bug Fixes
-
Backport fix for client specific CORS (#1754) (#3163) (996258d)
-
docs: Correct the tracing service name environment variable (6e2343c):
While I believe this used to be specific to OTEL, it now appears to be
configurable "globally", according tospec/config.json. -
Fixed configuration editor for the documentation page (#3105) (0a77a06):
-
Handle server error when refresh token requests come same time (#3207) (e66ba3c)
-
Updated process ending instructions (#3176) (b72491e):
cmd + c doesn't end the process on macOS but ctrl + c does.
Code Generation
- Pin v1.11.9 release commit (8814e79)
Documentation
- Fix missing image (7925597)
Features
-
Add session and requester to refresh token webhook data (#3204) (6d23859), closes #3203
-
Add token_endpoint_auth_signing_alg to cli (#3148) (ed6eb30)
-
Custom client token ttl (#3206) (9544c03), closes #3157:
This change introduces a new endpoint that allows you to control how long client tokens last. Now you can configure the lifespan for each valid combination of Client, GrantType, and TokenType.
Changelog
- b0d672d1 autogen(docs): generate and bump docs
- 44b2c441 autogen(docs): regenerate and update changelog
- b62b21b4 autogen(docs): regenerate and update changelog
- b5af690a autogen(docs): regenerate and update changelog
- e586fd72 autogen(docs): regenerate and update changelog
- 3f962767 autogen(docs): regenerate and update changelog
- 9bc59be9 autogen(docs): regenerate and update changelog
- d0533c49 autogen(docs): regenerate and update changelog
- dd63a187 autogen(docs): regenerate and update changelog
- f0cb5390 autogen(openapi): regenerate swagger spec and internal client
- dbf1056c autogen(openapi): regenerate swagger spec and internal client
- 5c8350e4 autogen(openapi): regenerate swagger spec and internal client
- 8814e797 autogen: pin v1.11.9 release commit
- 5127bb77 autogen: pin v1.11.9-pre.0 release commit
- 540d9329 chore: delete semantic.yml
- ceada196 chore: deprecate coupon
- 1faa00b6 chore: display GitHub Action badge
- 87b20be6 chore: replace x/json.go with ory/x's jsonx patch (#3183)
- c9be891f chore: update repository templates
- fa87290a chore: update repository templates
- 88992d3a chore: update repository templates
- 6b954c22 chore: update repository templates
- 5a753234 chore: update repository templates
- 3fa88fcb chore: update repository templates
- f2f13470 chore: update repository templates
- 2a4ad740 chore: update repository templates
- fbde5001 chore: update repository templates
- 79255970 docs: fix missing image
- 6d238590 feat: add session and requester to refresh token webhook data (#3204)
- ed6eb301 feat: add token_endpoint_auth_signing_alg to cli (#3148)
- 9544c03a feat: custom client token ttl (#3206)
- 6e2343c6 fix(docs): correct the tracing service name environment variable
- 996258d5 fix: backport fix for client specific CORS (#1754) (#3163)
- 0a77a069 fix: fixed configuration editor for the documentation page (#3105)
- e66ba3c6 fix: handle server error when refresh token requests come same time (#3207)
- 17b517f3 fix: link OIDC Certification image (#3124)
- a383b5a6 fix: ping logic for SQL Registry (#3095)
- 9902ec73 fix: swagger for dynamic client registration (#3141)
- b72491ec fix: updated process ending instructions (#3176)
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 2 years ago
This release resolves issues in the log module, improves the SDK type definitions, and introduces new configuration options to HSM.
Bug Fixes
-
Add limit and offset to pagination (#3062) (51f6c5d), closes #3033
-
Do not use cached version (422d422)
-
Proper response types for 404 errors (#3072) (e711273), closes #3064
-
sdk: Correct polymorph type for consent session (#3074) (646459a), closes #3058
-
Sync ports between Dockerfiles and comments (#3027) (ebd1694)
-
Use default for env var (2b024b4)
Code Generation
- Pin v1.11.8 release commit (337ab3e)
Documentation
Features
-
Add hsm key set prefix to support multiple hydra instances on the same hsm partition (#3066) (90523fd):
This pull request adds configuration option
hsm.key_set_prefixto support multiple Ory Hydra instances to store keys on the same HSM partition. For example ifhsm.key_set_prefix=app1.then key sethydra.openid.id-tokenwould be generated/requested/deleted on HSM withCKA_LABEL=app1.hydra.openid.id-tokenThis will not affect Hydra API in any way.
GET /keys/hydra.openid.id-tokenwill return key set from HSM with labelapp1.hydra.openid.id-token. -
Add support for trust grants that can issue tokens for any subject (#3012) (a3c4304), closes #2930:
Previously, a trust relationship had to be setup for every subject
before the issuer could sign a JWT token for it. This change will allow
setting up token services that can issue tokens with any value in the
subject field. -
Make sensitive log value redaction text configurable (#3040) (536352c)
Tests
Changelog
- e06dd6ae autogen(docs): generate and bump docs
- b548c5ad autogen(docs): regenerate and update changelog
- 77394397 autogen(docs): regenerate and update changelog
- 152bdddd autogen(docs): regenerate and update changelog
- b00d2b9b autogen(docs): regenerate and update changelog
- f2bef45b autogen(docs): regenerate and update changelog
- 1f0e79ca autogen(docs): regenerate and update changelog
- fff64918 autogen(docs): regenerate and update changelog
- 8adbfb00 autogen(docs): regenerate and update changelog
- 48449f63 autogen(docs): regenerate and update changelog
- 924be24b autogen(docs): regenerate and update changelog
- f9338e4f autogen(docs): regenerate and update changelog
- a2afc759 autogen(docs): regenerate and update changelog
- 7d899635 autogen(docs): regenerate and update changelog
- e3236dd9 autogen(docs): regenerate and update changelog
- 05286df2 autogen(docs): regenerate and update changelog
- 835cb787 autogen(docs): regenerate and update changelog
- 1e4e3280 autogen(docs): regenerate and update changelog
- 1056795b autogen(docs): regenerate and update changelog
- 7602b4cc autogen(openapi): regenerate swagger spec and internal client
- b17b4743 autogen(openapi): regenerate swagger spec and internal client
- 22176486 autogen(openapi): regenerate swagger spec and internal client
- 23bc3e93 autogen(openapi): regenerate swagger spec and internal client
- 83c918a4 autogen: add v1.11.7 to version.schema.json
- 337ab3ec autogen: pin v1.11.8 release commit
- f06505f4 chore(deps): bump async from 2.6.2 to 2.6.4 in /test/e2e/oauth2-client (#3073)
- 57693f69 chore(deps): bump async from 3.2.0 to 3.2.3 (#3069)
- ff10e176 chore(deps): bump minimist from 1.2.5 to 1.2.6 (#3045)
- 57686719 chore(deps): bump minimist in /test/e2e/oauth2-client (#3047)
- 9eabc7dd chore(deps): update alpine version (#3036)
- 222a01ba chore: bump ory/fosite to v0.42.2 (#3077)
- 184d3222 chore: improve Dockerfiles (#3052)
- f3206734 chore: update repository templates
- 849af9f2 chore: update repository templates
- 980c2d84 docs: update README (#3032)
- c46f780f docs: update pricing
- 90523fd0 feat: add hsm key set prefix to support multiple hydra instances on the same hsm partition (#3066)
- a3c4304b feat: add support for trust grants that can issue tokens for any subject (#3012)
- 22e1ebb5 feat: async backchannel logout (#2849)
- 6dda48dc feat: backchannel request logging (#3067)
- 536352c1 feat: make sensitive log value redaction text configurable (#3040)
- 646459a5 fix(sdk): correct polymorph type for consent session (#3074)
- d654911c fix(sdk): incorrect title (#3014)
- 51f6c5d1 fix: add limit and offset to pagination (#3062)
- 00100a1b fix: add missing flags to config schema
- 3115dde2 fix: configure audit logger (#3022)
- 422d4227 fix: do not use cached version
- 270dbe08 fix: generated consent model (#3076)
- e711273e fix: proper response types for 404 errors (#3072)
- 1590542c fix: remove extraneous call to driver.init() (#3093)
- d4b2696b fix: remove unnecessary transaction (#3029)
- ebd16940 fix: sync ports between Dockerfiles and comments (#3027)
- 7d378f18 fix: typo README (#3078)
- 2b024b4f fix: use default for env var
- d38f6e62 test: ensure generator checks are executed (#3061)
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 2 years ago
Ory Hydra has a new place for documentation at github.com/ory/docs and www.ory.sh/docs/hydra! Additionally, the CI/CD infrastructure was moved to GitHub actions.
Code Generation
- Pin v1.11.7 release commit (510615b)
Changelog
- 510615bc autogen: pin v1.11.7 release commit
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 2 years ago
Ory Hydra has a new place for documentation at github.com/ory/docs and www.ory.sh/docs/hydra! Additionally, the CI/CD infrastructure was moved to GitHub actions.
Code Generation
- Pin v1.11.6 release commit (49d0d75)
Changelog
- 49d0d754 autogen: pin v1.11.6 release commit
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 2 years ago
Ory Hydra has a new place for documentation at github.com/ory/docs and www.ory.sh/docs/hydra! Additionally, the CI/CD infrastructure was moved to GitHub actions.
Code Generation
- Pin v1.11.5 release commit (743468e)
Changelog
- 743468ec autogen: pin v1.11.5 release commit
Artifacts can be verified with cosign using this public key.
Published by ory-bot over 2 years ago
autogen: pin v1.11.4 release commit
Bug Fixes
Code Generation
- Pin v1.11.4 release commit (9e731b6)
Changelog
- 3536a989 autogen(docs): regenerate and update changelog
- 0fa1a539 autogen(docs): regenerate and update changelog
- 39c82fc4 autogen(docs): regenerate and update changelog
- 950f25a5 autogen(docs): regenerate and update changelog
- 3659006e autogen(openapi): regenerate swagger spec and internal client
- 2c80bc64 autogen(openapi): regenerate swagger spec and internal client
- bad5b045 autogen(openapi): regenerate swagger spec and internal client
- 89a6a91a autogen(openapi): regenerate swagger spec and internal client
- 9e731b6e autogen: pin v1.11.4 release commit
- b00f5ec3 autogen: pin v1.11.4-pre.0 release commit
- 96798db8 autogen: pin v1.11.4-pre.1 release commit
- 8b1c967c autogen: pin v1.11.4-pre.2 release commit
- b768bb5a fix: pass swag-spec-location to sdk-release (#2994)
Artifacts can be verified with cosign using this public key.