
vuls
Agent-less vulnerability scanner for Linux, FreeBSD, Container, WordPress, Programming language libraries, Network devices
GPL-3.0 License
Bot releases are hidden (Show)
Published by shino 7 months ago
DONT USE THIS VERSION, SKIPPED
Published by MaineK00n 10 months ago
What's Changed
- fix(scanner/redhat): do not make cache when offline of redhat fast by @MaineK00n in https://github.com/future-architect/vuls/pull/1814
- chore(deps): bump dictionaries by @MaineK00n in https://github.com/future-architect/vuls/pull/1815
Full Changelog: https://github.com/future-architect/vuls/compare/v0.24.7...v0.24.8
Published by MaineK00n 10 months ago
What's Changed
- feat(os): add FreeBSD 14 EOL by @MaineK00n in https://github.com/future-architect/vuls/pull/1797
- chore(deps): bump github.com/gosnmp/gosnmp from 1.36.1 to 1.37.0 by @dependabot in https://github.com/future-architect/vuls/pull/1798
- chore(deps): bump golang.org/x/oauth2 from 0.14.0 to 0.15.0 by @dependabot in https://github.com/future-architect/vuls/pull/1799
- chore(deps): bump go-cve-dictionary to 0.10.0 by @MaineK00n in https://github.com/future-architect/vuls/pull/1803
- feat(models/nvd): group by source by @MaineK00n in https://github.com/future-architect/vuls/pull/1805
- fix(scanner/redhat): make cache before detect dnf modules by @wadda0714 in https://github.com/future-architect/vuls/pull/1812
Full Changelog: https://github.com/future-architect/vuls/compare/v0.24.6...v0.24.7
Published by MaineK00n 12 months ago
What's Changed
- chore(deps): update dictionary by @MaineK00n in https://github.com/future-architect/vuls/pull/1708
- chore(deps): bump github.com/CycloneDX/cyclonedx-go from 0.7.1 to 0.7.2 by @dependabot in https://github.com/future-architect/vuls/pull/1733
- chore(deps): bump github.com/package-url/packageurl-go from 0.1.1-0.20220203205134-d70459300c8a to 0.1.2 by @dependabot in https://github.com/future-architect/vuls/pull/1754
- feat(ubuntu): add ubuntu 23.10(mantic) by @MaineK00n in https://github.com/future-architect/vuls/pull/1750
- fix(scanner): change lsof cmd that should succeed without password by @MaineK00n in https://github.com/future-architect/vuls/pull/1769
- feat(scanner): revert lsof command for futurevuls users by @MaineK00n in https://github.com/future-architect/vuls/pull/1770
Full Changelog: https://github.com/future-architect/vuls/compare/v0.24.3...v0.24.4
Published by MaineK00n over 1 year ago
What's Changed
- chore(deps): bump github.com/Azure/azure-sdk-for-go from 66.0.0+incompatible to 68.0.0+incompatible by @dependabot in https://github.com/future-architect/vuls/pull/1588
- chore(deps): bump github.com/aws/aws-sdk-go from 1.44.136 to 1.44.249 by @dependabot in https://github.com/future-architect/vuls/pull/1656
- chore(deps): bump github.com/emersion/go-smtp from 0.14.0 to 0.16.0 by @dependabot in https://github.com/future-architect/vuls/pull/1580
- feat(ubuntu): add ubuntu 23.04 by @MaineK00n in https://github.com/future-architect/vuls/pull/1647
- chore(deps): bump github.com/spf13/cobra from 1.6.1 to 1.7.0 by @dependabot in https://github.com/future-architect/vuls/pull/1658
- chore(deps): bump go.etcd.io/bbolt from 1.3.6 to 1.3.7 by @dependabot in https://github.com/future-architect/vuls/pull/1657
- chore(deps): bump github.com/c-robinson/iplib from 1.0.3 to 1.0.6 by @dependabot in https://github.com/future-architect/vuls/pull/1659
- chore(deps): bump github.com/aws/aws-sdk-go from 1.44.249 to 1.44.251 by @dependabot in https://github.com/future-architect/vuls/pull/1660
- chore(deps): bump github.com/Ullaakut/nmap/v2 from 2.1.2-0.20210406060955-59a52fe80a4f to 2.2.2 by @dependabot in https://github.com/future-architect/vuls/pull/1665
- chore(deps): bump golang.org/x/oauth2 from 0.1.0 to 0.7.0 by @dependabot in https://github.com/future-architect/vuls/pull/1662
- chore(deps): bump github.com/CycloneDX/cyclonedx-go from 0.7.0 to 0.7.1 by @dependabot in https://github.com/future-architect/vuls/pull/1663
- fix(saas): remove current directory part by @MaineK00n in https://github.com/future-architect/vuls/pull/1666
- chore(deps): update goval-dictionary v0.8.3 by @MaineK00n in https://github.com/future-architect/vuls/pull/1671
- chore(deps): bump github.com/aws/aws-sdk-go from 1.44.251 to 1.44.254 by @dependabot in https://github.com/future-architect/vuls/pull/1669
- chore(deps): bump golang.org/x/sync from 0.1.0 to 0.2.0 by @dependabot in https://github.com/future-architect/vuls/pull/1673
- chore(deps): bump github.com/aws/aws-sdk-go from 1.44.254 to 1.44.259 by @dependabot in https://github.com/future-architect/vuls/pull/1672
- chore(deps): update dictionary tools, Vuls is now CGO free by @MaineK00n in https://github.com/future-architect/vuls/pull/1667
- test: sort []cveContent by CVEID by @MaineK00n in https://github.com/future-architect/vuls/pull/1674
Full Changelog: https://github.com/future-architect/vuls/compare/v0.23.1...v0.23.2
Published by MaineK00n over 1 year ago
What's Changed
- chore: update version for golangci-lint by @kl-sinclair in https://github.com/future-architect/vuls/pull/1586
- fix: add comment by @MaineK00n in https://github.com/future-architect/vuls/pull/1585
- feat(cwe): add cwe-id for category and view by @MaineK00n in https://github.com/future-architect/vuls/pull/1578
- fix(ubuntu): vulnerability detection for kernel package by @MaineK00n in https://github.com/future-architect/vuls/pull/1591
- fix(report): tidy dependencies for multiple repo on integration with GSA by @kl-sinclair in https://github.com/future-architect/vuls/pull/1593
- fix(ubuntu): dependency problem by @kl-sinclair in https://github.com/future-architect/vuls/pull/1597
- fix: use GetCveContentTypes instead of NewCveContentType by @MaineK00n in https://github.com/future-architect/vuls/pull/1603
- feat(detector/exploitdb): mod update and add more urls by @MaineK00n in https://github.com/future-architect/vuls/pull/1610
- style: fix typo by @MaineK00n in https://github.com/future-architect/vuls/pull/1592
- feat: update EOL by @MaineK00n in https://github.com/future-architect/vuls/pull/1598
Full Changelog: https://github.com/future-architect/vuls/compare/v0.22.0...v0.23.0-beta
Published by MaineK00n over 2 years ago
What's Changed
- feat: support server scan for suse with text/plain by @Nikkely in https://github.com/future-architect/vuls/pull/1433
- chore(deps): bump github.com/aquasecurity/trivy from 0.24.2 to 0.25.1 by @dependabot in https://github.com/future-architect/vuls/pull/1436
- chore: fix lint error by @MaineK00n in https://github.com/future-architect/vuls/pull/1438
- feat: parse OS version from result of trivy-scan by @Nikkely in https://github.com/future-architect/vuls/pull/1444
- feat(ubuntu): add Jammy Jellyfish(22.04) by @MaineK00n in https://github.com/future-architect/vuls/pull/1431
- chore(deps): bump github.com/aquasecurity/trivy from 0.25.4 to 0.27.0 by @dependabot in https://github.com/future-architect/vuls/pull/1451
- chore(deps): update goval-dictionary and gost by @MaineK00n in https://github.com/future-architect/vuls/pull/1452
Full Changelog: https://github.com/future-architect/vuls/compare/v0.19.5...v0.19.6
Published by MaineK00n over 2 years ago
What's new in v0.19.3
TL;DR
- Fedora support https://github.com/future-architect/vuls/pull/1367
- trivy v0.23.0 support https://github.com/future-architect/vuls/pull/1377
How it works
Vulnerable Fedora Environment Setup
Deliberately downgrade the mysql package so that FEDORA-MODULAR-2021-217f84c072 is detected.
- Dockerfile
FROM fedora:35
RUN dnf -y install openssh-server glibc-langpack-en
RUN mkdir /var/run/sshd
RUN sed -i 's/#\?PermitRootLogin prohibit-password/PermitRootLogin yes/' /etc/ssh/sshd_config
RUN sed -i 's@session\s*required\s*pam_loginuid.so@session optional pam_loginuid.so@g' /etc/pam.d/sshd
ENV NOTVISIBLE "in users profile"
RUN echo "export VISIBLE=now" >> /etc/profile
COPY .ssh/id_rsa.pub /root/authorized_keys
RUN mkdir ~/.ssh && \
mv ~/authorized_keys ~/.ssh/authorized_keys && \
chmod 0600 ~/.ssh/authorized_keys
RUN ssh-keygen -A
RUN rm -rf /run/nologin
EXPOSE 22
# Vuls Setting
RUN dnf -y install dnf-utils which lsof iproute
# FEDORA-MODULAR-2021-217f84c072
RUN dnf module install -y mysql && dnf downgrade -y mysql
CMD ["/usr/sbin/sshd", "-D"]
check community-mysql package version
$ docker build -t vuls-target -f Dockerfile .
$ docker run --rm -itd -p 2222:22 vuls-target
$ ssh -i ~/.ssh/id_rsa -p 2222 [email protected]
[root@615d6b9247ec /]# cat /etc/fedora-release
Fedora release 35 (Thirty Five)
[root@615d6b9247ec /]# rpm -qa | grep community-mysql
community-mysql-common-8.0.26-1.module_f35+12627+b26747dd.x86_64
community-mysql-8.0.26-1.module_f35+12627+b26747dd.x86_64
community-mysql-errmsg-8.0.26-1.module_f35+12627+b26747dd.x86_64
community-mysql-server-8.0.26-1.module_f35+12627+b26747dd.x86_64
Vulnerability Detection (dnf updateinfo --security vs vuls report)
dnf updateinfo --security
The mysql package we just installed is a modular package, so the advisory starting with FEDORA-MODULAR- should be presented.
However, the actual advisory provided relates to a non-modular package of the same name.
[root@615d6b9247ec /]# dnf updateinfo --security --info
Last metadata expiration check: 0:02:24 ago on Thu Feb 3 04:47:52 2022.
===============================================================================
community-mysql-8.0.27-1.fc35
===============================================================================
Update ID: FEDORA-2021-46dc82116b
Type: security
Updated: 2021-11-10 02:52:52
Bugs: 2015421 - community-mysql-8.0.27 is available
: 2016141 - CVE-2021-2478 CVE-2021-2479 CVE-2021-2481 CVE-2021-35546 CVE-2021-35575 CVE-2021-35577 CVE-2021-35591 CVE-2021-35596 CVE-2021-35597 CVE-2021-35602 CVE-2021-35604 CVE-2021-35607 CVE-2021-35608 CVE-2021-35610 ... community-mysql: various flaws [fedora-all]
Description: **MySQL 8.0.27**
:
: Release notes:
:
: https://dev.mysql.com/doc/relnotes/mysql/8.0/en/news-8-0-27.html
Severity: Moderate
vuls
vuls report
FixedIn is displayed correctly as module to module!
$ vuls report --format-full-text
...
+----------------+----------------------------------------------------------------------------------+
| CVE-2021-35610 | FIXED |
+----------------+----------------------------------------------------------------------------------+
| Max Score | 7.1 MODERATE (redhat_api) |
| redhat_api | 7.1/CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:H MODERATE |
| nvd | 7.1/CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:H HIGH |
| jvn | 7.1/CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:H HIGH |
| Vendor | 4.0-6.9 MODERATE |
| nvd | 5.5/AV:N/AC:L/Au:S/C:N/I:P/A:P MEDIUM |
| jvn | 5.5/AV:N/AC:L/Au:S/C:N/I:P/A:P MEDIUM |
| Summary | **MySQL 8.0.27** Release notes: |
| | https://dev.mysql.com/doc/relnotes/mysql/8.0/en/news-8-0-27.html |
| Primary Src | https://www.oracle.com/security-alerts/cpuoct2021.html |
| Primary Src | https://nvd.nist.gov/vuln/detail/CVE-2021-35610 |
| Primary Src | https://bodhi.fedoraproject.org/updates/FEDORA-MODULAR-2021-217f84c072 |
| Patch | https://www.oracle.com/security-alerts/cpuoct2021.html |
| Affected Pkg | community-mysql-8.0.26-1.module_f35+12627+b26747dd |
| | -> 8.0.27-1.module_f35+13269+c9322734 (FixedIn: |
| | 0:8.0.27-1.module_f35+13269+c9322734) (updates-modular) |
| Affected Pkg | community-mysql-common-8.0.26-1.module_f35+12627+b26747dd |
| | -> 8.0.27-1.module_f35+13269+c9322734 (FixedIn: |
| | 0:8.0.27-1.module_f35+13269+c9322734) (updates-modular) |
| Affected Pkg | community-mysql-errmsg-8.0.26-1.module_f35+12627+b26747dd |
| | -> 8.0.27-1.module_f35+13269+c9322734 (FixedIn: |
| | 0:8.0.27-1.module_f35+13269+c9322734) (updates-modular) |
| Affected Pkg | community-mysql-server-8.0.26-1.module_f35+12627+b26747dd |
| | -> 8.0.27-1.module_f35+13269+c9322734 (FixedIn: |
| | 0:8.0.27-1.module_f35+13269+c9322734) (updates-modular) |
| Confidence | 100 / OvalMatch |
| CWE | NVD-CWE-noinfo: (nvd) |
| CWE | https://cwe.mitre.org/data/definitions/NVD-CWE-noinfo.html |
+----------------+----------------------------------------------------------------------------------+
...
vuls tui
Looking at the TUI, we have succeeded in getting the advisory we really want: FEDORA-MODULAR-2021-217f84c072!

What's Changed
- chore: update git submodule for integration test by @kotakanbe in https://github.com/future-architect/vuls/pull/1364
- fix(scanner/base) export libFile struct by @sadayuki-matsuno in https://github.com/future-architect/vuls/pull/1365
- fix(scanner/base) export libFile fields by @sadayuki-matsuno in https://github.com/future-architect/vuls/pull/1366
- feat(libscan): support trivy v0.23.0 by @kotakanbe in https://github.com/future-architect/vuls/pull/1377
- fix(oval): fix query in PostgreSQL by @MaineK00n in https://github.com/future-architect/vuls/pull/1372
- feat(alpine): add Alpine 3.14, 3.15 EOL by @MaineK00n in https://github.com/future-architect/vuls/pull/1359
- fix(gost): add nil check by @MaineK00n in https://github.com/future-architect/vuls/pull/1379
- fix(centos): identify CentOS and CentOS Stream by @MaineK00n in https://github.com/future-architect/vuls/pull/1360
- feat(fedora): support fedora by @maito1201 in https://github.com/future-architect/vuls/pull/1367
- chore(oval): update mod by @MaineK00n in https://github.com/future-architect/vuls/pull/1385
New Contributors
- @maito1201 made their first contribution in https://github.com/future-architect/vuls/pull/1367
Full Changelog: https://github.com/future-architect/vuls/compare/v0.19.2...v0.19.3
Published by kotakanbe over 4 years ago
- Container image scanning has been deprecated since v0.9.5 (#971 ).
- Fixed some bugs.
https://github.com/future-architect/vuls/compare/v0.9.4...v0.9.5
Published by kotakanbe over 4 years ago
Fixed some bugs.
https://github.com/future-architect/vuls/compare/v0.9.3...v0.9.4
Published by kotakanbe over 4 years ago
https://github.com/future-architect/vuls/compare/v0.9.2...v0.9.3
feat(report): display "fixed" when updatable even in fast mode #957
https://github.com/future-architect/vuls/pull/957
Ubuntu18 (fast scan mode)
-
before

-
after

Debian9 (fast scan mode)
- before

-after

fix(report): kernel vulns detection BUG in Ubuntu #958
OVAL for Ubuntu has been changed. The kernel used to be described as linux-image-*, but the -image- has been removed. ex: changed linux-image-aws to linux-aws.
For this reason, the detection logic was changed.
Published by kotakanbe over 4 years ago
Display fixed-in version for each package in report
TUI

Report

JSON
fixedIn is added to affectedPackages.
"CVE-2016-9840": {
"cveID": "CVE-2016-9840",
"confidences": [
{
"score": 100,
"detectionMethod": "OvalMatch"
}
],
"affectedPackages": [
{
"name": "rsync",
"fixedIn": "3.1.2-2.1ubuntu1.1"
}
],
Published by kotakanbe about 5 years ago
You need to rm cve.sqlite3 and re-fetch NVD (and JVN) database.
Go v1.13 or later is needed to compile https://github.com/future-architect/vuls/issues/903
Changelog
3ffed18 Change GPL v3 to AGPL v3 because of aquasecurity/trivy dependency (#897)
f54e725 fix(report): fill cert alerts from NVD and JVN feeds (#899)
cc13b6a fix(report): enable to report without NVD, exit if no OVAL data (#900)
8877db1 udpate deps, go 1.13 (#901)
af58122 for Amazon Linux image (#896)
b7ca5e5 feat(scan): add -wordpress-only and -libs-only flag (#898)
69b6d87 scanVuln => GetScanResults and writeScanResults (#891)
1fbd516 fix(report): fix too many variables while reporting (#888)
dec5d3b No warning(s) in the output file with -quiet option. Report command (#885)
d5e2040 awk is useless because ps already formats the output. Also, this syntaxe isn't correct when the command is excuted on a container because of the ' . (#883)
4326bef Allow Offline scanning on Alpine (#877)
Published by kotakanbe about 5 years ago
Changelog
3d4a5d9 fix(report): Unsupport family: centos (#876)
Published by kotakanbe over 5 years ago
Changelog
d770034 fix centos yum makecache --assumeyes (#872)
a977533 Fix performance and bug (#867)
c5e13dd fix(configtest): remove yum-plugin-ps check on Amazon Linux (#870)
a8040fe fix(wordpress): add --allow-root to wp cmd for docker based wp (#865)
9e06600 fix go module problems & update trivy version (#864)
22c6601 make fmt
425464f fix(scan): allow exit 1 for no match lsof | grep (#863)
ccb0751 fix(scan): show listening ip:port of procs (#862)
f832de8 feat(saas): log.info done after uploading
8a37de0 Add ips flag to scan (#861)
Published by kotakanbe over 5 years ago
Changelog
836e470 feat(scan): Display listen port of affected procs for each vulnerable pkgs (#859)
3e53903 feat(redhat): ignore will not fix vulns (#858)
f8c0b38 feat(fast-root): get running procs for each pkgs (all RHEL, CentOS, AmazonLinux, Ubuntu, Debian) (#855)
65e6070 Fix race condition in server mode (#857)
7b78ebb retrieve ips(deep security) identifiers (#852)
Published by kotakanbe over 5 years ago
Changelog
03c3189 Changes don't required config.toml in server mode (#853)
Published by kotakanbe over 5 years ago
New features
Support Amazon Linux in server mode
#850
Conent-Type: text/plain
$ ./vuls server -listen 0.0.0.0:5515 -format-json
# test amazon linux 1
$ docker run -it --rm amazonlinux:2016.09.0.20161028 /bin/bash
$ curl -X POST -H "X-Vuls-Server-Name: local" -H "Content-Type: text/plain" -H "X-Vuls-OS-Family: amazon" -H "X-Vuls-OS-Release: 2 (Karoo)" -H "X-Vuls-Kernel-Release: 4.9.125-linuxkit" --data-binary "`rpm -qa --queryformat "%{NAME} %{EPOCHNUM} %{VERSION} %{RELEASE} %{ARCH}\n"`" http://${HOST_IP}:5515/vuls
# test amazon linux 2
$ docker run -it --rm amazonlinux:2.0.20190508 /bin/bash
$ curl -X POST -H "X-Vuls-Server-Name: local" -H "Content-Type: text/plain" -H "X-Vuls-OS-Family: amazon" -H "X-Vuls-OS-Release: 2016.09" -H "X-Vuls-Kernel-Release: 4.9.125-linuxkit" --data-binary "`rpm -qa --queryformat "%{NAME} %{EPOCHNUM} %{VERSION} %{RELEASE} %{ARCH}\n"`" http://${HOST_IP}:5515/vuls
# test ec2 amazon linux2
$ curl -X POST -H "X-Vuls-Server-Name: local" -H "Content-Type: text/plain" -H "X-Vuls-OS-Family: amazon" -H "X-Vuls-OS-Release: 2 (Karoo)" -H "X-Vuls-Kernel-Release: 4.14.121-109.96.amzn2.x86_64" --data-binary "`rpm -qa --queryformat "%{NAME} %{EPOCHNUM} %{VERSION} %{RELEASE} %{ARCH}\n"`" http://${HOST_IP}:5515/vuls
Content-Type: application/json
$ ./vuls server -listen 0.0.0.0:5515 -to-localfile -format-json
$ curl -X POST -H "Content-Type: application/json" -d '{"Family": "amazon", "Release": "2 (Karoo)", "RunningKernel": {"Release": "4.14.121-109.96.amzn2.x86_64", "Version": ""}, "Packages": {"kernel": {"Name": "kernel", "Version": "4.14.114", "Release": "105.126.amzn2", "Arch": "x86_64"}, "dracut": {"Name": "dracut", "Version": "033", "Release": "535.amzn2.1.2", "Arch": "x86_64"}}}' http://localhost:5515/vuls
Changelog
4a34dfe Support amazonlinux via http text/plain (#850)
Published by kotakanbe over 5 years ago
Vulsrepo GitHub issue moved
GitHub issue of usiusi360 no more available.
If you find a issue of usiusi360/vulsrepo, add it to future-architect/vuls.
How to Update to v0.8.0
Update Go
Go over v1.12 needed.
Compile error will be occurred with Go under v11.
update and re-fetch with a new database
- goval-dictionary
- go-cve-dictinoary
- Vuls
New features
Container Image Scan
https://github.com/future-architect/vuls/pull/829
[servers]
[servers.image]
type="pseudo"
# GCR
[servers.image.images.hyperkube]
name="gcr.io/google-containers/hyperkube"
tag="v1.11.10"
# Local
[servers.image.images.web-dvwa]
name="vulnerables/web-dvwa"
tag="latest"
# Local
[servers.image.images.gcr]
name="asia.gcr.io/bizshift-stg/api"
tag="latest"
[servers.image.images.gcr.dockerOption]
gcpCredPath="/Users/amachi/Downloads/key.json"
Smart Programming Language Library Scan
https://github.com/future-architect/vuls/pull/829
[servers]
[servers.abuntu]
host = "xxx.xxx.xxx"
port = "22"
user = "tamachi"
keyPath = "/Users/amachi/.ssh/id_dsa"
findLock = true # auto detect lockfile
lockfiles = [
"/home/tamachi/lockfiles/package-lock.json"
"/home/tamachi/lockfiles/yarn.lock"
]
Speed up Oval Reporting
https://github.com/future-architect/vuls/pull/834
| os | before | after |
|---|---|---|
| alpine3.9 | over 1hour | 0.26s |
| Ubuntu | 180s | 3s |
Support Amazon OVAL Scan
https://github.com/future-architect/vuls/pull/824
Support OVAL scanning for Amazon Linux 1/2.
You should update to the latest version of goval-dictionary and fetch-amazon
$ goval-dictionary fetch-amazon
see also
- https://github.com/kotakanbe/goval-dictionary/pull/63
- https://github.com/kotakanbe/goval-dictionary#usage-fetch-amazon-alas-as-oval-data-type
Support RHEL8
You have to fetch RedHat OVAL before reporting.
To fetch
$ goval-dictionary fetch-redhat 5 6 7 8
see
- https://github.com/kotakanbe/goval-dictionary#usage-fetch-oval-data-from-redhat
- https://github.com/future-architect/vuls/pull/813
Bug Fix
- fix(scan): false negative of kernel related vulns on Ubuntu 16 #819
- fix(scan): a bug of kernel Vulns detection on Ubuntu18
- fix(report): Critical Bug Fix for CPE based scanning
- fix(report): fix the number of fixed/total in reporting
Changelog
4cf9a72 set GO111MODULE=on in .goreleaser.yml
bd1b135 Add vulsrepo issue template
8c3b305 fix(readme): typo in news (#841)
a371903 fix(scan): scan Amazon Linux with offline mode (#840)
c68a261 Update README.md
75fea79 feat(scan): Support RHEL8 (#813)
eb9f968 refactor(scan): remove yum-security related code (#836)
3634afd enhance issue_template (#837)
77b5df8 update goval-dictionary dependency to valid version (#839)
b81f640 fix(report): remove extra check logic #802 (#835)
a8a90d7 refactor(report): speed up oval reporting #833 (#834)
17bb575 fix(scan): enable to report if some warnings occured on scanning (#805)
abcea1a add Library Scan (with image scan) (#829)
10942f7 fix(scan): fetch only updatable package changelogs (#815)
87ee829 fix(scan): exec yum makecache to update metadata on RedHat based linux (#810)
fcc2c1e Changing the scannedAt time in the original result (#823)
269095d feat(report): support Amazon OVAL scanning (#824)
40492ee fix typos, extraneous text (#831)
64cdd5a fix(report): WordPress(WPVULNDB API) 429 Too Many Requests (#826)
3bb650c fix(report-redhat): fix false negative of affected vulns #827 (#828)
774544c fix(report): warning only if the kernel version is unknown (#822)
299805a [WIP]fix(scan): false negative of kernel related vulns on Ubuntu 16 (#819)
276363e fix(scan): a bug of kernel Vulns detection on Ubuntu18 (#818)
e750bd5 fix(report): fix the number of fixed/total in reporting (#817)
98fee7b Implement Vuls's own error code (#812)
53aaea9 add scannedVia field to know the way of access such as SSH, local or pseudo (#811)
824fbb6 Updated config.toml reference url (#809)
80566b9 fix(report): exit 1 when scan result has errors (#804)
533d05a fix(report): Error when GitHub integration failed (#800)
Published by kotakanbe over 5 years ago
New Features
WordPress Vulnerability Scan (core, plugin, theme)
For non-commercial use, you can use this WordPress integration for free.
But for commercial use, You have to send a E-Mail to the WPVulnDB team.
For Details, see the NOTE:
If you are under any doubt if your software is classed as non-commercial and/or would like to inquire about commercial usage of our databases get in touch.
First, you need to register a user and get the API token from your profile page on wpvulndb.com.
And then, check whether the wp command is insatalled on the scan target server.
A sample configuration is below.
- config.toml
[servers.kusanagi]
user = "root"
host = "10.10.10.10"
port = "22"
[servers.kusanagi.wordpress]
cmdPath = "/usr/local/bin/wp"
osUser = "wordpress"
docRoot = "/home/kusanagi/wp/DocumentRoot/"
wpVulnDBToken = "xxxxTokenxxxx"
ignoreInactive = false
- cmdPath: A path of
wp-clion the WordPress server - osUser: A OS user of
wp-clion the WordPress server - docRoot: A path of document root on the WordPress server
- wpVulnDBToken: A token of WPVULNDB API
- ignoreInactive: Ignore plugins or themes which are inactive state
Scan
To scan WordPress, execute as below.
$ vuls scan kusanagi
Vuls collects WordPrss Core version, plugins and themes via wp-cli.
Reporting
$ vuls report
Vuls detects vulnerabilities via accessing WPVulnDB.com via HTTP.
- Slack


- TUI

- Full-Text
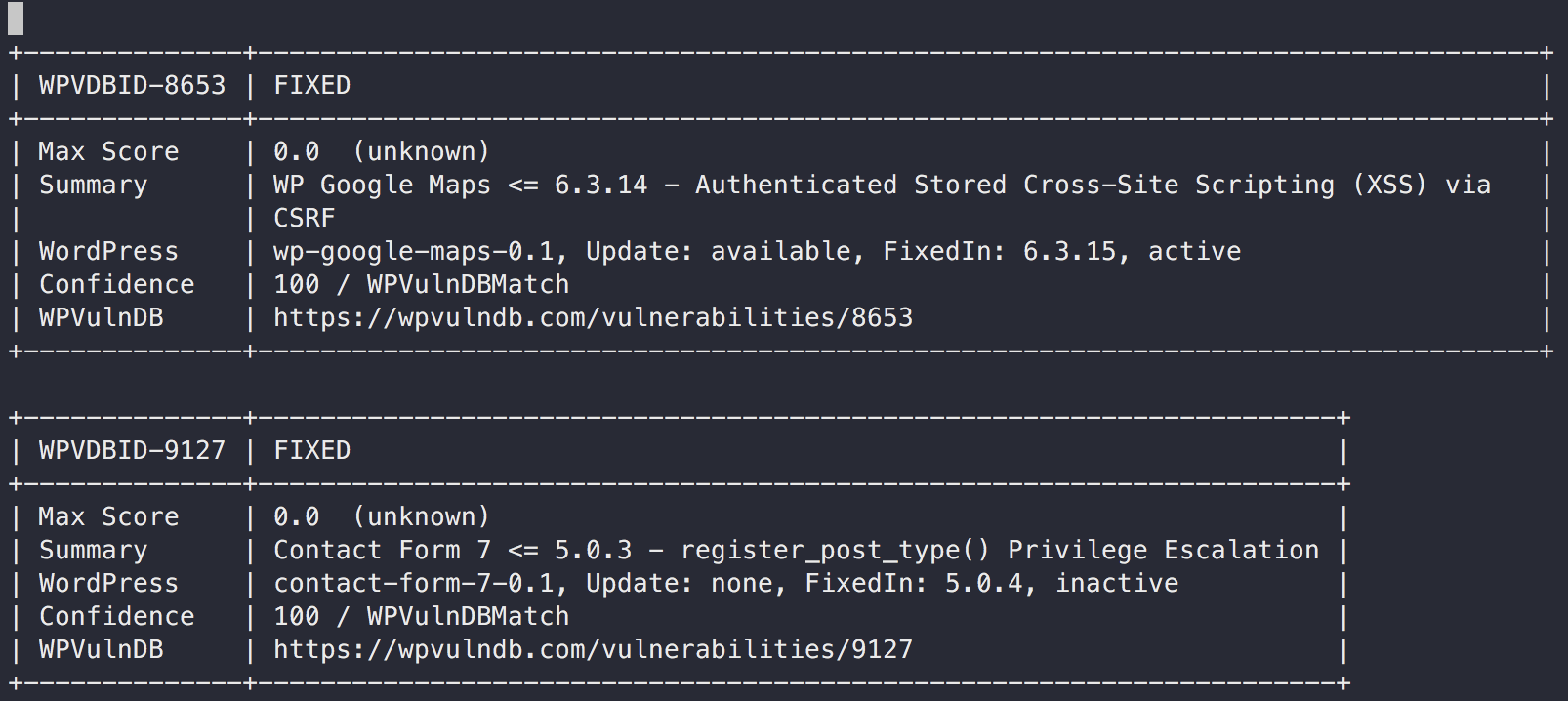
Changelog
6a1fc4f Merge branch 'master' of https://github.com/future-architect/vuls
9008d0d Add news to readme
583f457 fix goreleaser.yml
e5716d5 Add news to readme
7192ae1 Bump up version
99c65ef feat(scan): WordPress Vulnerability Scan (core, plugin, theme) (#769)
91df593 Editorial fixes (#798)
07aeaeb update go-exploitdb (#797)
cfeecda update pkgs (#796)
564dfa8 update cve dictionary (#795)
75dd6f2 Specify VOLUME using json syntax (#791)
e26fd0b fix(report): Critical Bug Fix for CPE based scanning #793 (#794)
d630680 feat(slack): enable -format-one-line-text with -to-slack (#792)
1723c3f fix(report): cpe match bug: go-cve-dictionary#120 (#790)
53dd903 fix(scan): parse error on SUSE #515 (#786)
5c6e06b Handle no-auth SMTP Servers and one liner email fix (#772)
cf6fb0c models: fix no-op append calls (#785)
e0e71b2 add scanner info in -to-saas (#783)
53f4a29 change implemention of integration (#780)



